APP实战:海博TV
登录进去发现有ROOT检测,虽然不会影响我们的登录,但是能绕过就绕过好了
ROOT函数定位
直接去定位Toast
var Toast =Java.use("android.widget.Toast");
Toast.show.implementation = function(){
showstack();
console.log("Toast.show.implementation");
return this.show();
}
result:
[Pixel XL::com.hoge.android.app.fujian]-> java.lang.Throwable
at android.widget.Toast.show(Native Method)
at com.hoge.android.util.CustomToast.showToast(CustomToast.java:172)
at com.hoge.android.util.CustomToast.showToast(CustomToast.java:134)
at com.hoge.android.util.CustomToast.showToast(CustomToast.java:99)
at com.hoge.android.factory.welcome.WelcomeActivity$2$1.run(WelcomeActivity.java:260)
at android.os.Handler.handleCallback(Handler.java:883)
at android.os.Handler.dispatchMessage(Handler.java:100)
at android.os.Looper.loop(Looper.java:214)
at android.app.ActivityThread.main(ActivityThread.java:7356)
at java.lang.reflect.Method.invoke(Native Method)
at com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
函数定位到
com.hoge.android.factory.welcome.WelcomeActivity$2$1.run
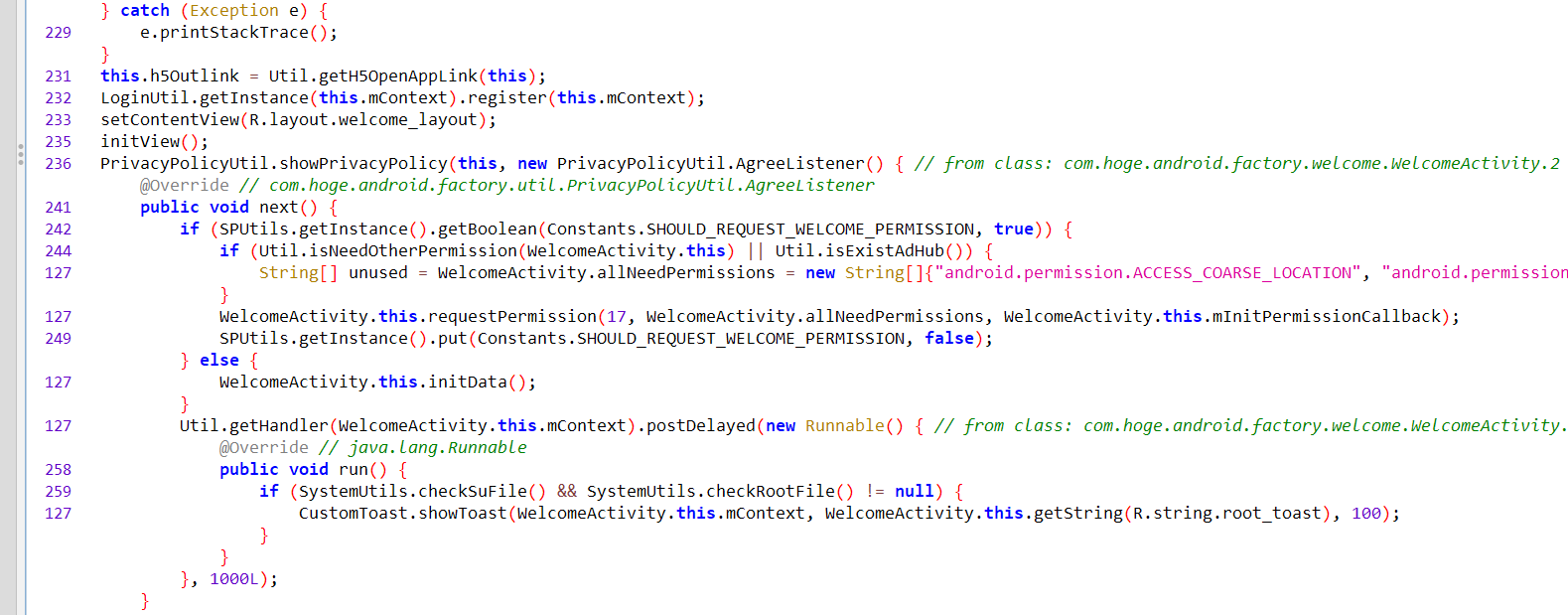
public void run() {
if (SystemUtils.checkSuFile() && SystemUtils.checkRootFile() != null) {
CustomToast.showToast(WelcomeActivity.this.mContext, WelcomeActivity.this.getString(R.string.root_toast), 100);
} }
R.string.root_toast这个值在jeb里面的资源表里面的String类可以看到就是ROOT设备的提示语
过Root检测
这里有两个Root检测的函数,
一个是在命令行中执行 which su 找到对应root权限的路径
new BufferedReader(new InputStreamReader(process.getInputStream())).readLine() 读取对应的可能得到的路径
假如能够读出来,就说明有root权限
public static boolean checkSuFile() {
Process process = null;
try {
process = Runtime.getRuntime().exec(new String[]{"which", "su"});
if (new BufferedReader(new InputStreamReader(process.getInputStream())).readLine() != null) {
if (process != null) {
process.destroy();
}
return true;
}
if (process != null) {
process.destroy();
}
return false;
} catch (Throwable th) {
if (process != null) {
process.destroy();
}
throw th;
}
}
这里的ROOT检测就是直接去执行对应路径的命令,查看有权限
public static File checkRootFile() {
String[] strArr = {"/sbin/su", "/system/bin/su", "/system/xbin/su", "/data/local/xbin/su", "/data/local/bin/su", "/system/sd/xbin/su", "/system/bin/failsafe/su", "/data/local/su"};
int length = strArr.length;
File file = null;
int i = 0;
while (i < length) {
File file2 = new File(strArr[i]);
if (file2.exists()) {
return file2;
}
i++;
file = file2;
}
return file;
}
绕过:
var SystemUtils = Java.use("com.hoge.android.factory.util.system.SystemUtils");
SystemUtils.checkSuFile.implementation=function()
{
var result = this.checkSuFile();
console.log(result);
return false;
}//第二个函数其实也是看第一个函数的返回值
登录逆向
这里的函数定位还是需要定位很久的,这里面有证书检测,抓包会崩溃,先HOOK掉证书检测,再来抓包,上一篇里面有绕过证书检测的代码的。
先来看看抓包的结果:
POST /api/v1/m_login.php?app_version=4.0.0&phone_models=PixelXL&client_id_android=34431799b51eaf57b3def0720642215b&language=Chinese&client_type=android&version=4.0.0&locating_city=%E7%A6%8F%E5%B7%9E&system_version=10&appid=9&device_token=1684ff905e7ad010a30421164d44e3f9&location_city=%E7%A6%8F%E5%B7%9E&package_name=com.hoge.android.app.fujian&appkey=OU4VuJgmGkqFzelCaueFLHll1sZJpOG4 HTTP/1.1
Accept-Language: zh-CN,zh;q=0.8
User-Agent: Dalvik/2.1.0 (Linux; U; Android 10; Pixel XL Build/QP1A.191005.007.A3) m2oSmartCity_468 1.0.0
X-API-VERSION: 4.0.0
X-API-SIGNATURE: ZDk3NWZiMTIzNzgxOTUzN2ZkYWQ0ZjBiMzc2OGZjZWI5YjQ3NTc0NQ==
X-API-KEY: 877a9ba7a98f75b90a9d49f53f15a858
X-API-TIMESTAMP: 1727335051221TrzPFY
X-AUTH-TYPE: sha1
Content-Type: application/x-www-form-urlencoded
Content-Length: 95
Host: mapi-plus.fjtv.net
Connection: Keep-Alive
Accept-Encoding: gzip
password=password777&client_id_android=34431799b51eaf57b3def0720642215b&member_name=15828712555
这里面有部分由于分析,删减了。
其实可以看到大部分都是固定的,我们直接去看看Sign的复现
关键代码定位
我们用objection自动化来HOOK一下,看看关键代码在哪
com.hoge.android.app.fujian on (google: 10) [usb] # android hooking watch class_method java.lang.String
.getBytes --dump-return --dump-args --dump-backtrace
(agent) Attempting to watch class java.lang.String and method getBytes.
(agent) Hooking java.lang.String.getBytes(int, int, [B, int)
(agent) Hooking java.lang.String.getBytes()
(agent) Hooking java.lang.String.getBytes(java.lang.String)
(agent) Hooking java.lang.String.getBytes(java.nio.charset.Charset)
(agent) Registering job 259388. Type: watch-method for: java.lang.String.getBytes
com.hoge.android.app.fujian on (google: 10) [usb] # (agent) [259388] Called java.lang.String.getBytes(java.nio.charset.Charset)
(agent) [259388] Backtrace:
java.lang.String.getBytes(Native Method)
java.lang.String.getBytes(String.java:914)
com.hoge.android.util.security.EncodeUtils.md5(EncodeUtils.java:249)
com.hoge.android.factory.util.Util.getDeviceToken(Util.java:529)
com.hoge.android.factory.util.DataRequestUtil.getHttpParams(DataRequestUtil.java:490)
com.hoge.android.factory.util.DataRequestUtil.getHttpParams(DataRequestUtil.java:472)
com.hoge.android.factory.util.ConfigureUtils.getUrl(ConfigureUtils.java:1210)
com.hoge.android.factory.util.ConfigureUtils.getUrl(ConfigureUtils.java:1182)
com.hoge.android.factory.model.LoginBiz.onLoginAction(LoginBiz.java:200)
com.hoge.android.factory.presenter.LoginPresenter.goLogin(LoginPresenter.java:66)
com.hoge.android.factory.CompLoginStyle1Activity.loginOfM2o(CompLoginStyle1Activity.java:339)
com.hoge.android.factory.LoginBaseActivity$1.onClick(LoginBaseActivity.java:161)
android.view.View.performClick(View.java:7140)
android.view.View.performClickInternal(View.java:7117)
android.view.View.access$3500(View.java:801)
android.view.View$PerformClick.run(View.java:27351)
android.os.Handler.handleCallback(Handler.java:883)
android.os.Handler.dispatchMessage(Handler.java:100)
android.os.Looper.loop(Looper.java:214)
android.app.ActivityThread.main(ActivityThread.java:7356)
java.lang.reflect.Method.invoke(Native Method)
com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
(agent) [259388] Arguments java.lang.String.getBytes(UTF-8)
(agent) [259388] Return Value: [object Object]
(agent) [259388] Called java.lang.String.getBytes()
(agent) [259388] Backtrace:
java.lang.String.getBytes(Native Method)
com.hoge.android.factory.util.Util.getRequestHeader(Util.java:1729)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:225)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:206)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:168)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:114)
com.hoge.android.factory.model.LoginBiz.onLoginAction(LoginBiz.java:208)
com.hoge.android.factory.presenter.LoginPresenter.goLogin(LoginPresenter.java:66)
com.hoge.android.factory.CompLoginStyle1Activity.loginOfM2o(CompLoginStyle1Activity.java:339)
com.hoge.android.factory.LoginBaseActivity$1.onClick(LoginBaseActivity.java:161)
android.view.View.performClick(View.java:7140)
android.view.View.performClickInternal(View.java:7117)
android.view.View.access$3500(View.java:801)
android.view.View$PerformClick.run(View.java:27351)
android.os.Handler.handleCallback(Handler.java:883)
android.os.Handler.dispatchMessage(Handler.java:100)
android.os.Looper.loop(Looper.java:214)
android.app.ActivityThread.main(ActivityThread.java:7356)
java.lang.reflect.Method.invoke(Native Method)
com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
(agent) [259388] Called java.lang.String.getBytes(java.nio.charset.Charset)
(agent) [259388] Backtrace:
java.lang.String.getBytes(Native Method)
java.lang.String.getBytes(String.java:978)
java.lang.String.getBytes(Native Method)
com.hoge.android.factory.util.Util.getRequestHeader(Util.java:1729)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:225)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:206)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:168)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:114)
com.hoge.android.factory.model.LoginBiz.onLoginAction(LoginBiz.java:208)
com.hoge.android.factory.presenter.LoginPresenter.goLogin(LoginPresenter.java:66)
com.hoge.android.factory.CompLoginStyle1Activity.loginOfM2o(CompLoginStyle1Activity.java:339)
com.hoge.android.factory.LoginBaseActivity$1.onClick(LoginBaseActivity.java:161)
android.view.View.performClick(View.java:7140)
android.view.View.performClickInternal(View.java:7117)
android.view.View.access$3500(View.java:801)
android.view.View$PerformClick.run(View.java:27351)
android.os.Handler.handleCallback(Handler.java:883)
android.os.Handler.dispatchMessage(Handler.java:100)
android.os.Looper.loop(Looper.java:214)
android.app.ActivityThread.main(ActivityThread.java:7356)
java.lang.reflect.Method.invoke(Native Method)
com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)objection -g <app:com.xiaojianbang.app> explorecom.hoge.android.app.fujian on (google: 10) [usb] # android hooking watch class_method java.lang.String
.getBytes --dump-return --dump-args --dump-backtrace
(agent) Attempting to watch class java.lang.String and method getBytes.
(agent) Hooking java.lang.String.getBytes(int, int, [B, int)
(agent) Hooking java.lang.String.getBytes()
(agent) Hooking java.lang.String.getBytes(java.lang.String)
(agent) Hooking java.lang.String.getBytes(java.nio.charset.Charset)
(agent) Registering job 259388. Type: watch-method for: java.lang.String.getBytes
com.hoge.android.app.fujian on (google: 10) [usb] # (agent) [259388] Called java.lang.String.getBytes(java.nio.charset.Charset)
(agent) [259388] Backtrace:
java.lang.String.getBytes(Native Method)
java.lang.String.getBytes(String.java:914)
com.hoge.android.util.security.EncodeUtils.md5(EncodeUtils.java:249)
com.hoge.android.factory.util.Util.getDeviceToken(Util.java:529)
com.hoge.android.factory.util.DataRequestUtil.getHttpParams(DataRequestUtil.java:490)
com.hoge.android.factory.util.DataRequestUtil.getHttpParams(DataRequestUtil.java:472)
com.hoge.android.factory.util.ConfigureUtils.getUrl(ConfigureUtils.java:1210)
com.hoge.android.factory.util.ConfigureUtils.getUrl(ConfigureUtils.java:1182)
com.hoge.android.factory.model.LoginBiz.onLoginAction(LoginBiz.java:200)
com.hoge.android.factory.presenter.LoginPresenter.goLogin(LoginPresenter.java:66)
com.hoge.android.factory.CompLoginStyle1Activity.loginOfM2o(CompLoginStyle1Activity.java:339)
com.hoge.android.factory.LoginBaseActivity$1.onClick(LoginBaseActivity.java:161)
android.view.View.performClick(View.java:7140)
android.view.View.performClickInternal(View.java:7117)
android.view.View.access$3500(View.java:801)
android.view.View$PerformClick.run(View.java:27351)
android.os.Handler.handleCallback(Handler.java:883)
android.os.Handler.dispatchMessage(Handler.java:100)
android.os.Looper.loop(Looper.java:214)
android.app.ActivityThread.main(ActivityThread.java:7356)
java.lang.reflect.Method.invoke(Native Method)
com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
(agent) [259388] Arguments java.lang.String.getBytes(UTF-8)
(agent) [259388] Return Value: [object Object]
(agent) [259388] Called java.lang.String.getBytes()
(agent) [259388] Backtrace:
java.lang.String.getBytes(Native Method)
com.hoge.android.factory.util.Util.getRequestHeader(Util.java:1729)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:225)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:206)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:168)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:114)
com.hoge.android.factory.model.LoginBiz.onLoginAction(LoginBiz.java:208)
com.hoge.android.factory.presenter.LoginPresenter.goLogin(LoginPresenter.java:66)
com.hoge.android.factory.CompLoginStyle1Activity.loginOfM2o(CompLoginStyle1Activity.java:339)
com.hoge.android.factory.LoginBaseActivity$1.onClick(LoginBaseActivity.java:161)
android.view.View.performClick(View.java:7140)
android.view.View.performClickInternal(View.java:7117)
android.view.View.access$3500(View.java:801)
android.view.View$PerformClick.run(View.java:27351)
android.os.Handler.handleCallback(Handler.java:883)
android.os.Handler.dispatchMessage(Handler.java:100)
android.os.Looper.loop(Looper.java:214)
android.app.ActivityThread.main(ActivityThread.java:7356)
java.lang.reflect.Method.invoke(Native Method)
com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
(agent) [259388] Called java.lang.String.getBytes(java.nio.charset.Charset)
(agent) [259388] Backtrace:
java.lang.String.getBytes(Native Method)
java.lang.String.getBytes(String.java:978)
java.lang.String.getBytes(Native Method)
com.hoge.android.factory.util.Util.getRequestHeader(Util.java:1729)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:225)
com.hoge.android.factory.util.DataRequestUtil.postWithProgress(DataRequestUtil.java:206)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:168)
com.hoge.android.factory.util.DataRequestUtil.post(DataRequestUtil.java:114)
com.hoge.android.factory.model.LoginBiz.onLoginAction(LoginBiz.java:208)
com.hoge.android.factory.presenter.LoginPresenter.goLogin(LoginPresenter.java:66)
com.hoge.android.factory.CompLoginStyle1Activity.loginOfM2o(CompLoginStyle1Activity.java:339)
com.hoge.android.factory.LoginBaseActivity$1.onClick(LoginBaseActivity.java:161)
android.view.View.performClick(View.java:7140)
android.view.View.performClickInternal(View.java:7117)
android.view.View.access$3500(View.java:801)
android.view.View$PerformClick.run(View.java:27351)-
android.os.Handler.handleCallback(Handler.java:883)
android.os.Handler.dispatchMessage(Handler.java:100)
android.os.Looper.loop(Looper.java:214)
android.app.ActivityThread.main(ActivityThread.java:7356)
java.lang.reflect.Method.invoke(Native Method)
com.android.internal.os.RuntimeInit$MethodAndArgsCaller.run(RuntimeInit.java:492)
com.android.internal.os.ZygoteInit.main(ZygoteInit.java:930)
还是很多堆栈信息的,最后我们定位到了com.hoge.android.factory.util.Util.getRequestHeader
这里的getRequestHeader在jadx中的反编译不明显,要去JEB里面看
public static Map getRequestHeader(Context arg10) {
String v10_6;
BaseApplication v10 = BaseApplication.getInstance();
HashMap v0 = new HashMap();
String version = Util.getVersionName(v10);
String random = SecurityUtil.getRandomData(6);
Object v3 = null;
try {
Class.forName("com.hoge.android.jni.Utils").newInstance().verify(v10);
v10_6 = Class.forName("com.hoge.android.jni.Utils").newInstance().signature(version, random);
goto label_53;
}
这里其实就可以看到signature里面传入了veriosn和random里面,看到了一下signture里面去
package com.hoge.android.jni;
import android.content.Context;
public class Utils {
public String version;
static {
System.loadLibrary("m2o_jni");
}
public Utils() {
this.version = "0.0.1";
}
public native String decode(String arg1) {
}
public native String signature(String arg1, String arg2) {
}
public native void verify(Context arg1) {
}
}
我们这里直接去HOOK这里JAVA层的signture
var Utils = Java.use("com.hoge.android.jni.Utils");
Utils.signature.implementation=function(a,b)
{
console.log("com.hoge.android.jni.Utils.signature args:"+a,b);
var result =this.signature(a,b);
console.log("result:"+result);
return result;
}
[Pixel XL::海博TV]-> com.hoge.android.jni.Utils.signature args:4.0.0 1727417638549s7oQ0G
result:d5161c2da8607e75168970df8849a151a04913d9
这里我们看到传入了,version和time
这里我们顺便把传入固定下来
function call_java()
{
Java.perform(function(){
var Utils = Java.use("com.hoge.android.jni.Utils");
var current_application = Java.use('android.app.ActivityThread').currentApplication();
var context = current_application.getApplicationContext();
// var arg0="com.mfw.roadbook.MainApplication@fd32da7";
var arg1="4.0.0";
var arg2="1727411395271StN4UY";
Utils.$new().signature(arg1,arg2);
});
}
SO层逆向
ida分析得:
int __fastcall signature(JNIEnv *a1, int a2, int a3)
{
const char *verison; // r7
const char *v6; // r0
const char *time; // r8
size_t v8; // r11
size_t v9; // r11
void *v10; // r0
char *v11; // r6
int v12; // r5
void *p; // [sp+1Ch] [bp-2Ch] BYREF
p = 0;
if ( !is_initialised )
exit(1);
verison = (*a1)->GetStringUTFChars(a1, a2, 0);
v6 = (*a1)->GetStringUTFChars(a1, a3, 0);
time = v6;
if ( verison )
{
if ( v6 && (v8 = strlen(verison), v9 = v8 + strlen(time), v10 = malloc(v9 + 80), (v11 = v10) != 0) )
{
memset(v10, 0, v9 + 80);
snprintf(
v11,
v9 + 80,
"%s&%s&%s&%s",
"877a9ba7a98f75b90a9d49f53f15a858",
"NjhhMDRiODE3N2JkYzllNWUxNmE4OWU2Nzc3YTdiNjY=",
verison,
time);
sha1_encode(v11, v9 + 79, &p);
if ( p )
v12 = ((*a1)->NewStringUTF)(a1);
else
v12 = 0;
}
else
{
v12 = 0;
v11 = 0;
}
(*a1)->ReleaseStringUTFChars(a1, a2, verison);
}
else
{
v12 = 0;
v11 = 0;
}
if ( time )
(*a1)->ReleaseStringUTFChars(a1, a3, time);
if ( v11 )
free(v11);
if ( p )
free(p);
return v12;
}
这里我们去HOOK代码
sha1_encode(v11, v9 + 79, &p);
var moduleBase = Module.findBaseAddress("libm2o_jni.so");
if (moduleBase !== null)
{;;//32位程序要++1
var sha1 = moduleBase.add(0xA86C+1);
Interceptor.attach(sha1,{
onEnter:function(args){
console.log(args[0].readCString());
this.args2=args[2];
},
onLeave:function(result){
console.log(hexdump(this.args2.readPointer()));
}
});
} else {
console.log("Module not found: libencryptlib.so");
}
这里为什么我们要console.log(hexdump(this.args2.readPointer())),其实是因为这里是二级指针,hexdump的结果需要是指针
[Pixel XL::海博TV]-> call_java()
com.hoge.android.jni.Utils.signature args:4.0.0 1727411395271StN4UY
877a9ba7a98f75b90a9d49f53f15a858&NjhhMDRiODE3N2JkYzllNWUxNmE4OWU2Nzc3YTdiNjY=&4.0.0&1727411395271StN4UY
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
e05b4ad0 36 33 35 65 39 30 31 31 63 62 39 61 64 37 61 35 635e9011cb9ad7a5
e05b4ae0 38 63 36 65 32 37 34 30 32 30 62 31 33 33 35 33 8c6e274020b13353
e05b4af0 33 30 33 63 36 36 37 65 00 00 78 00 74 00 00 00 303c667e..x.t...
e05b4b00 42 69 6e 64 65 72 3a 38 39 35 34 5f 32 00 20 77 Binder:8954_2. w
e05b4b10 69 74 68 6f 75 74 20 6d 61 6e 61 67 65 64 20 70 ithout managed p
e05b4b20 65 65 72 3e 00 00 00 00 00 00 00 00 00 00 00 00 eer>............
e05b4b30 61 00 6e 00 64 00 72 00 6f 00 69 00 64 00 2e 00 a.n.d.r.o.i.d...
e05b4b40 6f 00 73 00 2e 00 49 00 4d 00 65 00 73 00 73 00 o.s...I.M.e.s.s.
e05b4b50 65 00 6e 00 67 00 65 00 72 00 00 00 00 00 00 00 e.n.g.e.r.......
e05b4b60 50 ed 12 eb 01 00 00 00 30 02 ac c9 00 00 00 00 P.......0.......
e05b4b70 02 00 00 00 00 00 00 00 00 01 65 e0 00 00 00 00 ..........e.....
e05b4b80 16 23 00 00 00 93 65 e0 84 ed 12 eb 70 0c 68 e0 .#....e.....p.h.
e05b4b90 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
e05b4ba0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
e05b4bb0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
e05b4bc0 2f 64 61 74 61 2f 75 73 65 72 2f 30 2f 63 6f 6d /data/user/0/com
result:635e9011cb9ad7a58c6e274020b13353303c667e
这里就可以看到,加密是SHA1,标准的SHA1
call ————>libm2o_jni.so!0xa86d
,this.args0 onEnter: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
ebc2a9d0 38 37 37 61 39 62 61 37 61 39 38 66 37 35 62 39 877a9ba7a98f75b9
ebc2a9e0 30 61 39 64 34 39 66 35 33 66 31 35 61 38 35 38 0a9d49f53f15a858
ebc2a9f0 26 4e 6a 68 68 4d 44 52 69 4f 44 45 33 4e 32 4a &NjhhMDRiODE3N2J
ebc2aa00 6b 59 7a 6c 6c 4e 57 55 78 4e 6d 45 34 4f 57 55 kYzllNWUxNmE4OWU
ebc2aa10 32 4e 7a 63 33 59 54 64 69 4e 6a 59 3d 26 34 2e 2Nzc3YTdiNjY=&4.
ebc2aa20 30 2e 30 26 31 37 32 37 34 31 31 33 39 35 32 37 0.0&172741139527
ebc2aa30 31 53 74 4e 34 55 59 00 00 00 00 00 00 00 00 00 1StN4UY.........
ebc2aa40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aa50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aa60 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aa70 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aa80 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aa90 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aaa0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aab0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
ebc2aac0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
这里传入的参数其实是字符串拼接的结果,包含了传入的verison和time