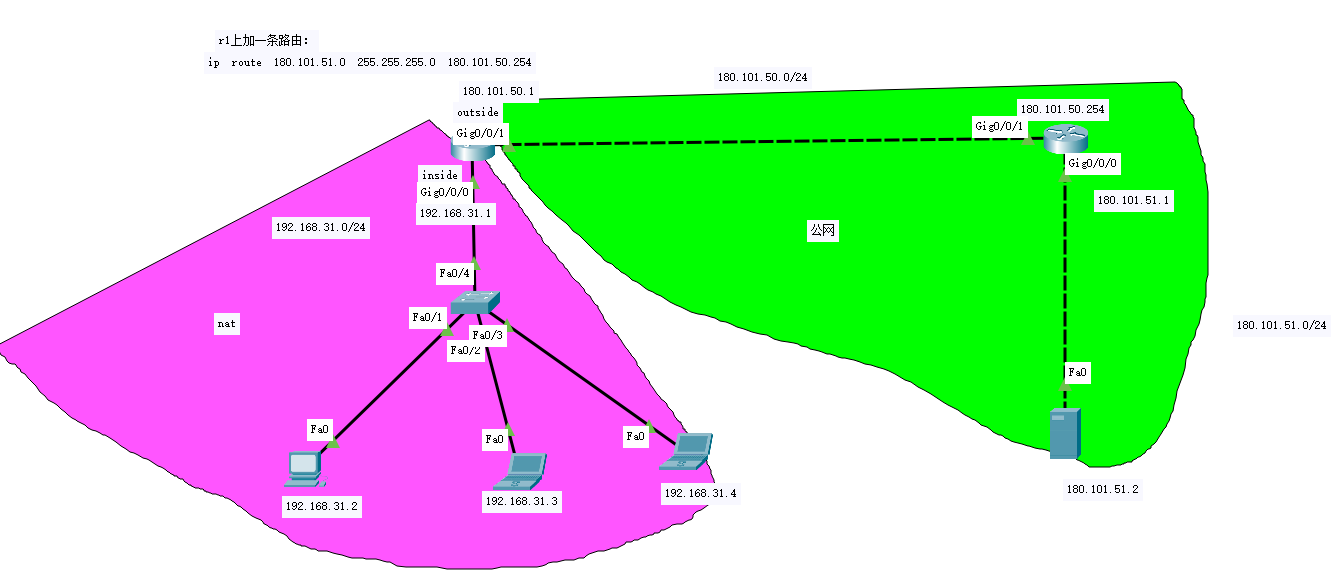
再看网络
NAT
三种方式:
-
静态转换Static Nat
-
动态转换Dynamic Nat
-
端口多路复用OverLoad
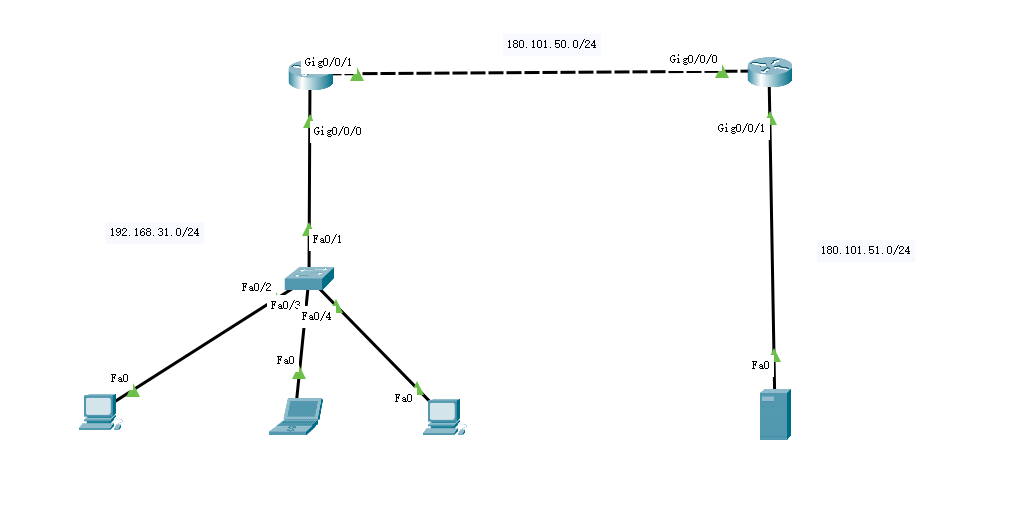
eNSP或者cisco实验(这里使用cisco):
-
静态转换Static Nat
R-1(config)#ip nat pool fpc 180.101.50.100 180.101.50.200 netmask 255.255.255.0 #声明一个nat地址池 R-1(config)#ip nat inside source static 192.168.31.2 180.101.50.100 #在地址池选一个ip,对终端做ip映射:内侧192.168.31.2的终端ip映射成180.101.50.100 R-1(config)#ip nat outside source static 180.101.50.100 192.168.31.2 #对外侧180.101.50.100的路由器接口ip映射成191.168.31.2
R-1(config)#int g0/0/0 #路由器接口g/0/0是内侧 R-1(config-if)#ip nat inside R-1(config-if)#exit R-1(config)#int g0/0/1 #路由器接口g0/0/1是外侧 R-1(config-if)#ip nat outside
R-1# show ip nat statistics #查看接口配置
Total translations: 2 (1 static, 1 dynamic, 0 extended)
Outside Interfaces: GigabitEthernet0/0/1
Inside Interfaces: GigabitEthernet0/0/0
R-1# show ip nat translations #查看nat配置,inside global 内部公网ip,inside local 内部私网ip ,outside local 外部私网ip, outside global 外部公网ip
Pro Inside global Inside local Outside local Outside global
--- 180.101.50.100 192.168.31.2 --- ---
--- --- --- 192.168.31.2 180.101.50.100
-
动态转换Dynamic Nat
Router(config)#ip nat pool fpc 180.101.50.100 180.101.50.200 netmask 255.255.255.0 #声明一个nat地址池
Router#access-list 1 permit 192.168.31.0 0.0.31.255 ip nat inside source list 1 pool fpc int g0/0 ip nat inside exit int g0/1 ip nat outside
Router#show ip nat statistics
Total translations: 8 (0 static, 8 dynamic, 8 extended)
Outside Interfaces: GigabitEthernet0/0/1
Inside Interfaces: GigabitEthernet0/0/0
Hits: 8 Misses: 10
Expired translations: 2
Dynamic mappings:
-- Inside Source
access-list 1 pool fpc refCount 8
pool fpc: netmask 255.255.255.0
start 180.101.50.100 end 180.101.50.200
type generic, total addresses 101 , allocated 1 (0%), misses 0
Router#
Router#show ip nat translations
Pro Inside global Inside local Outside local Outside global # 每次ping都不一样,随机从池中获取ip映射
icmp 180.101.50.100:10 192.168.31.2:10 180.101.51.2:10 180.101.51.2:10
icmp 180.101.50.100:3 192.168.31.2:3 180.101.51.2:3 180.101.51.2:3
icmp 180.101.50.100:4 192.168.31.2:4 180.101.51.2:4 180.101.51.2:4
icmp 180.101.50.100:5 192.168.31.2:5 180.101.51.2:5 180.101.51.2:5
icmp 180.101.50.100:6 192.168.31.2:6 180.101.51.2:6 180.101.51.2:6
icmp 180.101.50.100:7 192.168.31.2:7 180.101.51.2:7 180.101.51.2:7
icmp 180.101.50.100:8 192.168.31.2:8 180.101.51.2:8 180.101.51.2:8
icmp 180.101.50.100:9 192.168.31.2:9 180.101.51.2:9 180.101.51.2:9
总而言之,去SNAT,回DNAT PAT(端口映射):去DNAT,回SNAT
vlan与交换 trunck技术(路由器成本昂贵,vlan是很好的替代品)
vlan:虚拟局域网技术,可以从逻辑上将将一个大的网络划分若干小的局域网,从而达到控制广播流量的效果。
交换机的泛洪流量在虚拟局域网内进行 ---> 默认是VLAN1
拆分广播域,切割局域网方式:
1、路由(路由器价格昂贵)
2、子网掩码,划分不同的子网,不同子网间不能通信,但是还可以发送广播
3、vlan,主要是控制广播泛洪,2、安全性 虚拟局域网(vlan)之间由二层上升到三层通信,间接通信
- 在局域网,网络规模不断的扩大,接入的主机以及设备会越来越多,在这种情况下,网络中的广播流量越来越大,于是会加重交换机的负担,消耗交换机的cpu,内存等,甚至造成交换机的死机。
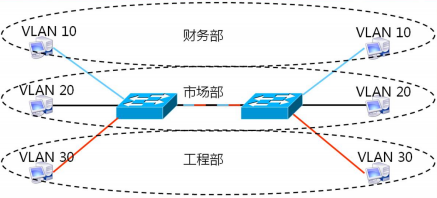
在vlan技术中,只有同一vlan内的端口内的主机才可以进行通信,不同vlan端口之间不能直接通信访问。因此vlan可以限制个别主机访问服务器资源,这样可以提高局域网络的安全性。
VPN技术